New Python Variant of Chaes Malware Targets Banking and Logistics Industries
Banking and logistics industries are under the onslaught of a reworked variant of a malware called Chaes.
“It has undergone major overhauls: from being rewritten entirely in Python, which resulted in lower detection rates by traditional defense systems, to a comprehensive redesign and an enhanced communication protocol,” Morphisec said in a new detailed technical write-up shared with The Hacker News.
Chaes, which first emerged in 2020, is known to target e-commerce customers in Latin America, particularly Brazil, to steal sensitive financial information.
A subsequent analysis from Avast in early 2022 found that the threat actors behind the operation, who call themselves Lucifer, had breached more than 800 WordPress websites to deliver Chaes to users of Banco do Brasil, Loja Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago.
Further updates were detected in December 2022, when Brazilian cybersecurity company Tempest Security Intelligence uncovered the malware’s use of Windows Management Instrumentation (WMI) in its infection chain to facilitate the collection of system metadata, such as BIOS, processor, disk size, and memory information.

The latest iteration of the malware, dubbed Chae$ 4 in reference to debug log messages present in the source code, packs in “significant transformations and enhancements,” including an expanded catalog of services targeted for credential theft as well as clipper functionalities.
Despite the changes in the malware architecture, the overall delivery mechanism has remained the same in attacks that were identified in January 2023.
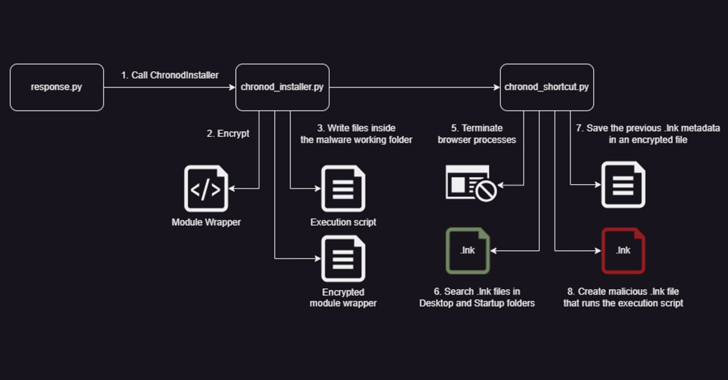
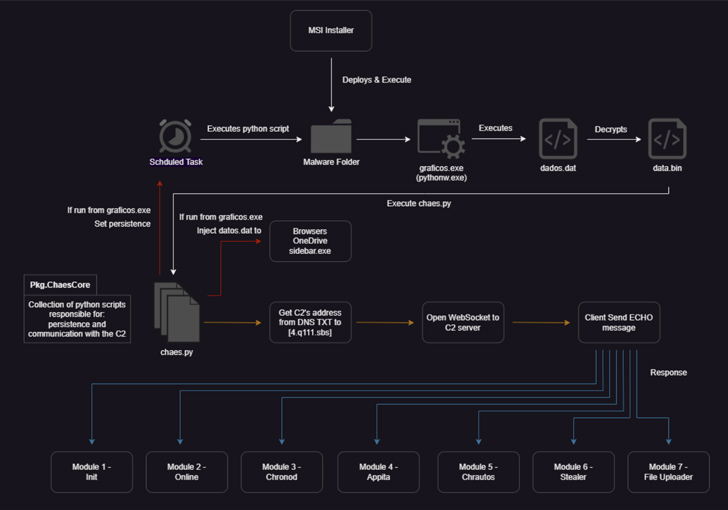
Potential victims landing on one of the compromised websites are greeted by a pop-up message asking them to download an installer for Java Runtime or an antivirus solution, triggering the deployment of a malicious MSI file that, in turn, launches a primary orchestrator module known as ChaesCore.
The component is responsible for establishing a communication channel with the command-and-control (C2) server from where it fetches additional modules that support post-compromise activity and data theft –
- Init, which gathers extensive information about the system
- Online, which…

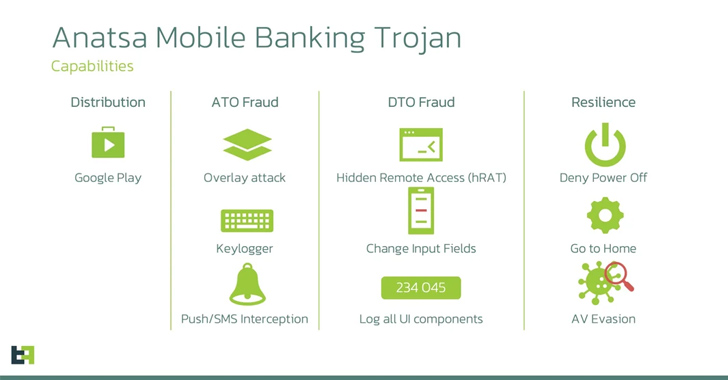
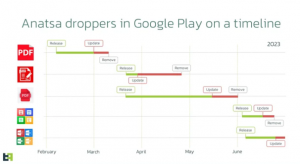 The new app was reported to Google again and removed, but in the ultimate game of Whac-A-Mole, every time the apps were removed, new apps appeared. The researchers note that the speed at which the actors return with a new dropper after the previous one is removed is notable in itself, given that the coding can take anywhere from a few days and several weeks.
The new app was reported to Google again and removed, but in the ultimate game of Whac-A-Mole, every time the apps were removed, new apps appeared. The researchers note that the speed at which the actors return with a new dropper after the previous one is removed is notable in itself, given that the coding can take anywhere from a few days and several weeks.