Tag Archive for: Basics
Hacking the World – Part 1: Hacking Basics
/in Internet Security

Each week in October, as part of Cybersecurity Awareness Month, we’ll publish an article packed with facts and stats, to give you an in-depth look at the state of cybersecurity in today’s world. We’ll start with the basics, then cover vulnerabilities, risks, costs – and so much more.
Cybersecurity is in focus now more than ever before – and 2020 was a record year for hacking activity. Companies faced swathes of sophisticated attacks during the initial throes of the COVID-19 pandemic and this trend has continued into 2021.
We’ll tell you everything you need to know about the scale, cost, and geography of hacking attacks and data breaches, not to mention stats on the biggest threats, vulnerabilities, and risk areas over the last 12 months.
We’ll even cover the future of cybersecurity and some tips to stay safe. But first, let’s take a look at the key definitions. Jump to a section below, or read on:
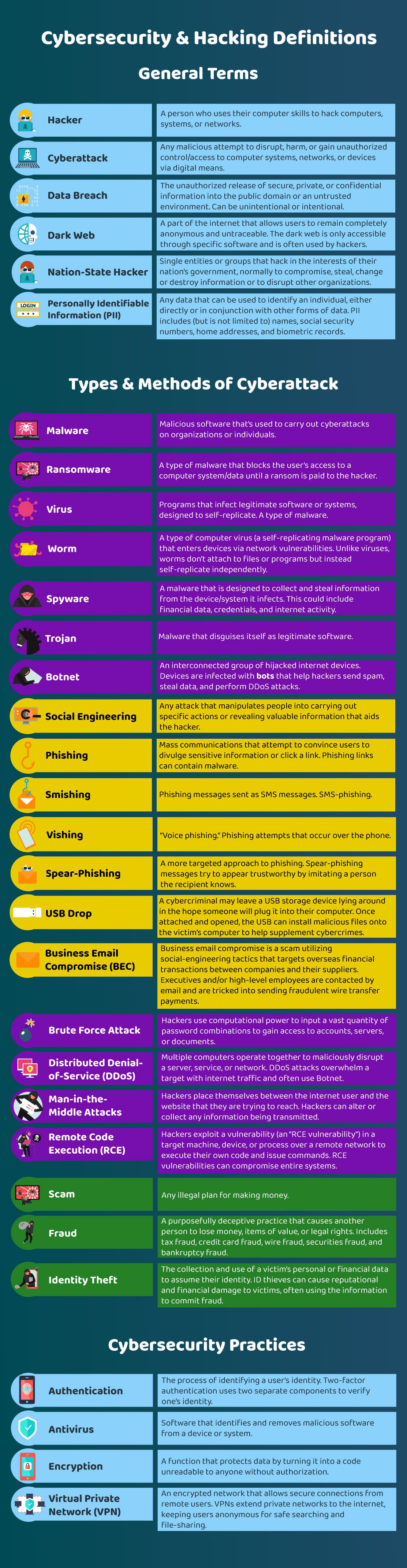
Cybersecurity Glossary
General Statistics
Hacking 101
Cybersecurity Glossary
Digital rights refer to those rights that allow individua
Cybersecurity is a complicated subject with its fair share of technical jargon. Before we get into our long list of cybersecurity/hacking stats, let us first go over some key definitions.
This should help us avoid any confusion.
As you probably already know, cybersecurity is the protection of device users/contents against unauthorized electronic data and bad actors. Cybersecurity also outlines the measures taken to achieve this protection.
Hacking is the process of gaining unauthorized access to a system or device’s data. There are a ton of other cybersecurity and hacking-related definitions. Here are some important ones.
Now we’ll dive into the world of hacking and cybersecurity statistics…
General Statistics
Here are a few general stats to get you acquainted with cybersecurity and hacking: History, target data, and the current state of hacking breaches.
The History of Hacking

Hacking is almost as old as the very first computer network. That’s right, as long as computers have been around, people have been busy trying to figure out how best to exploit them.
Bob Thomas of BBM wrote the creeper — an experimental program…
To stop the ransomware pandemic, start with the basics
/in Internet Security
TWENTY YEARS ago, it might have been the plot of a trashy airport thriller. These days, it is routine. On May 7th cyber-criminals shut down the pipeline supplying almost half the oil to America’s east coast for five days. To get it flowing again, they demanded a $4.3m ransom from Colonial Pipeline Company, the owner. Days later, a similar “ransomware” assault crippled most hospitals in Ireland.
Enjoy more audio and podcasts on iOS or Android.
Such attacks are evidence of an epoch of intensifying cyber-insecurity that will impinge on everyone, from tech firms to schools and armies. One threat is catastrophe: think of an air-traffic-control system or a nuclear-power plant failing. But another is harder to spot, as cybercrime impedes the digitisation of many industries, hampering a revolution that promises to raise living standards around the world.
The first attempt at ransomware was made in 1989, with a virus spread via floppy disks. Cybercrime is getting worse as more devices are connected to networks and as geopolitics becomes less stable. The West is at odds with Russia and China and several autocracies give sanctuary to cyber-bandits.
Trillions of dollars are at stake. Most people have a vague sense of narrowly avoided fiascos: from the Sony Pictures attack that roiled Hollywood in 2014, to Equifax in 2017, when the details of 147m people were stolen. The big hacks are a familiar but confusing blur: remember SoBig, or SolarWinds, or WannaCry?
A forthcoming study from London Business School (LBS) captures the trends by examining comments made to investors by 12,000 listed firms in 85 countries over two decades. Cyber-risk has more than quadrupled since 2002 and tripled since 2013. The pattern of activity has become more global and has affected a broader range of industries. Workers logging in from home during the pandemic have almost certainly added to the risks. The number of affected firms is at a record high.
Faced with this picture, it is natural to worry most about spectacular crises caused by cyber-attacks. All countries have vulnerable physical nodes such as oil pipelines, power plants and…
EV battery basics: All you need to know about kW, kWh, and charging speed – The Next Web
/in Computer SecurityEV battery basics: All you need to know about kW, kWh, and charging speed The Next Web
“Don’t Plug Your Phone into a Charger You Don’t Own” – read more