39% of all internet traffic is from bad bots
Automated traffic takes up 64% of internet traffic – and whilst just 25% of automated traffic was made up by good bots, such as search engine crawlers and social network bots, 39% of all traffic was from bad bots, a Barracuda report reveals.
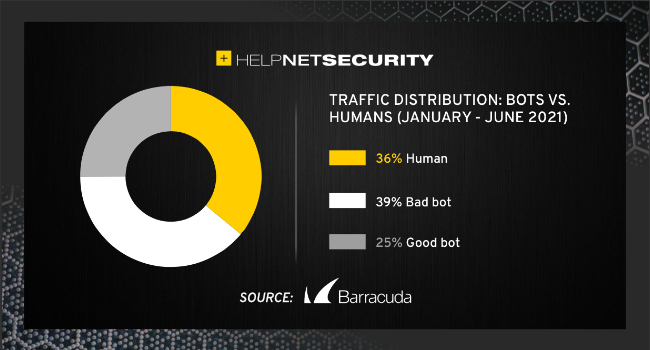
These bad bots include both basic web scrapers and attack scripts, as well as advanced persistent bots. These advanced bots try their best to evade standard defences and attempt to perform their malicious activities under the radar. The report revealed that the most common of these persistent bots were ones that went after e-commerce applications and login portals.
Bad bots internet traffic by location
The report also included a breakdown of bad bot traffic by location. It revealed that North America accounts for 67% of bad bot traffic, followed by Europe (22%) and then Asia (7.5%).
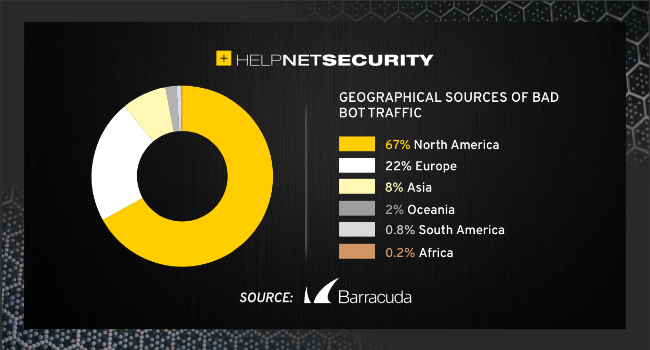
Interestingly, the European bot traffic was more likely to come in from hosting services (VPS) or residential IPs than the North American traffic, most of which originated from public data centres.
Most bot traffic comes in from AWS and Microsoft Azure
The research also revealed that most bot traffic comes in from the two largest public cloud vendors, AWS and Microsoft Azure, in roughly equal measure. This is likely because it is easy to set up a free account with either provider, and then use the account to set up the bad bots.
Finally, researchers observed that bad bot traffic tends to follow the standard workday, allowing them to hide within normal human traffic streams to avoid raising alarm bells.
Nitzan Miron, VP of Product Management, Application Security, Barracuda said: “While some bots like search engine crawlers are good, our research shows that over 60% of bots are dedicated to carrying out malicious activities at scale. When left unchecked, these bad bots can steal data, affect site performance, and even lead to a breach. That’s why it’s critically important to detect and effectively block bot traffic.”





