XPhase Clipper Malware Campaign Targets Crypto Users
A new strain of malware dubbed XPhase Clipper has been stealthily targeting cryptocurrency users. This Clipper malware infiltrates unsuspecting victims’ systems through deceptive websites masquerading as authentic cryptocurrency platforms.
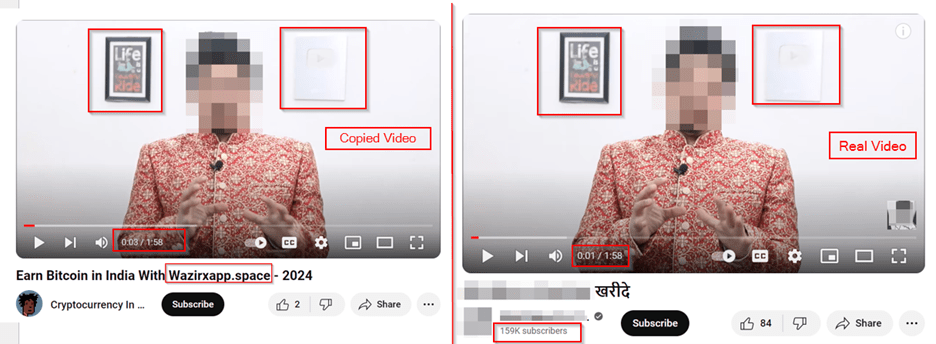
Cybersecurity experts at Cyble Research and Intelligence Labs (CRIL) have found this concerning trend where a large-scale operation is using cloned YouTube videos to target unsuspecting victims on the internet.
This is a churned-down version of the report, shedding light on its modus operandi and the infection chain of XPhase Clipper malware.
Understanding the XPhase Clipper Malware Campaign
Clipper malware poses a serious threat to cryptocurrency users by pilfering sensitive information, particularly cryptocurrency wallet addresses, from the clipboard.
With the increasing popularity of cryptocurrencies like Bitcoin and Ethereum, cybercriminals are increasingly exploiting users to abscond with their funds.
XPhase Clipper represents a sophisticated iteration of this malware strain, designed to intercept and manipulate copied cryptocurrency wallet addresses, rerouting funds to the attackers’ accounts.
The threat actors behind the XPhase Clipper malware campaign are exclusively targeting cryptocurrency users worldwide, deploying a series of deceptive tactics to ensnare victims.

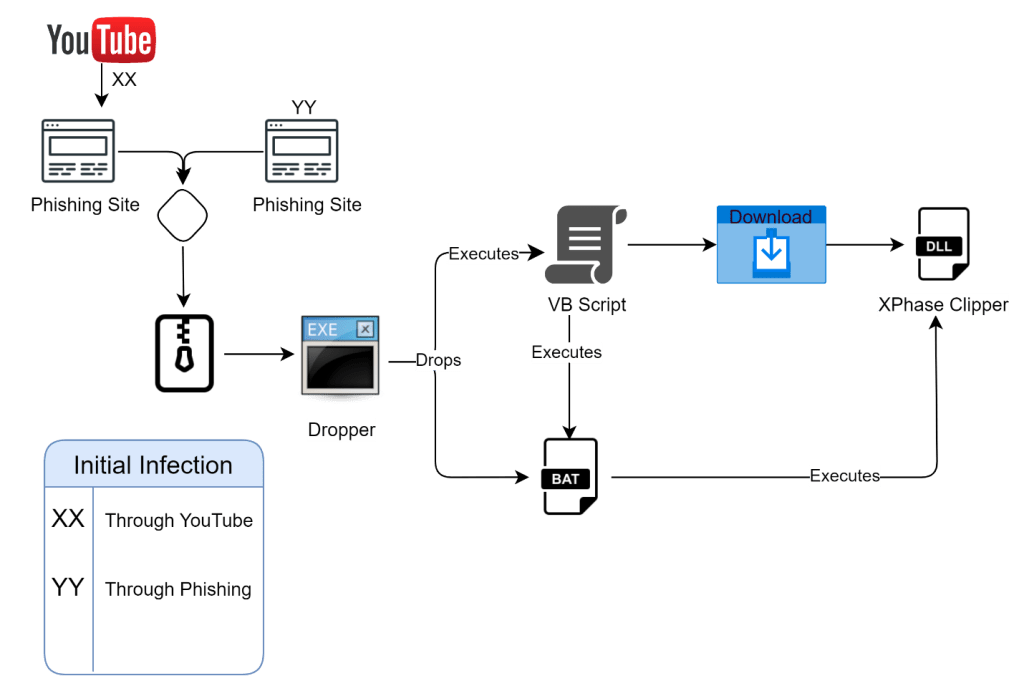
Notably, phishing sites impersonating reputable platforms such as Metamask and Wazirx have emerged as conduits for spreading the XPhase Clipper payload.

These malicious sites lure users into downloading a zip file housing an array of malicious components, including a dropper executable, VB Script, and Batch script files, culminating in the execution of the clipper payload in the form of a DLL file.
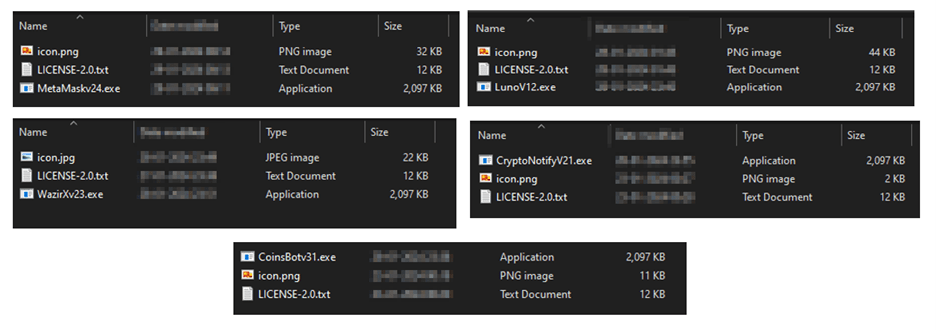
XPhase Clipper Malware Targets Indian Crypto Users
Upon closer examination, CRIL found that the infection chain is meticulously orchestrated, with each stage serving to conceal the malicious activities of the XPhase Clipper.
The VB Script plays an important role in facilitating the download and execution of the clipper payload, while the Batch script ensures persistence by adding a registry…