How to Move WhatsApp Chats to Android, iPhone, Signal, and Telegram
Since early 2016, WhatsApp has protected messages and conversations sent in its app with end-to-end encryption. This means that nobody other than the sender and receiver of messages can read their content—not even Meta can read or snoop on the contents of your conversations.
Despite WhatsApp being omnipresent—more than 2 billion people use it each month—securely moving your encrypted chats and photos to different platforms or apps has been a challenge. Transferring your WhatsApp chats from Android to iPhone and from iPhone to Android has historically only been possible using third-party apps. These apps are often fiddly and don’t necessarily protect your data at the level offered by WhatsApp’s ecosystem.
But in recent months WhatsApp has made it possible to officially switch between iPhones and Android (and vice versa), rolling out processes to securely move data between operating systems and working with phone manufacturers to enable the move.
If you’re fed up with Meta’s ecosystem, it’s also possible to move your groups and some chat data to other messaging apps. Here’s how to move all of your WhatsApp chats and backups.
Android to iPhone
Moving your WhatsApp account from Android to an iPhone involves a few steps. But it should be possible to bring most of your information with you: Your profile photo, individual and group chats, history, photos, videos, and settings can all make the jump from one device to another. Your call history and display name can’t be moved across, however, WhatsApp says.
Most of the work in moving your WhatsApp data comes before you make the shift. To move between devices, you need to ensure you have the same phone number on each. Before you start the process, make sure you have a recently updated version of WhatsApp on your Android phone. You also need to be running at least Android 5 on the device you’re moving from and iOS 15.5 on the iPhone you’re moving to. (The iPhone needs to be a new device or have been recently reset to its factory settings.)
Next, download and install the “Move to iOS” app from Google’s Play Store—this Apple-owned app will do all the heavy lifting. When you’re ready to migrate your data, plug both…






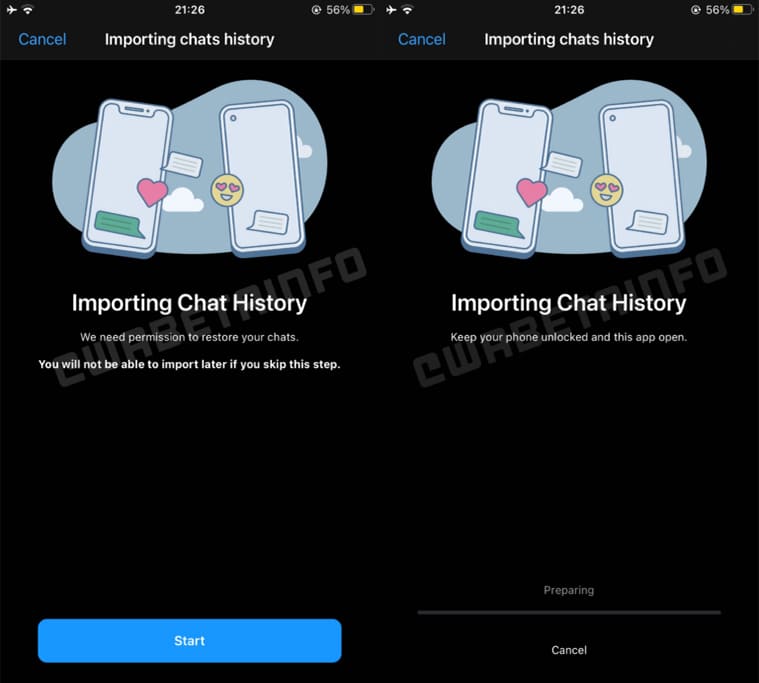 WhatsApp chat transfer prompt. (Image credit: WABetaInfo)
WhatsApp chat transfer prompt. (Image credit: WABetaInfo)