Top VAPT Testing Companies – Security Boulevard
By reducing information risks and vulnerabilities, a process called information security, also referred to as infosec, protects electronic data. Data collection, organization, processing, and deletion are all included in the definition of data management. Data can be stored in text, picture, or video file formats on servers, desktop computers, laptops, or mobile devices. InfoSec measures must be put in place by any organization that deals with sensitive or confidential data.VAPT (Vulnerability Assessment and Penetration Testing) is useful in this situation. The use of VAPT services can help ensure that the security measures put in place for one’s computer systems, network systems, and data are appropriate and up to par. They offer a viewpoint that aids in the analysis of any security flaws and failures. By doing this, you can lessen the impact of any undesirable acts hackers take.
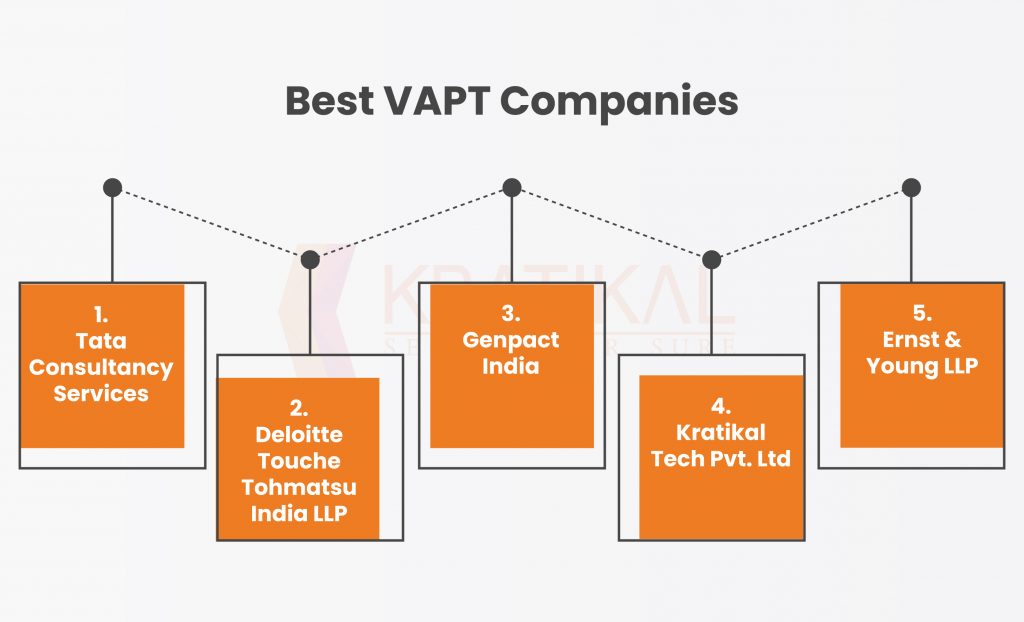
In this Blog, we will mainly address what VAPT is, and why Vulnerability Assessment and Penetration Testing Services are Important in the Cyberworld. Along with advice on how to choose the right course of action for your security, the best VAPT companies in India will also be covered in detail.
What is VAPT?
The procedure of evaluating and identifying vulnerabilities within a system is known as vulnerability assessment and penetration testing, or VAPT. Testing is done to determine whether or not these vulnerabilities can be exploited after they have been discovered and identified. In order to mitigate these risks, appropriate measures must be taken if they can be exploited. In addition to network VAPT, web application VAPT, and mobile application VAPT, there are many other uses for VAPT services.
A vulnerability report is submitted after a thorough review of the auditee organization’s systems and procedures are carried out by an expert panel from any certified company as part of the vulnerability assessment process. While in penetration testing, the VAPT testing businesses use these defects and flaws to find out how far a con artist may go in abusing such vulnerabilities. The defending tactics are to be evaluated.
Why VAT considered to be Important?
Vulnerabilities exist in the IT infrastructure…