Stealthy HeadCrab Malware Compromised Over 1,200 Redis Servers
At least 1,200 Redis database servers worldwide have been corralled into a botnet using an “elusive and severe threat” dubbed HeadCrab since early September 2021.
“This advanced threat actor utilizes a state-of-the-art, custom-made malware that is undetectable by agentless and traditional anti-virus solutions to compromise a large number of Redis servers,” Aqua security researcher Asaf Eitani said in a Wednesday report.
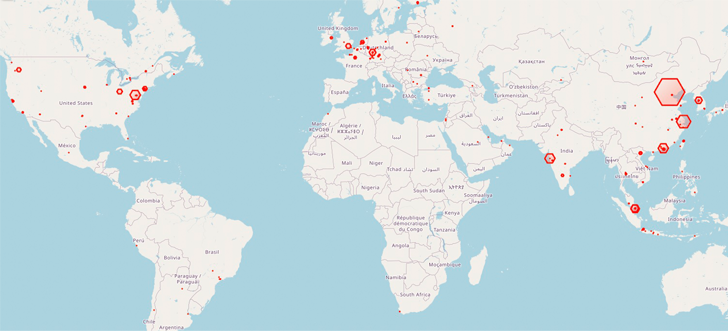
A significant concentration of infections has been recorded in China, Malaysia, India, Germany, the U.K., and the U.S. to date. The origins of the threat actor are presently unknown.
The findings come two months after the cloud security firm shed light on a Go-based malware codenamed Redigo that has been found compromising Redis servers.
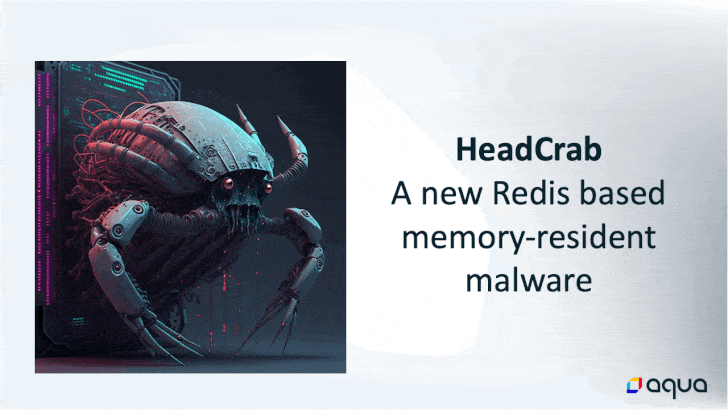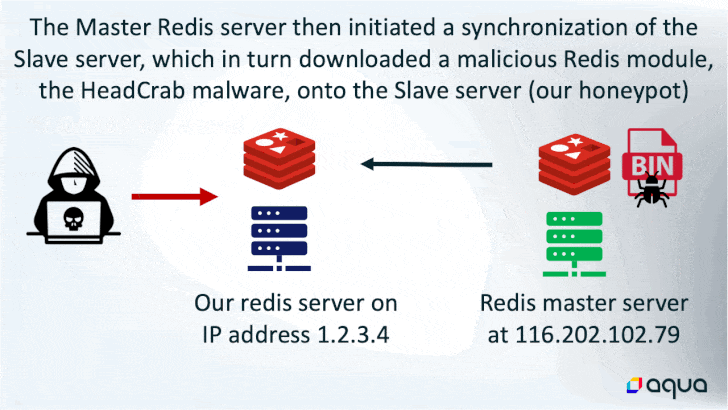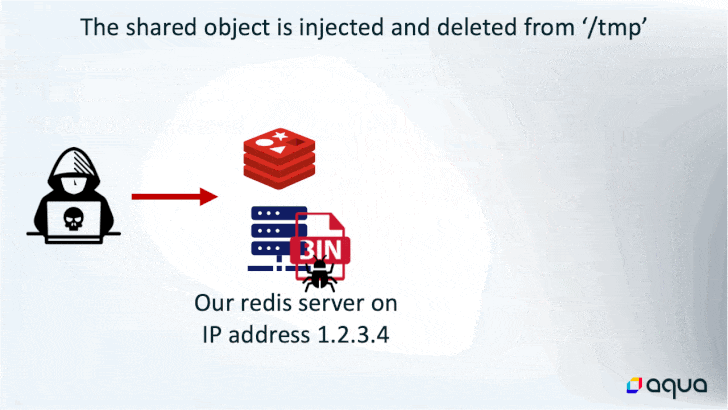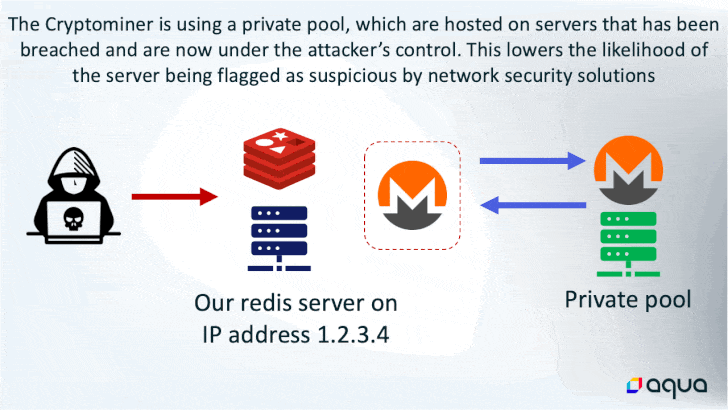
The attack is designed to target Redis servers that are exposed to the internet, followed by issuing a SLAVEOF command from another Redis server that’s already under the adversary’s control.
In doing so, the rogue “master” server initiates a synchronization of the newly hacked server to download the malicious payload, which contains the sophisticated HeadCrab malware.
“The attacker seems to mainly target Redis servers and has a deep understanding and expertise in Redis modules and APIs as demonstrated by the malware,” Eitani noted.
While the ultimate end goal of using the memory-resident malware is to hijack the system resources for cryptocurrency mining, it also boasts of numerous other options that allows the threat actor to execute shell commands, load fileless kernel modules, and exfiltrate data to a remote server.
What’s more, a follow-on analysis of the Redigo malware has revealed it to be weaponizing the same master-slave technique for proliferation, and not the Lua sandbox escape flaw (CVE-2022-0543) as previously disclosed.
Users are recommended to refrain from exposing Redis servers directly to the internet, disable the “SLAVEOF” feature in their environments if not in use, and configure the servers to only accept connections from trusted hosts.
Eitani said “HeadCrab will persist in using cutting-edge techniques to penetrate servers, either through…