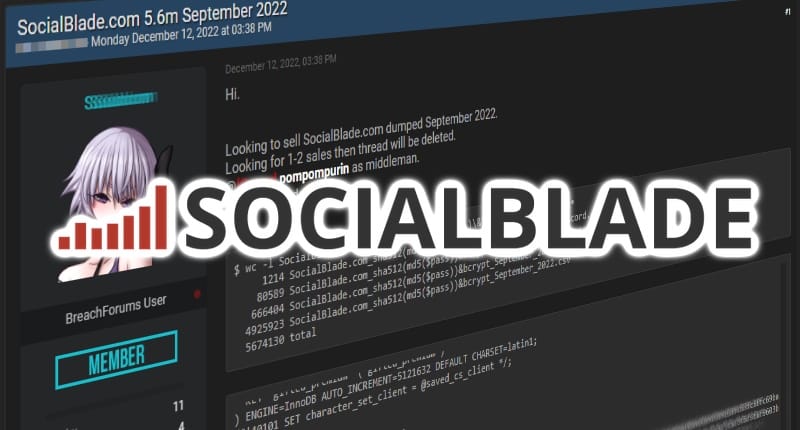
Data breach at Social Blade confirmed. Hacker offers to sell database on underground website
Social media analytics service Social Blade has confirmed that it is investigating a security breach after a hacker offered its user database for sale on an underground criminal website.
In a notification sent to Social Blade users, the firm said that it had confirmed that its database was being offered for sale on a hacking forum after being notified of a potential breach on December 14th.
According to Bleeping Computer, Social Blade’s data was first put on sale on the underground forum on December 12, 2022.
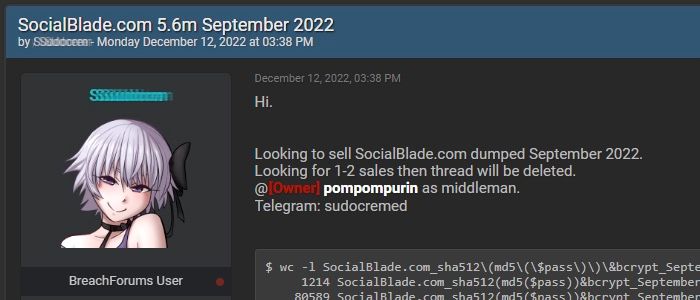
The hacker, meanwhile, claims to have stolen the database of 5.6 million records in September.
Social Blade, which monitors the social media accounts of tens of millions of users, issued a reassurance that no credit card information had been leaked, but did say that the leaked data included email addresses, IP addresses, password hashes, client IDs and tokens for business API users, auth tokens for connected accounts, and “many other pieces of non-personal and internal data.”
In addition, the firm warned that “a very small subset of the data (about a tenth of a percent)”” also included the addresses of users.
Social Blade went on to say that although password hashes had been leaked, it did not believe they were at risk as the strong bcrypt encryption algorithm had been used. Nonetheless, it would be sensible for affected Social Blade users to change their passwords, ensuring that new passwords are hard-to-crack or guess, and are unique.
Business API tokens have meanwhile been reset to prevent exploitation by unauthorised third parties.
Social Blade believes that the individual who stole its data accessed it by exploiting a website vulnerability. It says it has closed the security hole and is conducting additional reviews of its systems to ensure that security is further hardened.
Anyone who has used Social Blade would be wise to not only change their password but also to be on the lookout for scams and phishing attacks which attempt to use the breached information to trick the unwary into handing over further details.