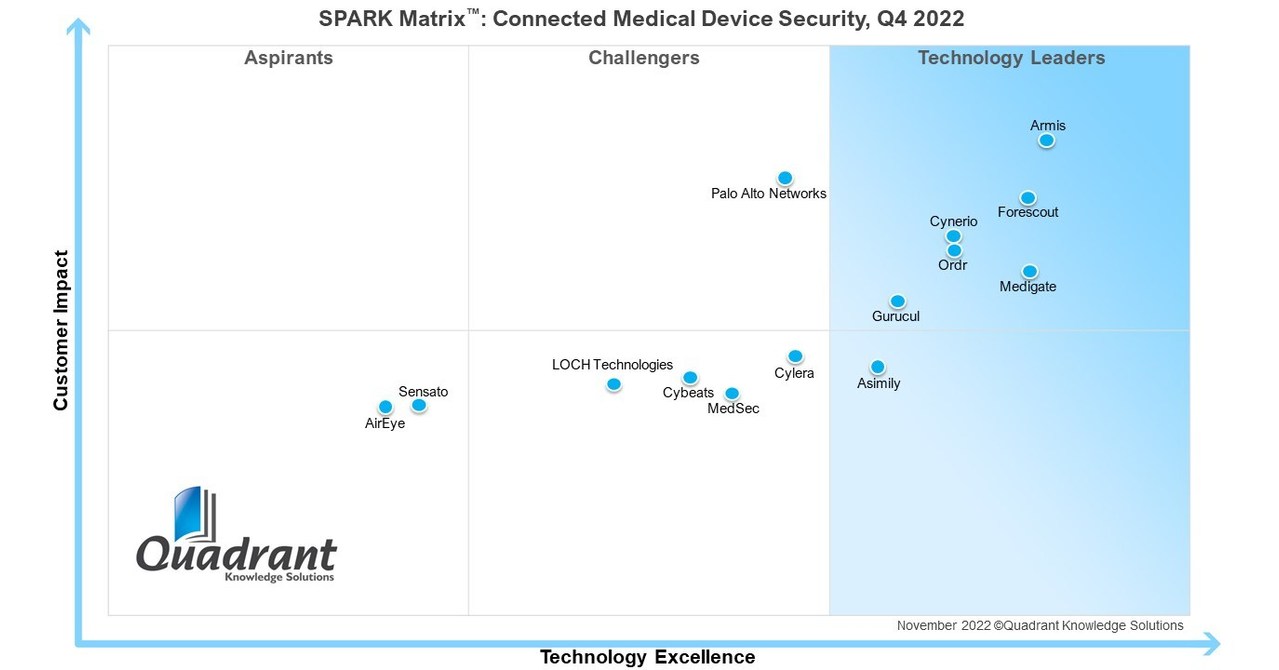
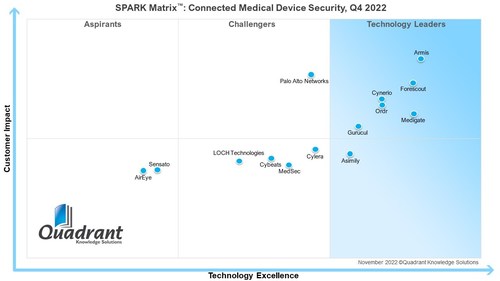
Cyber Security Essentials: Safeguarding Your Digital Life In An Increasingly Connected World
Welcome to the digital age, where everything from our personal lives to global commerce relies on technology. As we revel in the convenience and endless possibilities it offers, we must also face a sobering reality – the ever-growing threat of cybercrime. With each passing day, hackers are becoming savvier and more relentless, posing serious risks to our digital lives. In this blog post, we will delve into cyber security essentials – an indispensable guide to fortify your online defenses in an increasingly connected world. Whether you’re a tech enthusiast or just starting out on your digital journey, join us as we navigate through the complexities of safeguarding your valuable data and ensuring peace of mind in this rapidly evolving cyber landscape.
What is Cyber Security?
Cybersecurity is the practice of protecting information systems from cyberattacks. Cyberattacks can take many forms, including:
-Spyware and malware: Private data such as e-mails, bank account numbers, and passwords can be stolen by spyware or malware. Spyware and malware can also monitor user activity and gather sensitive information.
-Data breaches: In a data breach, hackers access personal data belonging to either individuals or organizations. This can include name, address, e-mail addresses, and Social Security numbers. Data breaches can also result in the release of confidential information.
-Criminals exploiting online security vulnerabilities: Criminals could exploit online security vulnerabilities to gain unauthorized access to a system or to steal confidential information.
What are the threats to your digital life?
In an increasingly interconnected and digital world, cyber security is more important than ever. Here are five of the most common threats to digital life and how to safeguard yourself against them:
1. Hackers: Hackers can steal your personal information, passwords, and other confidential information. To protect yourself from hackers, make sure you keep…