GoldDigger Disguises as Fake Android App To Steal Banking Credentials
GoldDigger, a new Android Trojan, imitates a fraudulent Android application and has been discovered to spoof both a Vietnamese government portal and a local energy provider.
Since at least June 2023, this specific Trojan has been active. Stealing banking credentials is its major objective.
It takes advantage of the Accessibility Service to steal personal data, intercept SMS traffic, and carry out other tasks for the user. The Trojan may be accessed remotely as well.
Researchers from Group-IB’s Threat Intelligence team discovered this Android Trojan targeting Vietnamese financial institutions. Three Android Trojans, including GoldDigger, are now operating in the Asia Pacific.
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware
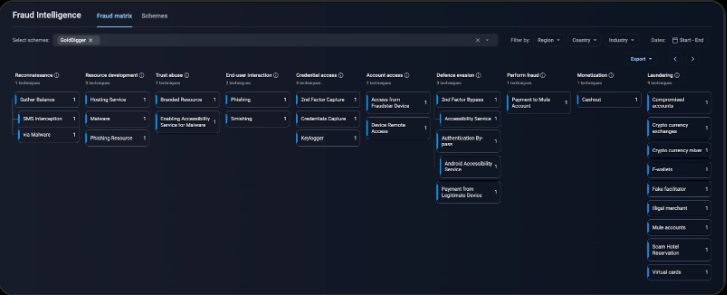
Tactics Of The GoldDigger Trojan
Implementing a sophisticated protection system is one of GoldDigger’s key characteristics. The Trojan can greatly restrict static and dynamic malware analysis and elude detection due to Virbox Protector, a powerful protection solution for applications.
Banking Trojans’ primary objective is to infect as many devices as they can and access user accounts.
The “Install from Unknown Sources” feature is disabled by default on all Android devices, preventing the installation of apps from unofficial sources. APKs can be installed from sources other than the Google Play Store if the “Install from Unknown Sources” feature is enabled.
To download and install GoldDigger, the “Install from Unknown Sources” feature must be turned on on the victim’s device.
The GoldDigger Trojan prompts the user to enable Accessibility Service when it is run. The accessibility features offered by Android are designed to make using mobile devices easier for people with impairments.
These services include speech-to-text,…



