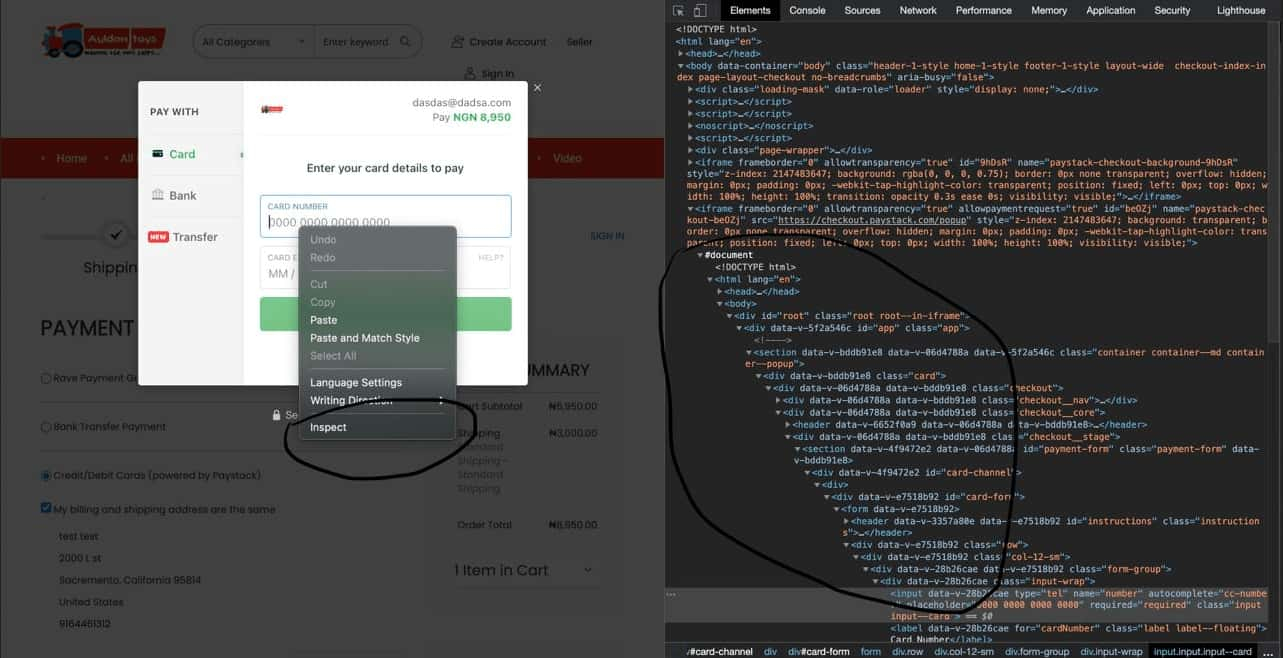
Hacking Tools, Stolen Credit Cards Advertised on Facebook Groups
(Bloomberg) — One user offered hacking services, both ethical and not. Another claimed to be able to change school grades. And several others peddled stolen credit cards and IDs.
Such illegal products and services have long been offered on the dark web, a murky section of the internet that’s populated with illicit forums. But these offers were being made on Facebook, despite repeated efforts by the social media giant to curb illegal behavior on its site.
A Bloomberg News analysis found more than 45 groups and pages — with more than 1 million combined members — where the spoils of cyber crimes and the tools needed to carry them out were offered for sale. Some of the sites were revealed by Facebook’s own discovery mechanism, which recommends groups based on those who have already joined, but Bloomberg discovered others through keyword searches and referrals from other groups.
Among the most common were hacking-for-hire services, with 11 of the groups and pages specifically dedicated to facilitating the practice, including three with more than 100,000 members. Those groups averaged between 12,000 and 18,000 posts per month, according to data from the Facebook-owned analytics platform CrowdTangle. One tool, listed on a group called Hacker Hub, promises to deliver credentials for popular social media sites and victims’ financial information.
Alexander Leslie, a researcher at the threat intelligence firm Recorded Future Inc., said the volume of illicit offers on Facebook “way, way overshadows what we see on the dark web in other forums that deal with similar content.”
While hardly definitive given Facebook’s massive size, the Bloomberg analysis indicates the social media platform’s efforts to stop illicit behavior haven’t kept pace. The company now known as Meta Platforms Inc. removed the content in question when reached by Bloomberg News.
“We take significant steps to stop criminal activity on our platforms and have removed this content,” a spokesperson said via email. “We invest heavily in technology to tackle illegal content and we encourage people to report activity like this to us and the police, so we can take action.”
Since its earliest…