What We Know About San Diego Scripps Health Cyberattack – NBC 7 San Diego
What to Know
- The California Department of Public health calls the cyberattack “ransomware attacks”
- Scripps did not provide any information on how the cyberattack occurred but later determined that the outage was due to a security incident involving malware on its computer networks
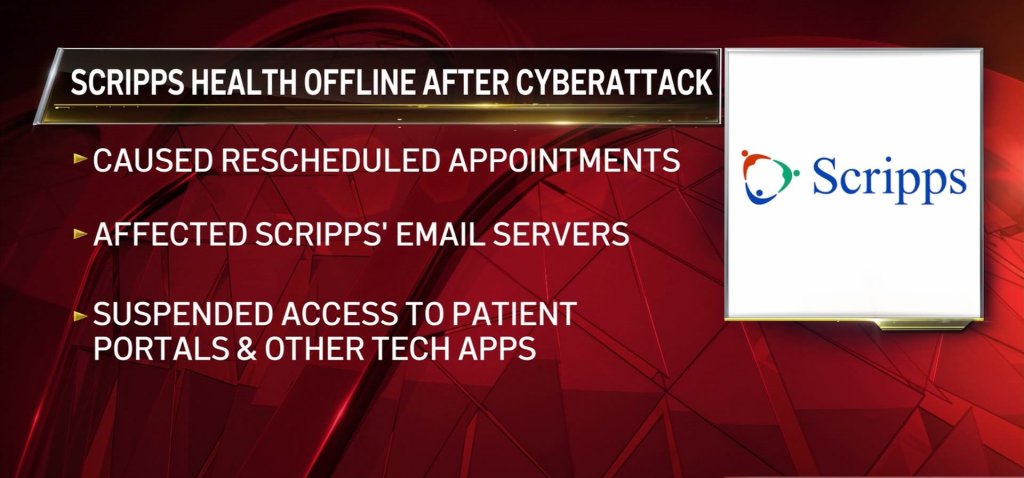
- The cyberattack caused rescheduled appointments, affected Scripps email servers, and suspended access to patient portals and other tech applications
One of San Diego’s main health care systems, Scripps Health, had its technology servers hacked on May 1 in what has been deemed a ransomware attack by the California Department of Public Health (CDPH).
And, although the incident has disrupted access to patient information, affected the ability of health care workers to do their jobs and led to a lack of communication with patients, Scripps Health has provided little details about the cyberattack.
NBC 7
Patients who have appointments scheduled in the coming days can call 1-800-SCRIPPS for more information about their appointment status.
The local health-care provider, operates five hospitals in San Diego, along with a series of clinics.
Here’s what happened in the last week, what we know and what we don’t know:
May 2, 2021
Scripps Health first confirmed on Sunday that their technology servers were hacked overnight forcing the health care system to switch to offline chart systems and causing a disruption to their patient portals.
Scripps did not provide any information on how the cyberattack occurred or state exactly what systems were affected by the breach.
The health care system said they suspended access to their patient portals and other “technology applications related to our operations at our health care facilities,” but stressed that patient care continues using “established back-up processes, including offline documentation methods.”
The San Diego County Office of Emergency Services (OES) said ambulances were being diverted from Scripps’ facilities to other hospitals in the area but that it was a precautionary measure.
As of May 5, the county had stopped adjusting its routing of…