Frustrated by slow downloads on your PC?

We have all been there. What is supposed to be a quick PDF download becomes a test of patience and determination. Will the download take three minutes or 30? Some days you do not have time to roll the dice: You want the files you download to take less time than, say, constructing a full-scale model of the Golden Gate bridge.
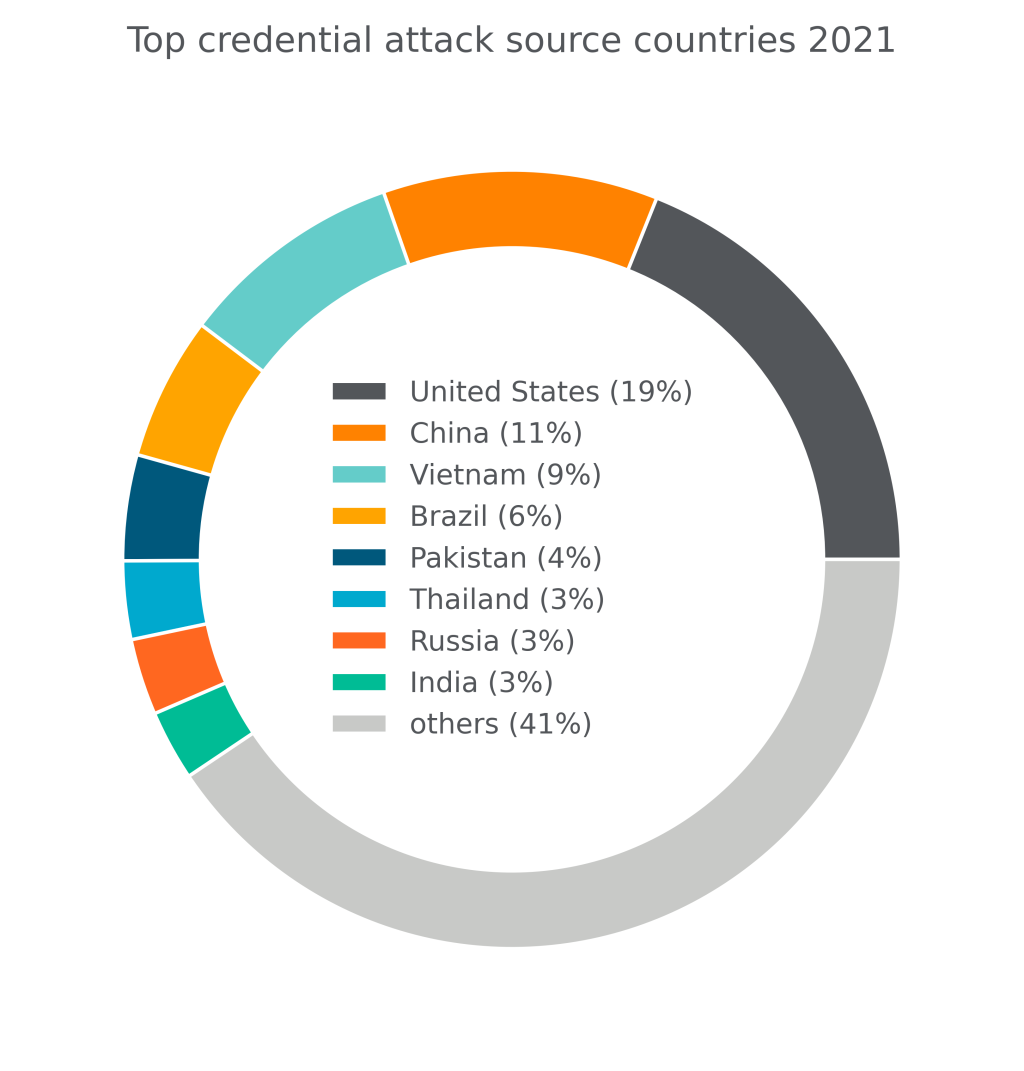
With that in mind, I rounded up some reasons your downloads and your computer in general have slowed down.
Reason #1: A security issue
What is that old saying about hating to be the bearer of bad news? Well, it certainly applies here. Your speed could be bogged down if your systems are infected in any way. Hackers will use your systems to send out spam emails, steal your contacts, track browsing sites and habits and deliver invasive and targeted ads. Consider professional support for your laptops and desktops, factory resets for your mobile devices and a replacement networking system, such as one of the new mesh network systems.”
Reason #2: A weak Wi-fi signal
Once you rule out security issues, it is time to look to your Wi-fi signal and test your internet, which could explain slow downloads, so you need to run internet speed tests. Run speed tests on a mobile device right next to the main modem/router/access point, and then test further away and see if the speeds stay reasonable.
While there are several tests available, contact your internet provider and see the software they are running. By testing with that product eliminates any argument of different results with different products. The internet speed test is worth trying as the test will let you know if the connection becomes weak or slow. The test will also show if the ISP internet provider is supplying the speed that you contract with them.
If possible, test a hardwired connection to see if there is a speed difference between Wi-fi and plugged in. An older laptop is ideal for this, as some new machines often do not have plug-in internet anymore.
Reason #3: A slow connection
A slow internet connection is frequently to blame for slow downloads. Many residential areas have limited or only one option for an internet provider. Being in a rural area will often have no connection other than cellular and…