How EDR Security Supports Defenders in a Data Breach
The cost of a data breach has reached an all-time high. It averaged $4.35 million in 2022, according to the newly published IBM Cost of a Data Breach Report. What’s more, 83% of organizations have faced more than one data breach, with just 17% saying this was their first data breach.
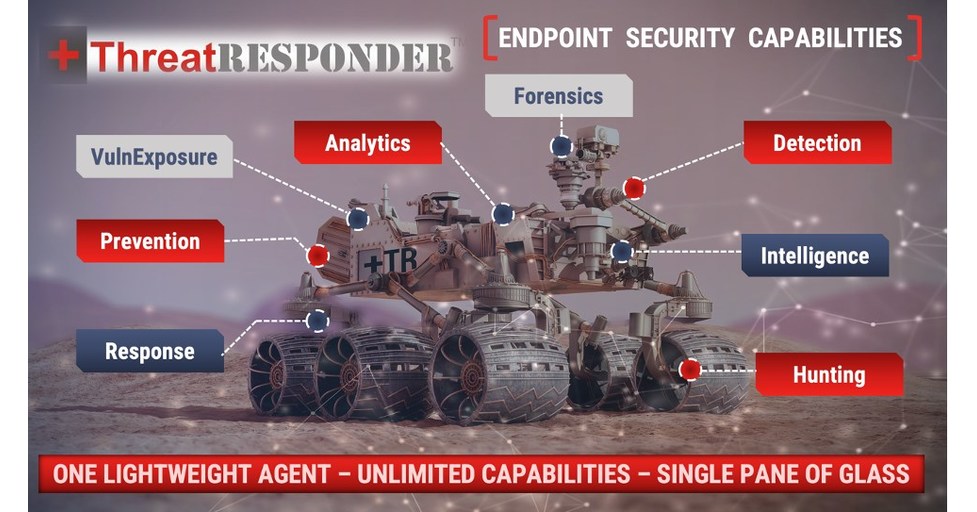
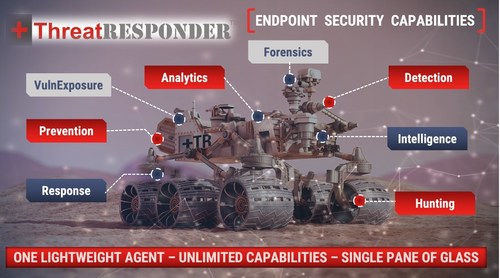
What can organizations do about this? One solution is endpoint detection and response (EDR) software. Take a look at how an effective EDR solution can help your security teams.
What is a Data Breach?
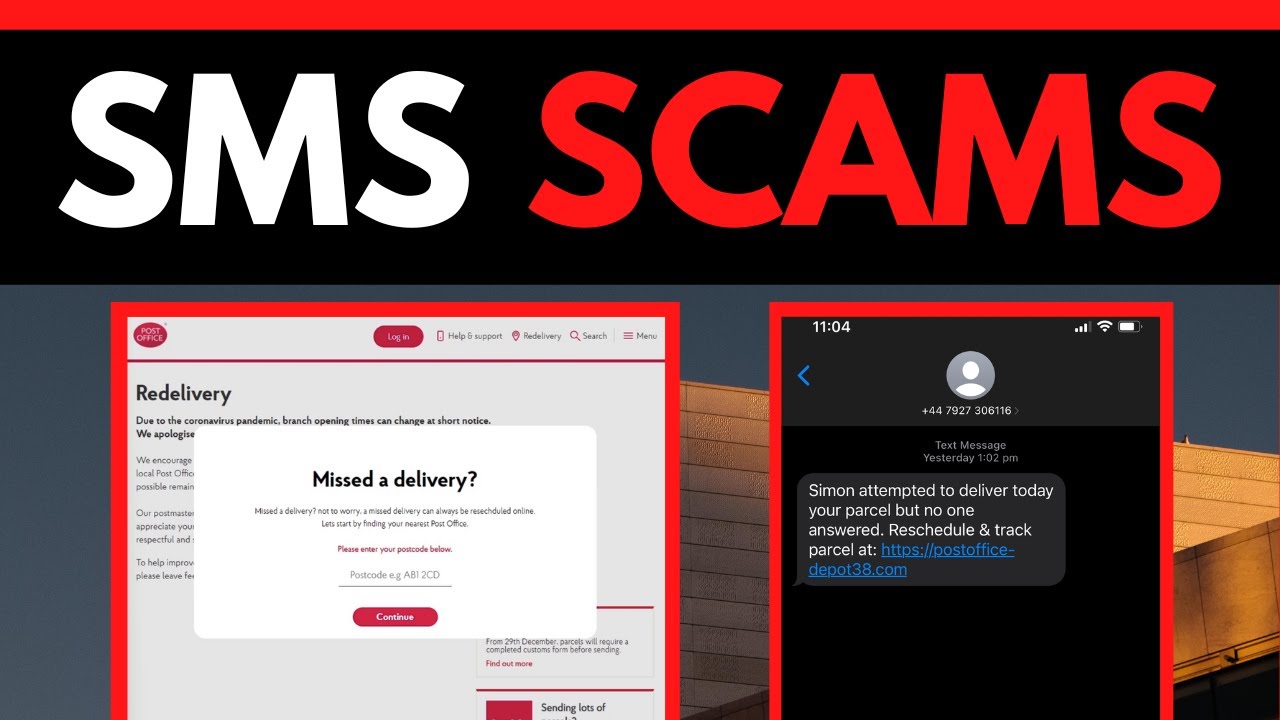
A data breach is a cyberattack where a threat actor infiltrates a data source and exposes sensitive, confidential and protected data. This can occur as a result of ransomware attacks, phishing or malware attacks or other types of data theft. Whatever the source of the breach, it always leads to a loss of trust and damages the victim’s good name. It leaves many questions. How did the attack begin? How many devices did it strike? Have attackers stolen data? If yes, how much and from where?
Sharing an example of how threat actors might launch a phishing attack, Stephanie Carruthers, chief people hacker for IBM X-Force recounts:
“We had a client that wanted us to launch a phishing campaign against a hundred of their employees. We started to look through the company’s website and blogs, and we found a website where employees can post reviews about their employer. One common issue that we saw, which a lot of people complained about, was the parking at their job. So, we crafted a phishing campaign that actually explained how starting Monday, it was going to be assigned parking, and they just had to view the map to see their space, or else they would get towed. And that was one of our successful campaigns because we saw what people absolutely hated, and we tried to fix it in a way. And just by that website where we found all that information, it made our campaign extremely successful.”
What to Do After a Data Breach
After a breach, cyber defenders or blue teams work under a lot of pressure to find answers quickly. Often there is a state of temporary shutdown, resulting in loss of revenue and critical data, which threatens business continuity. After the attack, defenders try to find the…