Endpoint Protection / Antivirus Products Tested for Malware Protection
AUSTIN, Texas – Aug. 25, 2022 — CyberRatings.org, the nonprofit entity dedicated to providing transparency on cybersecurity product efficacy, has published results of its Q2 2022 Endpoint Protection Comparative Test.
Focused on endpoint products that feature antivirus protection, the products tested were Avast Free Antivirus, AVG AntiVirus Free, ESET Internet Security, McAfee Total Protection, Norton 360, Microsoft Defender, Sophos Home Premium and Trend Micro Maximum Security.
“The bad guys are getting bolder and malware / ransomware campaigns continue to get more sophisticated,” said Vikram Phatak, CEO of CyberRatings.org. “Most infections occur in the first few hours after a new campaign is launched. The time it takes for a security product to block the attack matters a lot,” adds Phatak. “That is why we tested not only how much malware a product blocks, but how quickly it blocks an attack.”
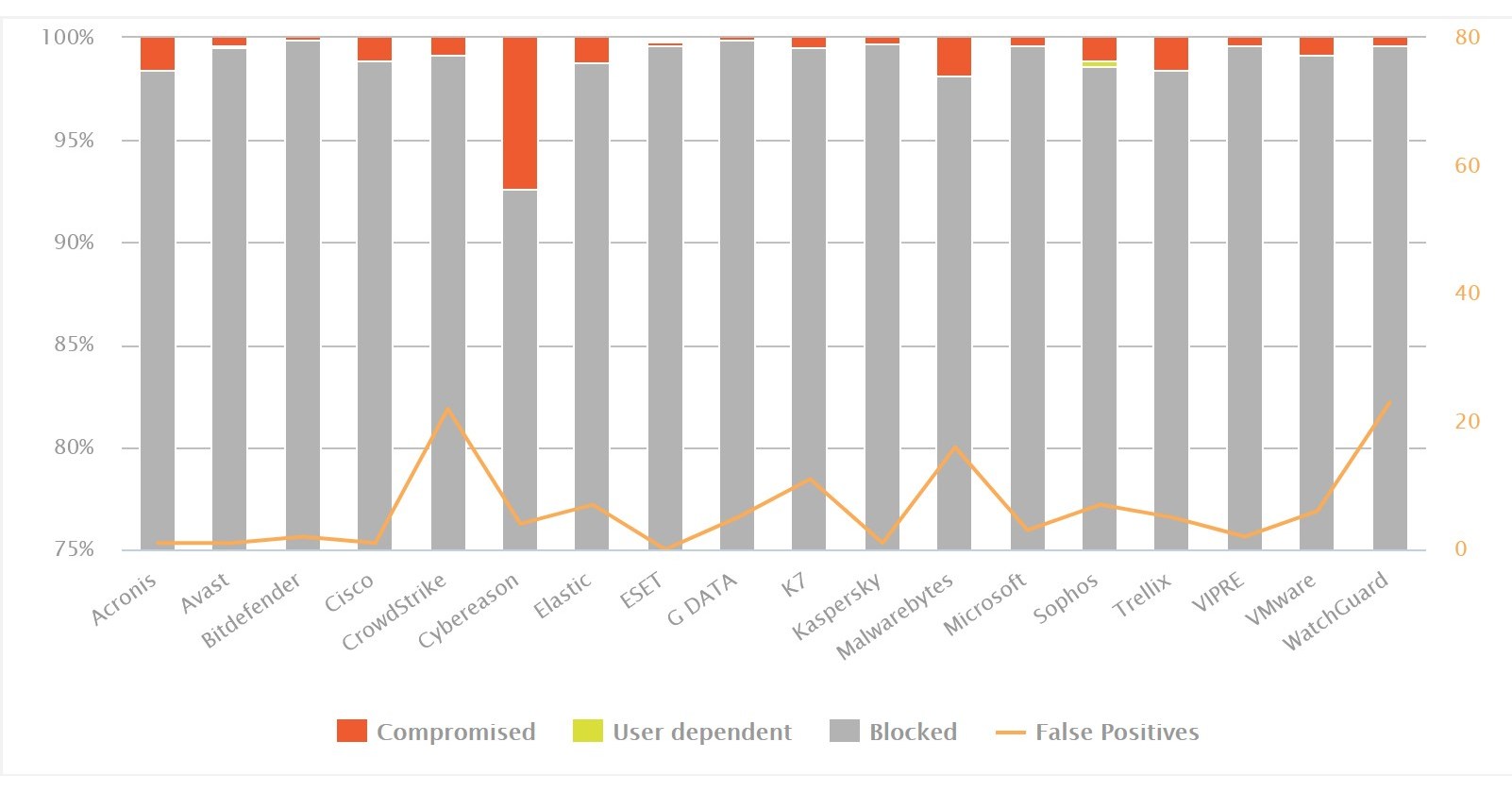
Over 40,000 live tests were performed on each product, providing a ±0.49% margin of error. Trend Micro Maximum Security offered the most protection, blocking 97.97% of malware. Sophos Home Premium provided the second-highest protection, blocking 97.47%, followed by Microsoft Defender at 97.13%. Sophos was the quickest to add protection for previously unblocked malware, closely followed by Trend Micro.
With more businesses embracing remote work, a user’s protection is likely limited to the web browser and their endpoint protection product. Therefore, it’s important to be informed about which products are performing as advertised.
The Comparative Test Reports provide metrics for products blocking malware over time, average time a product added protection, and average time it took a product to add protection.
The test was funded by CyberRatings.org and no vendor paid to be in or out of the test. As a service to the community, CyberRatings.org is providing these reports for free.
The following endpoint protection / antivirus products were tested:
- Avast Free Antivirus – v22.4.6011 (build 22.4.7175.725)
- AVG AntiVirus Free – v22.4.3231 (build 22.4.7175.725)
- ESET Internet Security – v15.1.12.0
- McAfee Total Protection – v16.0 R46
- Norton 360 (latest updates)
- Sophos Home…