Automotive Cyber Security Market Is Estimated To Expand At
Automotive Cyber Security Market overview
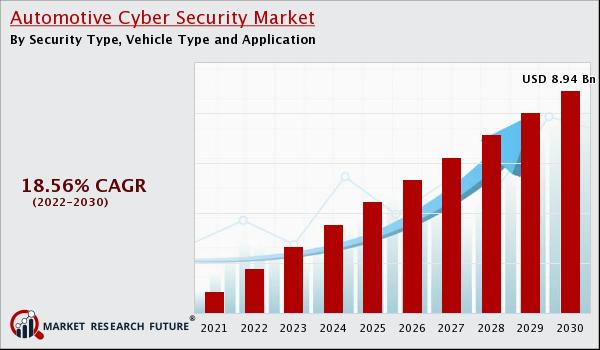
By 2028, the Automotive Cyber Security Market is estimated to be worth USD 8.94 billion, recording a CAGR of 18.56% during the predicted period (2021 – 2028). The market was valued at a rate of USD 2.16 billion in 2020. The choices, preferences and desires of drivers are rapidly changing. Consumers are now expecting personalized experiences, so the vehicle industry is adapting the technique to meet those demands. More software results from increased personalization and connectedness, which means more vulnerability.
Connected vehicles can function similarly to smartphones and smart appliances. The sharing of internet and wireless network access with other vehicles and external equipment can send and receive data. New and advanced software is already providing greater features and capabilities to fulfill the needs and expectations of drivers. In such cases, automobile cybersecurity is serious, and it should be a part of the design process.
The factors that are estimated to drive the growth of the automotive cybersecurity market are an increase in the need for automotive cybersecurity, government initiatives for implementing connected car technology, and mandatory cybersecurity standards. However, the increase in the development of common podiums is leading to high risks, and the challenge is making the applications secure, which restrains the market growth. However, improving vehicle security using adaptive security and increasing the complexity of cars’ electronic systems are estimated to offer profitable growth opportunities for the market players.
Request Free Sample of Report @ https://www.marketresearchfuture.com/sample_request/2970
The outbreak of covid-19 forced governments across the globe to impose strict lockdowns and made social distancing mandatory to stop the virus from spreading. This resulted in a drop of demand for new vehicles significantly. However, the automotive industry also had a slow production rate; there was a reduction in the supply of raw materials and breakage in the supply chains globally. The losses observed by the automotive sector have affected the…