North Korean Nation-State Actors Exposed in JumpCloud Hack After OPSEC Blunder
North Korean nation-state actors affiliated with the Reconnaissance General Bureau (RGB) have been attributed to the JumpCloud hack following an operational security (OPSEC) blunder that exposed their actual IP address.
Google-owned threat intelligence firm Mandiant attributed the activity to a threat actor it tracks under the name UNC4899, which likely shares overlaps with clusters already being monitored as Jade Sleet and TraderTraitor, a group with a history of striking blockchain and cryptocurrency sectors.
UNC4899 also overlaps with APT43, another hacking crew associated with the Democratic People’s Republic of Korea (DPRK) that was unmasked earlier this March as conducting a series of campaigns to gather intelligence and siphon cryptocurrency from targeted companies.
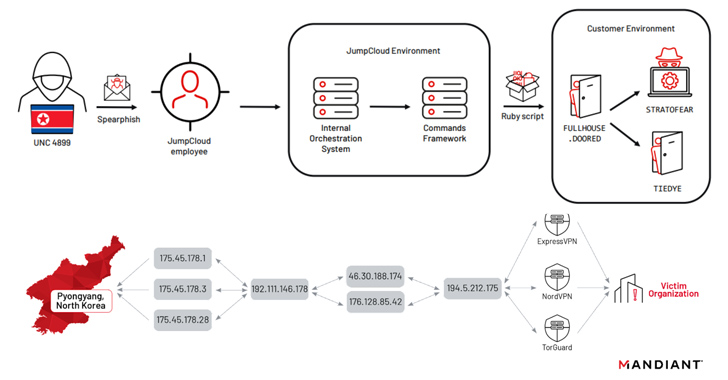
The adversarial collective’s modus operandi is characterized by the use of Operational Relay Boxes (ORBs) using L2TP IPsec tunnels along with commercial VPN providers to disguise the attacker’s true point of origin, with commercial VPN services acting as the final hop.
“There have been many occasions in which DPRK threat actors did not employ this last hop, or mistakenly did not utilize this while conducting actions on operations on the victim’s network,” the company said in an analysis published Monday, adding it observed “UNC4899 connecting directly to an attacker-controlled ORB from their 175.45.178[.]0/24 subnet.”
The intrusion directed against JumpCloud took place on June 22, 2023, as part of a sophisticated spear-phishing campaign that leveraged the unauthorized access to breach fewer than five customers and less than 10 systems in what’s called a software supply chain attack.
Mandiant’s findings are based on an incident response effort initiated in the aftermath of a cyber attack against one of JumpCloud’s impacted customers, an unnamed software solutions entity, the starting point being a malicious Ruby script (“init.rb”) executed via the JumpCloud agent on June 27, 2023.
A notable aspect of the incident is its targeting of four Apple systems running macOS Ventura versions 13.3 or 13.4.1, underscoring North Korean actors’ continued investment in honing malware specially tailored for the platform in…