North Korea’s ScarCruft Deploys RokRAT Malware via LNK File Infection Chains
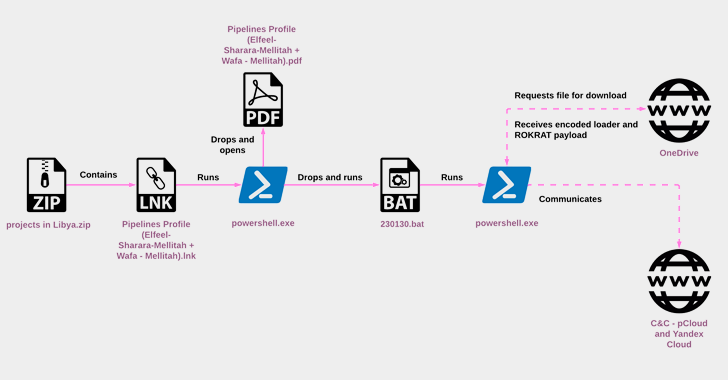
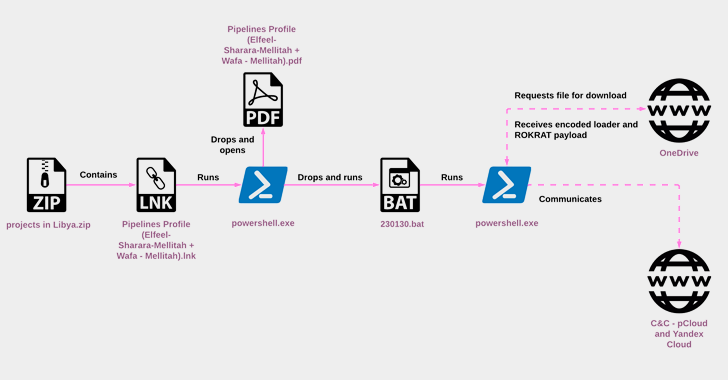
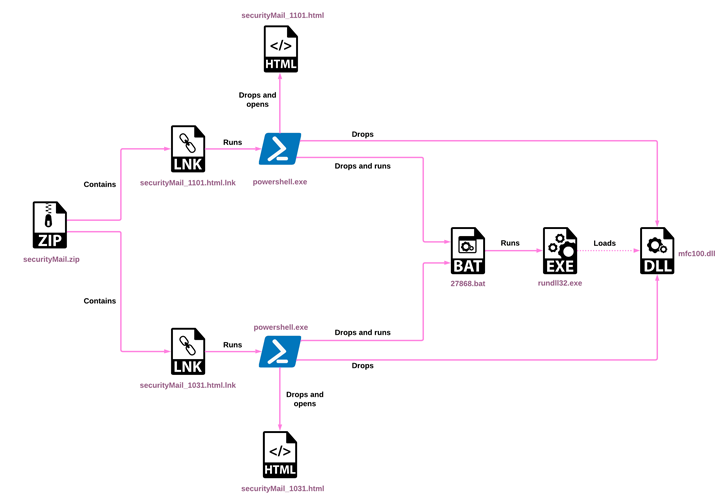
The North Korean threat actor known as ScarCruft began experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default.
“RokRAT has not changed significantly over the years, but its deployment methods have evolved, now utilizing archives containing LNK files that initiate multi-stage infection chains,” Check Point said in a new technical report.
“This is another representation of a major trend in the threat landscape, where APTs and cybercriminals alike attempt to overcome the blocking of macros from untrusted sources.”
ScarCruft, also known by the names APT37, InkySquid, Nickel Foxcroft, Reaper, RedEyes, and Ricochet Chollima, is a threat group that almost exclusively targets South Korean individuals and entities as part of spear-phishing attacks designed to deliver an array of custom tools.
The adversarial collective, unlike the Lazarus Group or Kimsuky, is overseen by North Korea’s Ministry of State Security (MSS), which is tasked with domestic counterespionage and overseas counterintelligence activities, per Mandiant.
The group’s primary malware of choice is RokRAT (aka DOGCALL), which has since been adapted to other platforms such as macOS (CloudMensis) and Android (RambleOn), indicating that the backdoor is being actively developed and maintained.
RokRAT and its variants are equipped to carry out a wide range of activities like credential theft, data exfiltration, screenshot capture, system information gathering, command and shellcode execution, and file and directory management.
The collected information, some of which is stored in the form of MP3 files to cover its tracks, is sent back using cloud services like Dropbox, Microsoft OneDrive, pCloud and Yandex Cloud in a bid to disguise the command-and-control (C2) communications as legitimate.
Other bespoke malware used by the group include, but not limited to, Chinotto, BLUELIGHT, GOLDBACKDOOR, Dolphin, and, most recently, M2RAT. It’s also known to use commodity malware such as Amadey, a downloader that can receive commands from the attacker to…