SpaceX says researchers are welcome to hack Starlink and can be paid up to $25,000 for finding bugs in the network
-
Elon Musk’s SpaceX said it encourages researchers to hack Starlink in a non-disruptive way.
-
If researchers submit findings through SpaceX’s bug bounty program, they could be paid up to $25,000.
-
One researcher recently said he hacked into Starlink using a $25 homemade device.
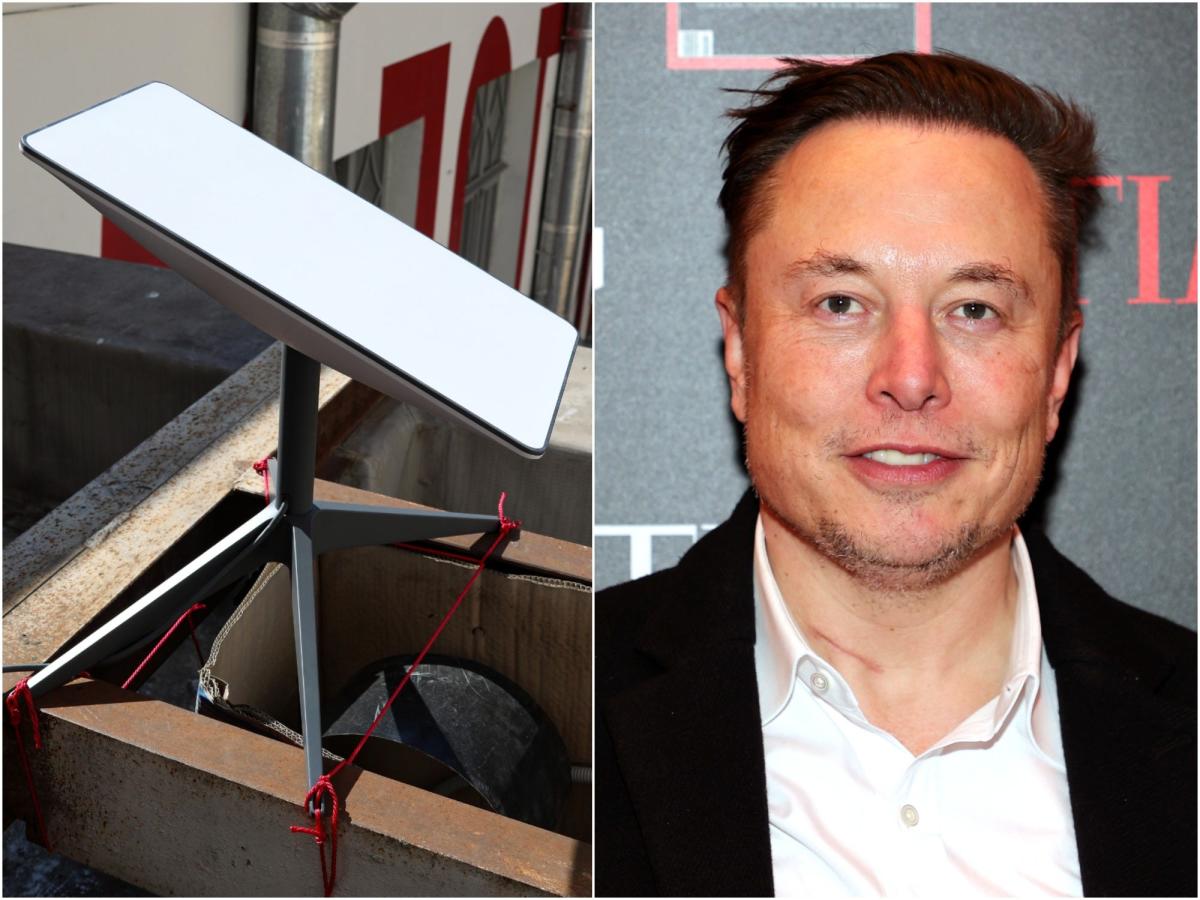
SpaceX says responsible researchers are welcome to hack into its satellite internet network, Starlink. It added that it could pay them up to $25,000 for discovering certain bugs in the service.
The announcement came after security researcher Lennert Wouters said last week he was able to hack into Starlink using a $25 homemade device. He said he performed the test as part of SpaceX’s bug bounty program, where researchers submit findings of potential vulnerabilities in Starlink’s network.
In a six-page document entitled “Starlink welcomes security researchers (bring on the bugs),” SpaceX congratulated Wouters on his research.
“We find the attack to be technically impressive, and is the first attack of its kind that we are aware of in our system,” SpaceX said in the document. Wouters’ hack involving a homemade circuit board shouldn’t worry any Starlink users and won’t directly affect the satellites, SpaceX added.
The company’s own engineers are always trying to hack Starlink to improve the service and make it more secure, SpaceX said in the document. It welcomed any security researchers who wanted to help secure Starlink, saying they should consider joining the team or contributing their findings to the company’s bug bounty program.
“We allow responsible security researchers to do their own testing, and we provide monetary rewards when they find and report vulnerabilities,” SpaceX said in the document.
On SpaceX’s bug bounty website, it says researchers who carry out non-disruptive tests on Starlink, report the findings, and discover vulnerabilities within scope can be rewarded between $100 and $25,000.
The site lists 32 researchers who SpaceX said reported important security issues in Starlink. It also says the average payout in the last three months was $973.
Testing that disrupts the service for…