This popular game gives hackers access to your entire PC
Hackers have been abusing the anti-cheat system in a massively popular game, and you don’t even need to have it installed on your computer to be affected.
The game in question is called Genshin Impact, and according to a new report, hackers are able to utilize the game’s anti-cheat measures in order to disable antivirus programs on the target machine. From there, they’re free to conduct ransomware attacks and take control of the device.
Trend Micro prepared a lengthy report about this new hack, describing the way it works in great detail. The attack can be carried out using a Genshin Impact driver called “mhypro2.sys.” As mentioned above, the game doesn’t need to be installed on the targeted device. The module can operate independently and doesn’t need the game in order to run.
Researchers have found proof of threat actors using this vulnerability to conduct ransomware attacks since July 2022. While it’s unclear how the hackers are initially able to gain access to their target, once they’re in, they’re able to use the Genshin Impact driver in order to access the computer’s kernel. A kernel generally has full control over everything that happens in your system, so for threat actors to be able to access it is disastrous.
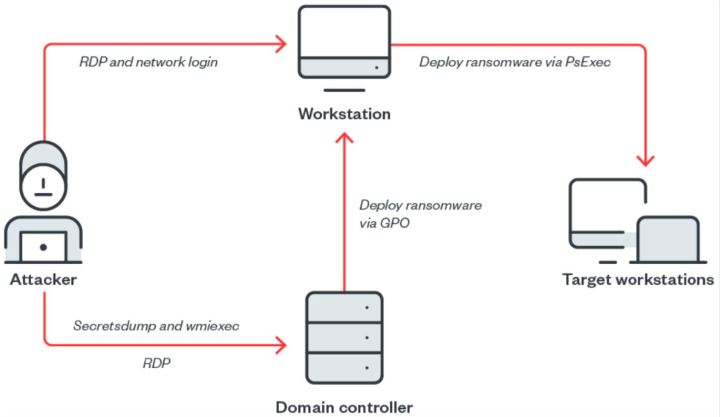
The hackers used “secretsdump,” which helped them snatch admin credentials, and “wmiexec,” which executed their commands remotely through Windows’ own Management Instrumentation tool. These are free and open-source tools from Impacket that anyone could get their hands on if they wanted to.
With that out of the way, the threat actors were able to connect to the domain controller and implant malicious files onto the machine. One of these files was an executable called “kill_svc.exe” and it was used to install the Genshin Impact driver. After dropping “avg.msi” onto the desktop of the affected computer, four files were transferred and executed. In the end, the attacker was able to completely kill the computer’s antivirus software and transfer the ransomware payload.
After some hiccups, the adversaries were able to fully load the driver and the ransomware onto a network share with the goal of mass deployment,…




