Who is Alleged Medibank Hacker Aleksandr Ermakov? – Krebs on Security
Authorities in Australia, the United Kingdom and the United States this week levied financial sanctions against a Russian man accused of stealing data on nearly 10 million customers of the Australian health insurance giant Medibank. 33-year-old Aleksandr Ermakov allegedly stole and leaked the Medibank data while working with one of Russia’s most destructive ransomware groups, but little more is shared about the accused. Here’s a closer look at the activities of Mr. Ermakov’s alleged hacker handles.

Aleksandr Ermakov, 33, of Russia. Image: Australian Department of Foreign Affairs and Trade.
The allegations against Ermakov mark the first time Australia has sanctioned a cybercriminal. The documents released by the Australian government included multiple photos of Mr. Ermakov, and it was clear they wanted to send a message that this was personal.
It’s not hard to see why. The attackers who broke into Medibank in October 2022 stole 9.7 million records on current and former Medibank customers. When the company refused to pay a $10 million ransom demand, the hackers selectively leaked highly sensitive health records, including those tied to abortions, HIV and alcohol abuse.
The U.S. government says Ermakov and the other actors behind the Medibank hack are believed to be linked to the Russia-backed cybercrime gang REvil.
“REvil was among the most notorious cybercrime gangs in the world until July 2021 when they disappeared. REvil is a ransomware-as-a-service (RaaS) operation and generally motivated by financial gain,” a statement from the U.S. Department of the Treasury reads. “REvil ransomware has been deployed on approximately 175,000 computers worldwide, with at least $200 million paid in ransom.”
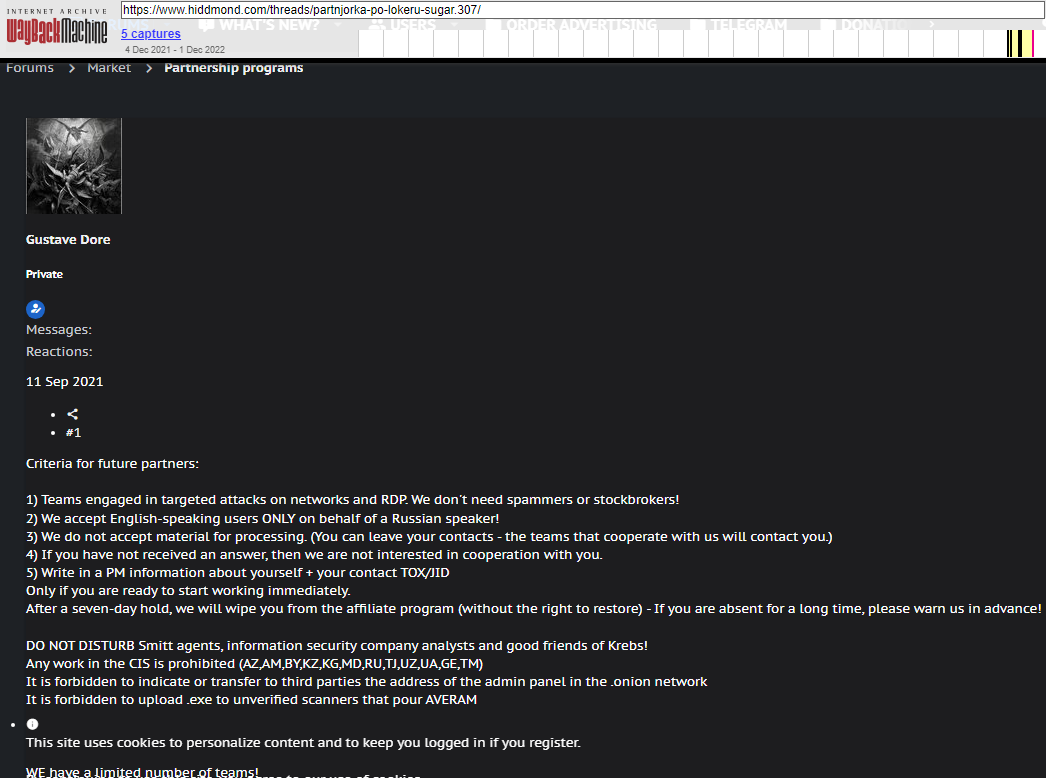
The sanctions say Ermakov went by multiple aliases on Russian cybercrime forums, including GustaveDore, JimJones, and Blade Runner. A search on the handle GustaveDore at the cyber intelligence platform Intel 471 shows this user created a ransomware affiliate program in November 2021 called Sugar (a.k.a. Encoded01), which focused on targeting single computers and end-users instead of corporations.