Samsung Releases Maintenance Mode, A New Feature To Hide Your Personal Information From Prying Eyes
The new privacy feature will roll out gradually to Galaxy devices starting with the Galaxy S22, allowing users to block access to their data while their devices are being serviced
Samsung Electronics Co., Ltd. today begins the global rollout[1] of Maintenance Mode, a new privacy feature coming to select Samsung Galaxy devices, following a successful pilot program in Korea and initial launch in China. Maintenance Mode can relieve user anxiety that comes with giving a personal device to someone for repairs, by letting users block access to their personal information, such as their photos, messages or contacts.
“Our whole lives are on our phones, from credit card information to family photos. With Maintenance Mode, we are giving extra reassurance that Galaxy users can keep their privacy, even if they hand their phone to someone,” said Seungwon Shin, VP and Head of Security Team at Mobile eXperience Business, Samsung Electronics. “This is just the latest example of our constant efforts to introduce new ways to make people feel safe and in control, so they can explore new mobile experiences with peace of mind, knowing we have their back.”
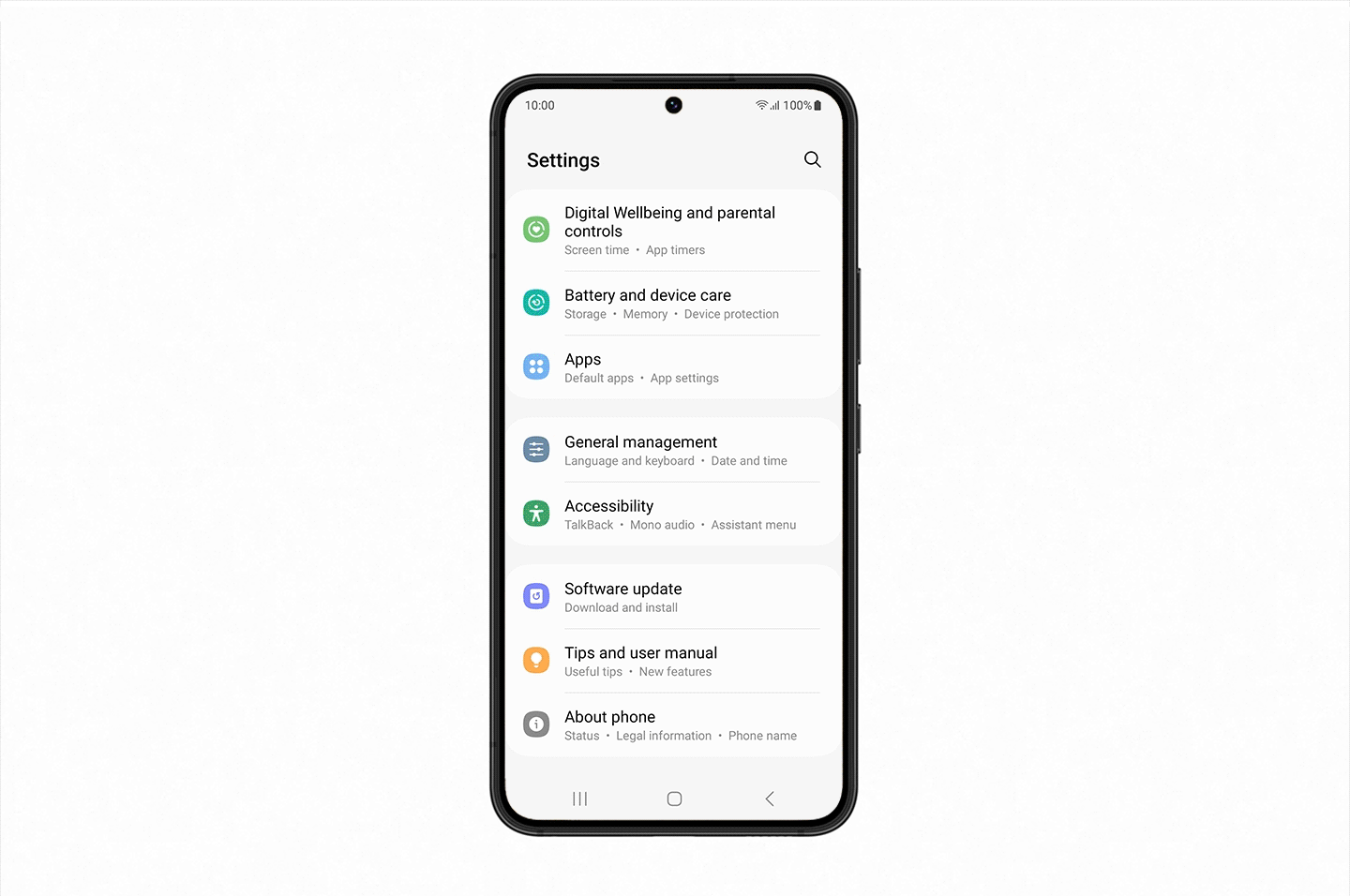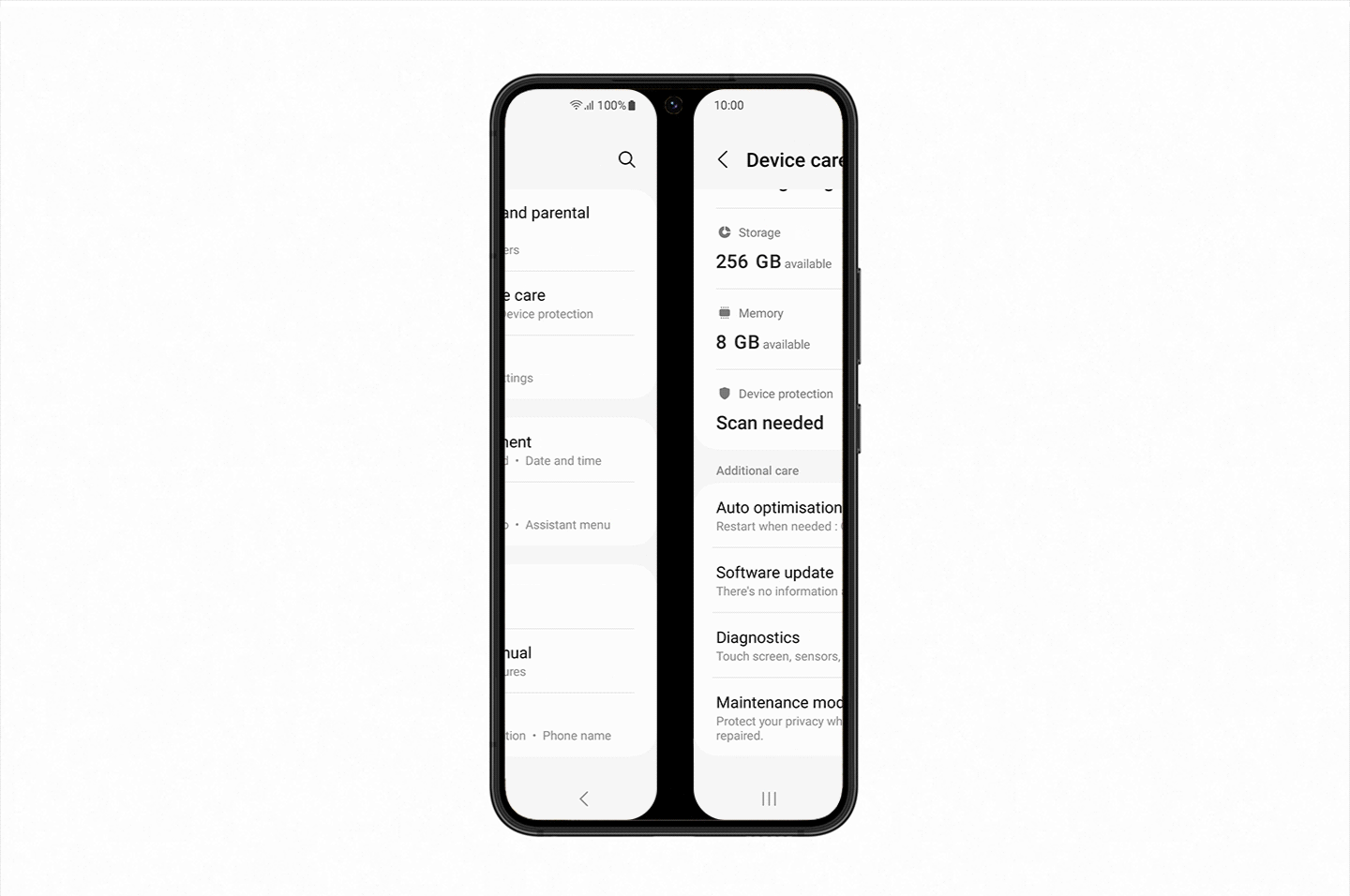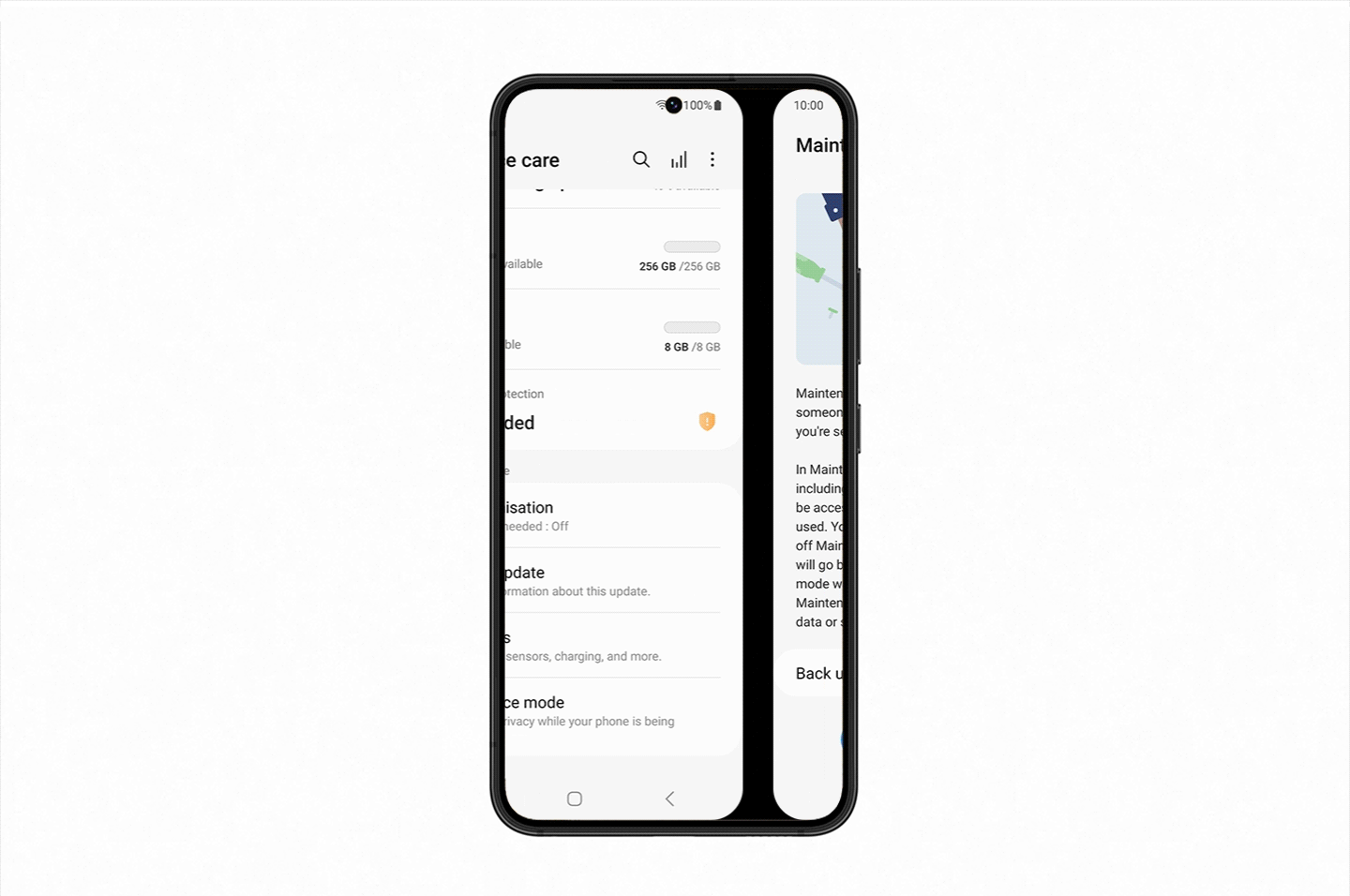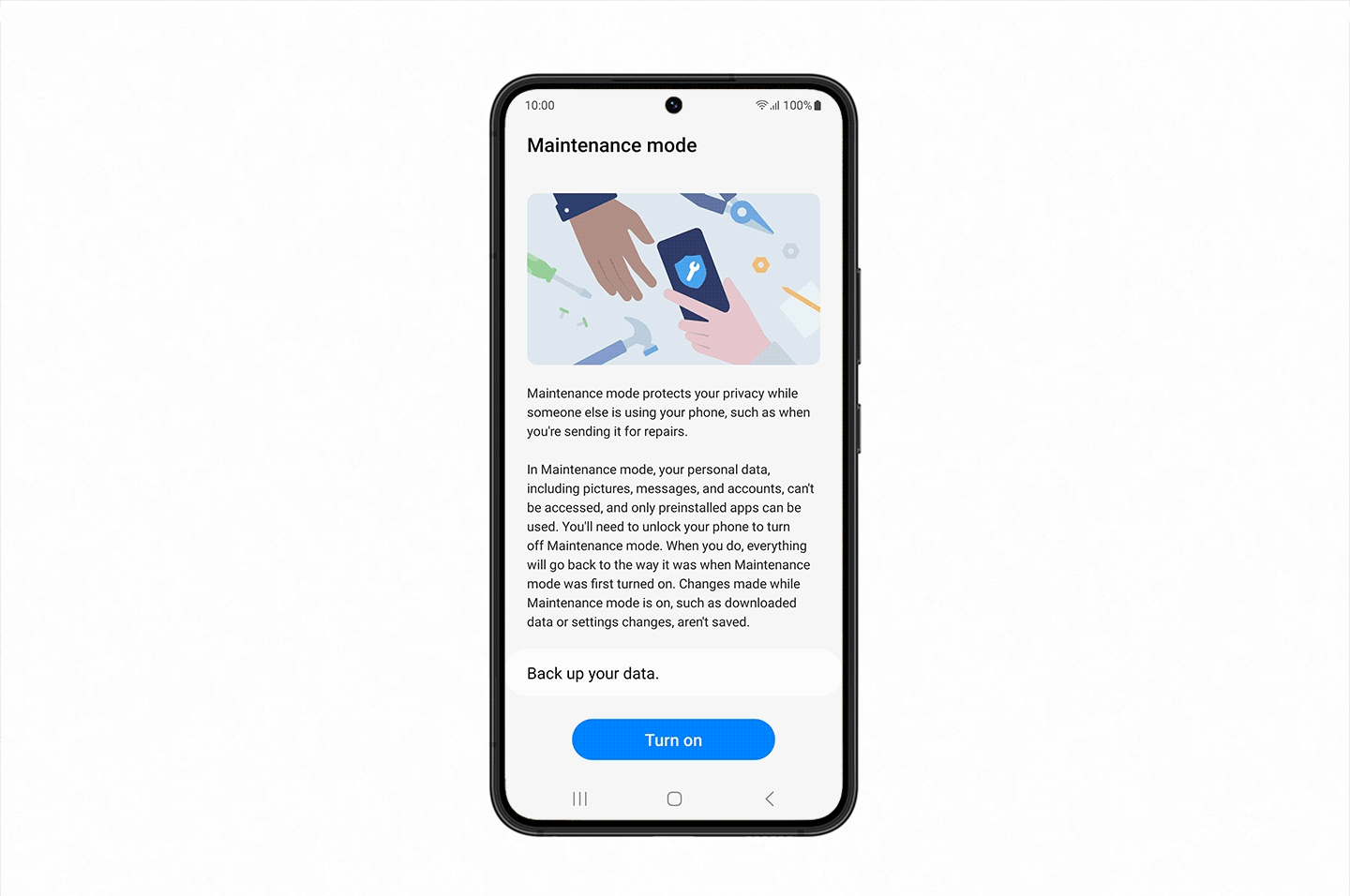
Maintenance Mode is a way of creating a separate user account when you hand in your device to be repaired so they can operate core functions without being able to access to any of your private information. All the user needs to do is select Maintenance Mode in the ‘Battery and device care’ menu within ‘Settings’, and reboot their smartphone. As soon as it’s rebooted, all their personal information including their photos, documents and messages will be restricted[2].
Once Maintenance Mode is switched on, the person who was entrusted with the device won’t be able to retrieve user-installed apps either. Data or accounts generated when using Maintenance Mode are automatically deleted as soon as the owner exits Maintenance Mode. They will be able to download apps on Galaxy Store, but those will be automatically deleted along with any data or accounts created as soon as the owner exits Maintenance Mode.
Samsung Galaxy devices are protected by Knox,…