Hey Alexa Go Hack Yourself: Researchers Detail Wild Self-Issued Smart Speaker Hijacks
Did you ever get an Amazon delivery and not remember placing an order for the item? There are plenty of stories of this all over the internet, and sometimes those boil down to one too many cocktails in your attitude adjustment hour. What if we told you that maybe one of those times it wasn’t related to brain fog or blackouts, but some random person decided to order something for you through your own Amazon Echo device?
That’s what researchers from the University of London’s Royal Holloway, and Catania University in Italy discovered is entirely possible. Through a few different methods of either social engineering or just being nearby an Echo device, Alex can be activated and used fairly easily. Tested on the third generation of the Echo Dot, though believed to be exploitable via fourth gen devices as well, the researchers found that playing audio files with the right wake words will activate the Alexa Voice-enabled device it is playing from. Dubbed “Alexa Versus Alexa” by the researchers, the exploit can be used to order products, make modifications to settings, install skills, and a whole host of other functionality that the Echo device product line allows Amazon Echo Dot owners to take advantage of.
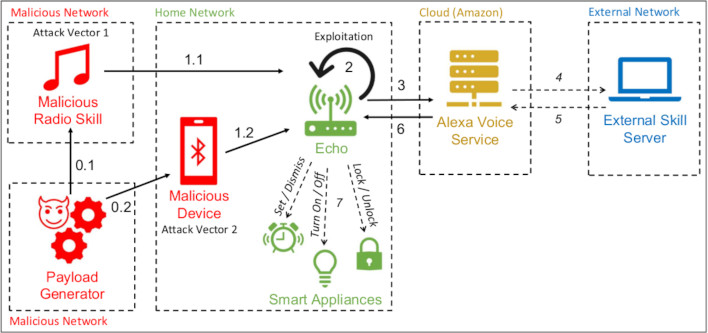
An social engineering exploit example would be having someone activate an internet radio station that intentionally utilizes common activation terms. So pre-existing skills, like Echo’s Music and Radio skill, may play one of these stations that then let that device activate itself. Part of the reason this can be a really big problem is that Amazon’s Echo devices typically only validate account activity and actions during the initial setup of the device. Skill installation is a big deal for this because these are small apps that run directly on the device, and with the right malicious code they can potentially be a security threat. That creates a situation where once the vulnerability is activated, the attacker can issue any command that is at the disposal of the Echo device.
Amazon has issued a patch (check your software version here), which you can force by asking the device to ‘check for updates’. However, the issue remains if the attacker is in…





