Cybersecurity: Preliminary Results Show That Agencies’ Implementation of FISMA Requirements Was Inconsistent
What GAO Found
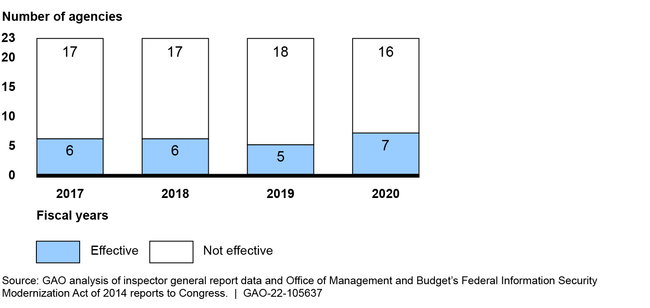
Based on GAO’s preliminary results, in fiscal year 2020, the effectiveness of federal agencies’ implementation of requirements set by the Federal Information Security Modernization Act of 2014 (FISMA) varied. For example, more agencies reported meeting goals related to capabilities for the detection and prevention of cybersecurity incidents, as well as those related to access management for users. However, inspectors general (IG) identified uneven implementation of cyber security policies and practices. For fiscal year 2020 reporting, IGs determined that seven of the 23 civilian Chief Financial Officers Act of 1990 (CFO) agencies had effective agency-wide information security programs. The results from the IG reports for fiscal year 2017 to fiscal year 2020 were similar with a slight increase in effective programs for 2020.
Number of 23 Civilian Chief Financial Officers Act of 1990 Agencies with Effective and Not Effective Agency-Wide Information Security Programs, as Reported by Inspectors General for Fiscal Years 2017-2020
GAO has also routinely reported on agencies’ inconsistent implementation of federal cybersecurity policies and practices. Since 2010, GAO has made about 3,700 recommendations to agencies aimed at remedying cybersecurity shortcomings; about 900 were not yet fully implemented as of November 2021. More recent GAO reviews have identified weaknesses regarding access controls, configuration management, and the protection of data shared with external entities. GAO has made numerous recommendations to address these.
Based on interviews with agency officials, such as chief information security officers, GAO’s preliminary results show that officials at 14 CFO Act agencies stated that FISMA enabled their agencies to improve information security program effectiveness to a great extent. Officials at the remaining 10 CFO Act agencies said that FISMA had improved their programs to a moderate extent. The officials also identified impediments to implementing FISMA, such as a lack of resources. Agency officials suggested ways to improve the FISMA reporting process, such as by updating FISMA metrics to increase their effectiveness, improving…

