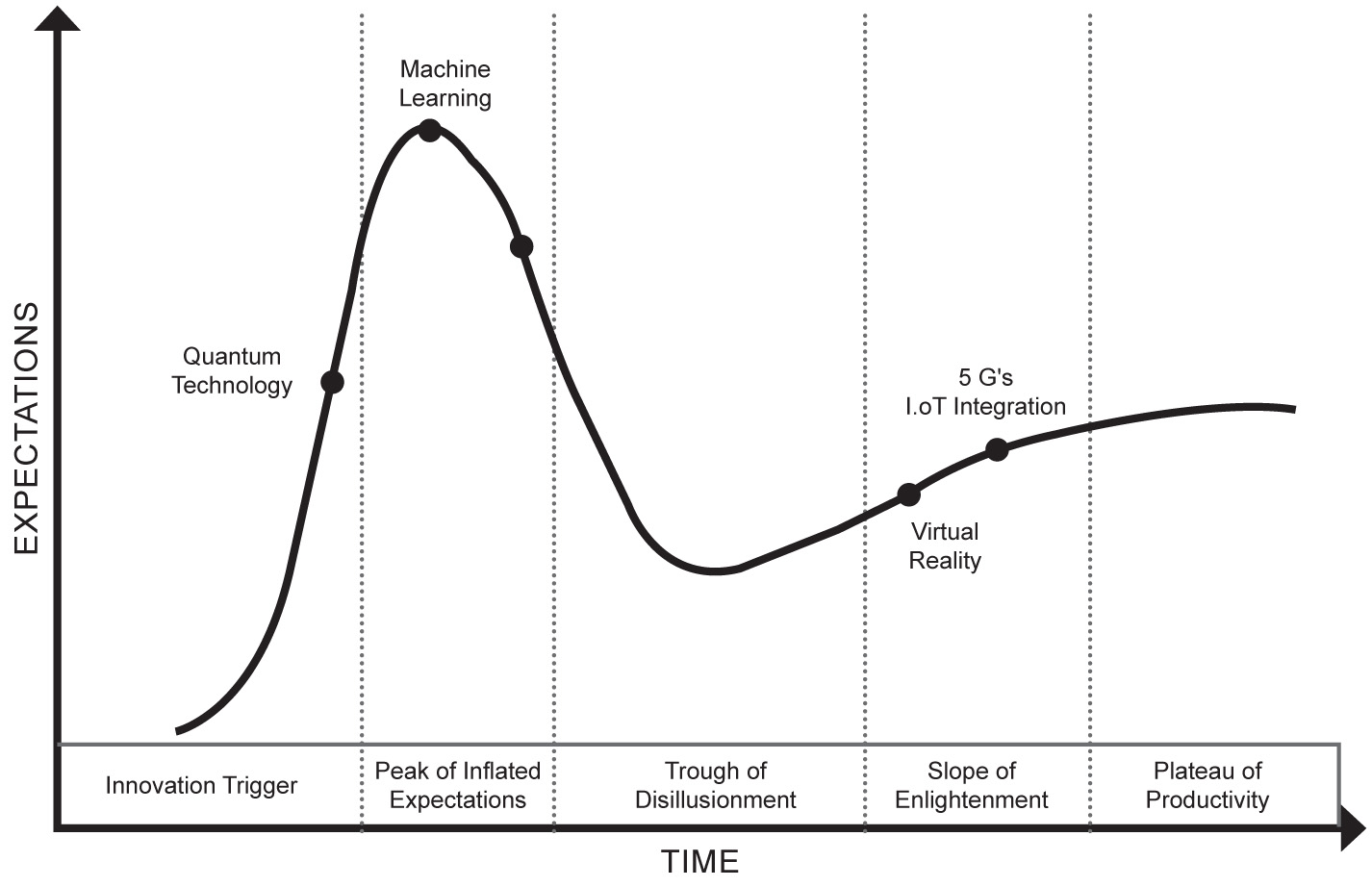
Quantum Technology: Gartner’s Hype Cycle and its Implications for National Security Policy
The 2022 Nobel Prize in Physics was awarded to three scientists “for experiments with entangled photons, establishing the violations of Bell Inequalities and pioneering quantum information science”. The press release dated October 04, 2022, noted that “the ineffable effects of quantum mechanics are starting to find applications and that the one very factor is how quantum mechanics allow two or more particles to exist in an entangled state and what happens to one of the particles of an entangled pair determines what happens to the other particle, even if they are far apart.
Quantum Technology
Quantum technology is any class of technology new or old that works by using the principles of quantum mechanics. Quantum technology revolutionises the concept of information processing from the earlier mechanical to digital mode a step further. It uses the dynamics of quantum physics or the behaviour of the universe’s smallest particles, the atom and the behaviour of matter at the sub-atomic scale. Quantum phenomenon is not new but was the basis of development of lasers and semi-conductors since the 1950s. Emerging quantum information technologies will lead to development of quantum computers, radars, cryptography and other systems by utilising the principles of quantum physics. At the very basic level, the technologies use the quantum principles of “entanglement” and “superposition” to share information by ways that are not possible in the classic electronic computers.
Superposition
Superposition is a term to describe the ability of any particle to exist across many states at the same time until it is measured so a particle is said to be in a “superposition” of all those possible states. Superposition has an implication on the concept of computing. Today’s computing involves information in bits; either zero or one. Quantum computers would process information in quantum bits or qubits which can be one, zero or a superposition of the two states which is huge number of possible states making computation exponentially faster than the most advanced available traditional computers today. In a coin analogy a bit is like a tossed coin…