SaaS, IoT, AI and Cloud will continue to accelerate Indian IT: ETILC Members
However, despite slowing down the financial ecosystem, the statewise lockdowns also had an upside; the pandemic drove companies worldwide to expand their investments in their respective digital infrastructure. The IT sector accounted for 8% of India’s GDP in 2020, which is a substantial increase from its contribution of 1.2% in 1998. In 2019-20, India held the position of the largest sourcing destination in the IT-BPM industry globally.
Growing Demand
As per Gartner’s predictions, IT spending in India will amount upto $98.5 billion by 2021. With the imposition of home isolation due to the pandemic, more and more people started accessing digital services from home. To make ends meet, the IT sector has been constantly keeping up with these demands by providing online services to businesses.
“India is at the cusp of creating massive employment opportunities in the IT/BPM sector, owing to tech like citizen development, AI and cloud”
The consequent demand and trust in the sector has facilitated companies like Cognizant, Infosys, and Wipro, Tanla Solutions, and HCL Tech with digital expansion as well as increased revenue. Moreover, Tech Mahindra experienced a growth of 39.2% with its net profit at Rs 1,353.2 crore for Q1 FY 2021-2022. Wipro witnessed revenue growth of 22.3% with Tata Consultancy Services at 18.5% growth.
As per the latest Naukri JobSpeak report, the Indian job market witnessed 57 per cent Y-o-Y growth as of September. The IT/software sector in particular grew by 138 per cent (Y-o-Y). Additionally, with thickening technological intervention and the gradual post-covid reopening, retail and hospitality industries also saw an increase in hiring by 82 per cent and 70 per cent, respectively. As digital innovation expands, the scope of job creation and acquisition will also…




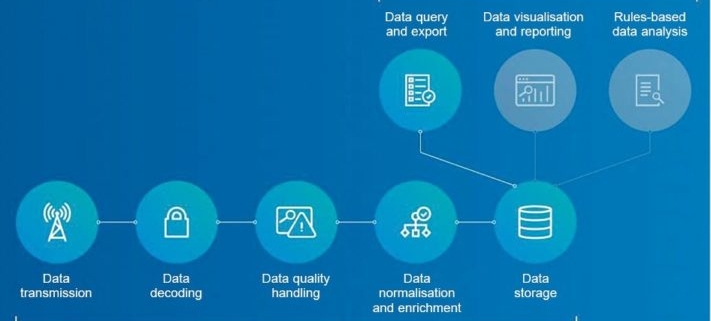
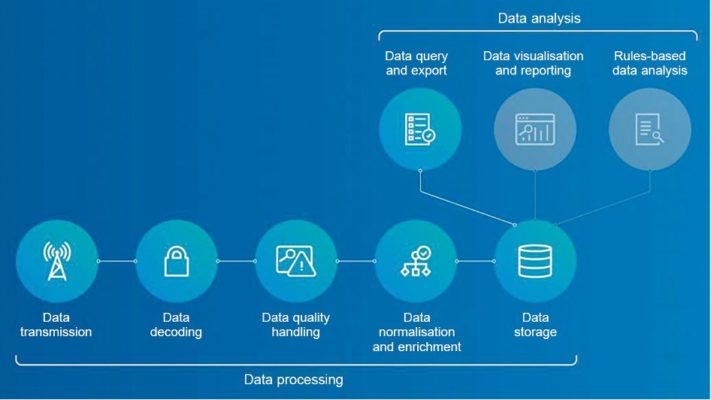
 Fig.2: Steps in IoT data management ( Source:
Fig.2: Steps in IoT data management ( Source: