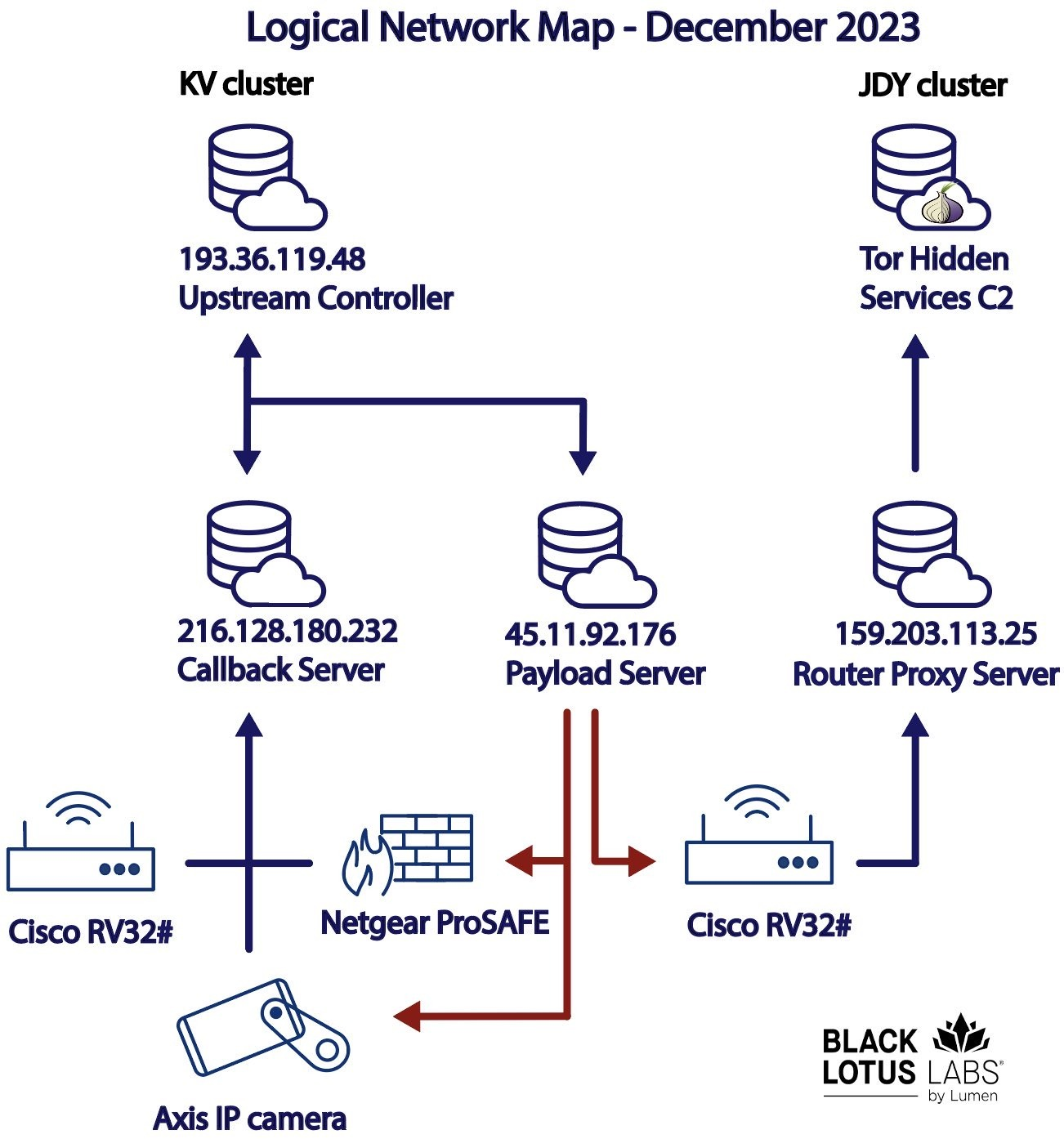
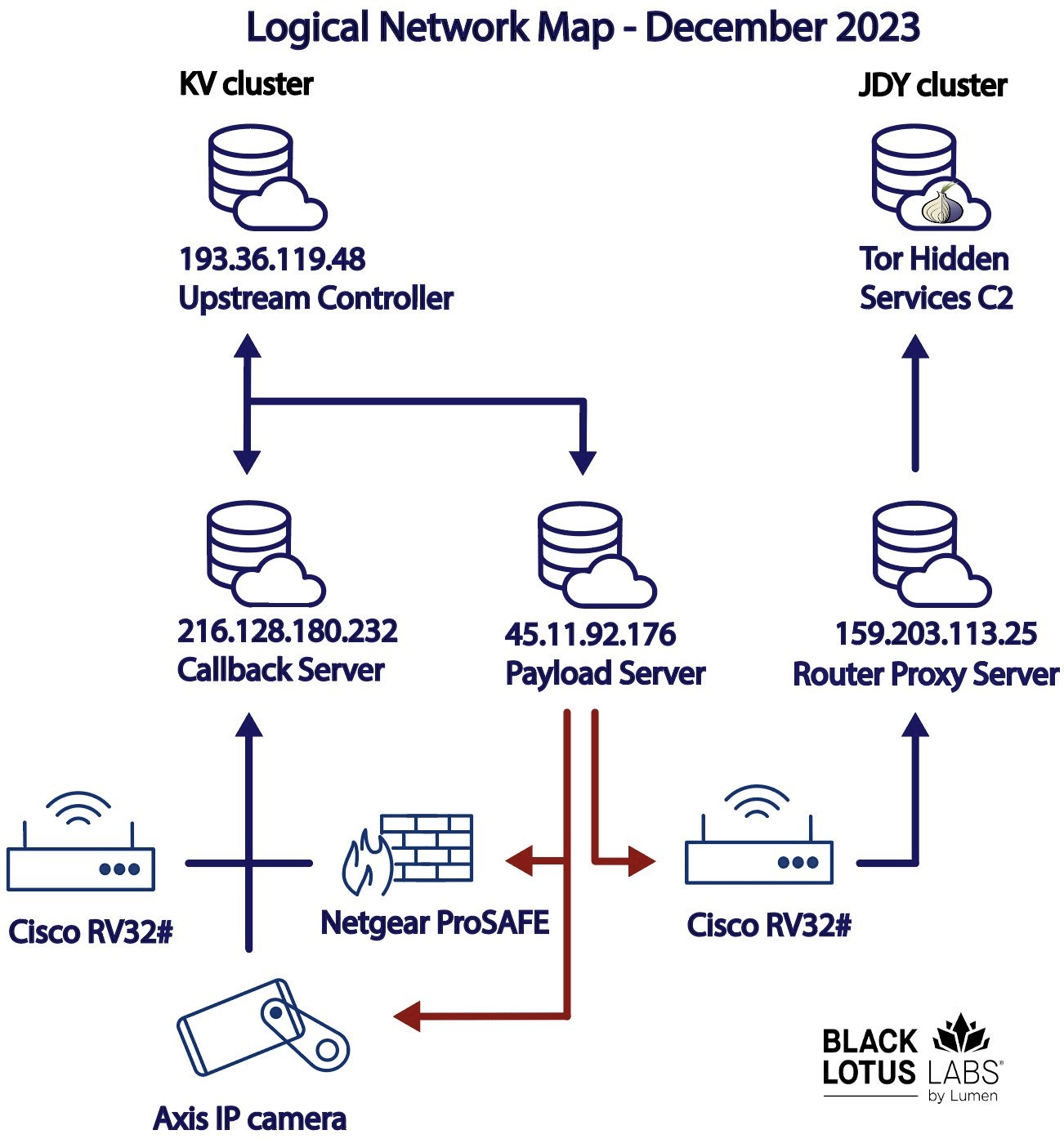
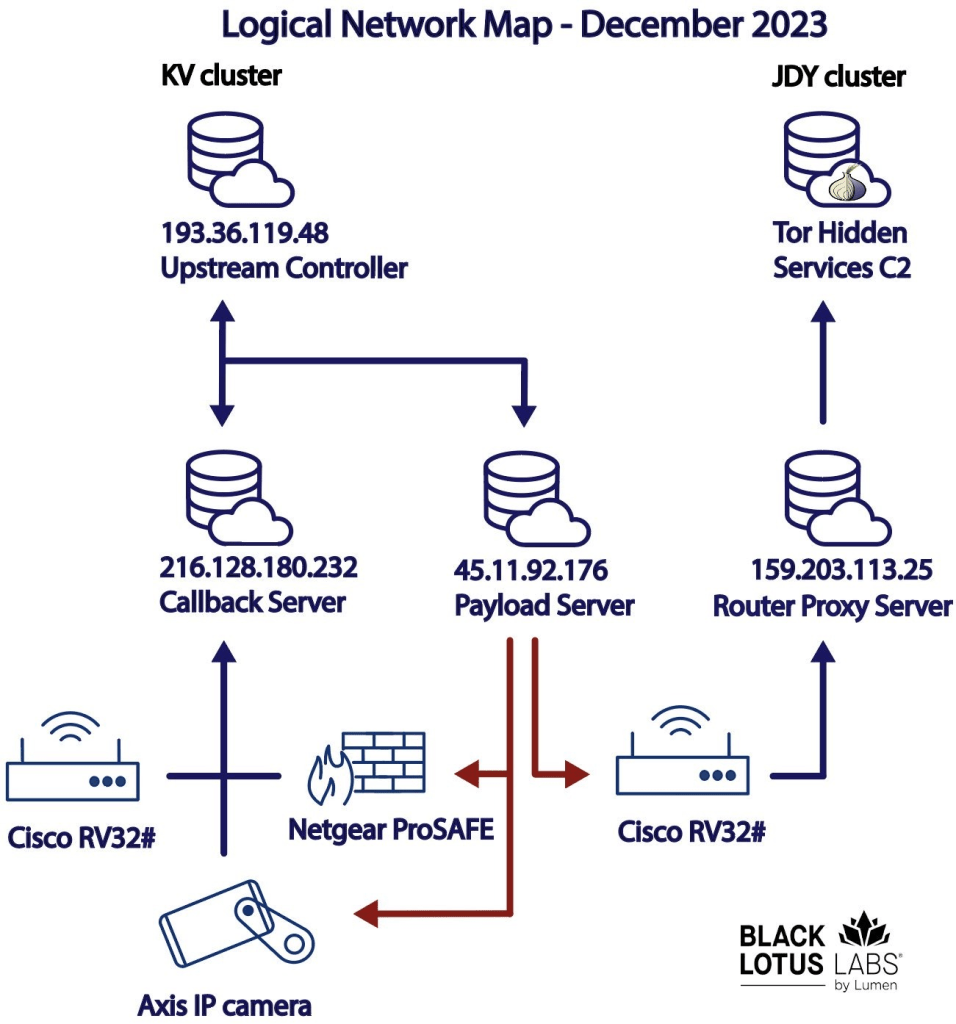
Fidelity National Financial discloses cyberattack previously linked to ransomware gang
Insurance and settlement service giant Fidelity National Financial Inc. has officially disclosed that they suffered from a “cybersecurity incident” that the infamous ransomware gang ALHPV/BlackCat claimed responsibility for in November.
The disclosure came via a Jan. 9 filing with the U.S. Securities and Exchange Commission, which states that Fidelity National became aware of a cybersecurity incident on Nov. 19 that impacted certain systems. The company then ticked off the standard response list: hiring third-party experts, notifying law enforcement and regulatory authorities and taking measures to block access to affected systems.
The incident is described as causing “varying levels of disruption” before being contained on Nov. 26 and systems restored. An investigation completed on Dec. 19 subsequently found that an unauthorized third party had accessed certain systems, deployed malware and exfiltrated certain data.
Fidelity National added that it has no evidence that any customer-owned system was directly impacted in the incident and no customer has reported that this has occurred. The last confirmed date of unauthorized third-party activity in the company’s network occurred Nov. 20.
Affected customers have been notified and offered credit monitoring, web monitoring and identity theft restoration services. Fidelity is also continuing to coordinate with law enforcement, its customers, regulators, advisers and other stakeholders.
What’s missing from the disclosure is any mention of ransomware. Companies describing attacks at cybersecurity incidents aren’t new, but usually, the notices don’t follow widespread media coverage of them being targeted by a ransomware gang. That ALPHV/BlackCat is behind the attack is also highly believable, as the ransomware gang was one of the most prolific through 2023.
Cybersecurity experts agree with Craig Jones, vice president of security operations at SecOps security company Ontinue Inc., telling SiliconANGLE that per the SEC filing, the attack involved data exfiltration,
“Fidelity National Financial appears to have experienced a ransomware attack attributed to the ALPHV/BlackCat ransomware group,” Jones said….