Iranian Hackers’ Sophisticated Malware Targets Windows and macOS Users
The Iranian nation-state actor known as TA453 has been linked to a new set of spear-phishing attacks that infect both Windows and macOS operating systems with malware.
“TA453 eventually used a variety of cloud hosting providers to deliver a novel infection chain that deploys the newly identified PowerShell backdoor GorjolEcho,” Proofpoint said in a new report.
“When given the opportunity, TA453 ported its malware and attempted to launch an Apple flavored infection chain dubbed NokNok. TA453 also employed multi-persona impersonation in its unending espionage quest.”
TA453, also known by the names APT35, Charming Kitten, Mint Sandstorm, and Yellow Garuda, is a threat group linked to Iran’s Islamic Revolutionary Guard Corps (IRGC) that has been active since at least 2011. Most recently, Volexity highlighted the adversary’s use of an updated version of a Powershell implant called CharmPower (aka GhostEcho or POWERSTAR).
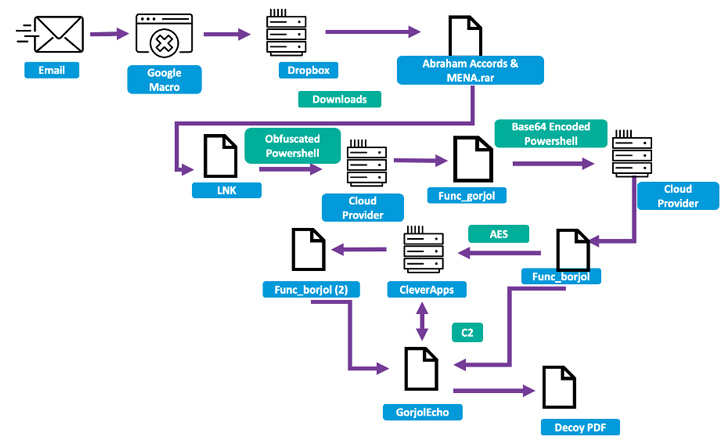
In the attack sequence discovered by the enterprise security firm in mid-May 2023, the hacking crew sent phishing emails to a nuclear security expert at a U.S.-based think tank focused on foreign affairs that delivered a malicious link to a Google Script macro that would redirect the target to a Dropbox URL hosting a RAR archive.
Present within the file is an LNK dropper that kicks off a multi-stage procedure to ultimately deploy GorjolEcho, which, in turn, displays a decoy PDF document, while covertly awaiting next-stage payloads from a remote server.
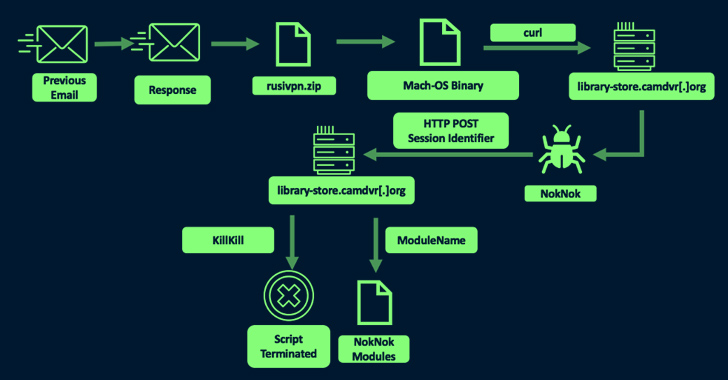
But upon realizing that the target is using an Apple computer, TA453 is said to have tweaked its modus operandi to send a second email with a ZIP archive embedding a Mach-O binary that masquerades as a VPN application, but in reality, is an AppleScript that reaches out to a remote server to download a Bash script-based backdoor called NokNok.
🔐 Privileged Access Management: Learn How to Conquer Key Challenges
Discover different approaches to conquer Privileged Account Management (PAM) challenges and level up your privileged access security strategy.
NokNok, for its part, fetches as many as four modules that are capable of…