Tag Archive for: MacOS
Fixing macOS Cannot Verify That This App is Free from Malware
/in Computer Security
A rather common error crops up when you try to run apps that aren’t from the Mac App Store. “macOS cannot verify that this app is free from malware” displays when you try to certain third-party applications. These apps, downloaded from outside the Mac App Store, are typically by developers who don’t register their apps with Apple. Unfortunately, even perfectly safe apps occasionally experience difficulties passing the security checks done by the macOS Gatekeeper security framework.
Nonetheless, our team found a fix for you. Follow along as we show you how to allow the app to run anyways. Yes, you can bypass and fix the “macOS cannot verify that this app is free from malware” error.
What Does Does the Message That macOS Cannot Verify That This App Is Free from Malware Mean?
Gatekeeper is a security technology included in macOS that helps guarantee only trustworthy software is allowed to run on a user’s Mac.
When a user downloads and opens an app, plug-in, or installation package from a source other than the App Store, Gatekeeper performs a check to ensure that the program is from an identified developer. It also ensures the program has not been changed, and is notarized by Apple to be free of known dangerous material.
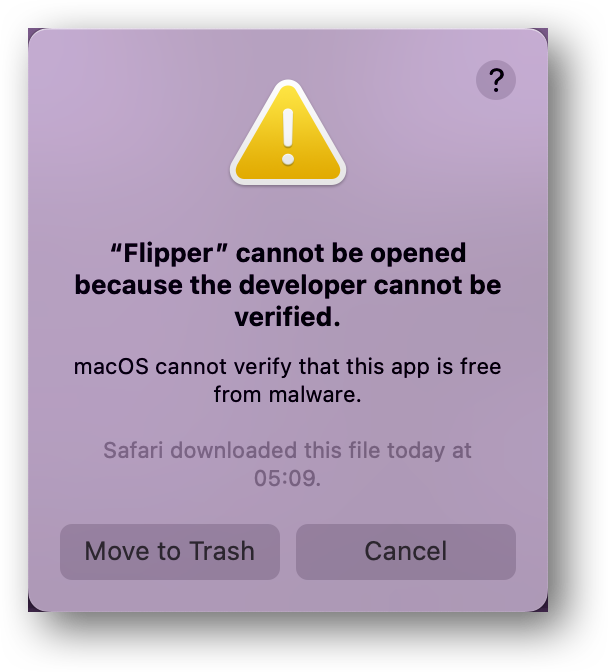
However, when these checks fail, you get an error that “macOS cannot verify that this app is free from malware.” When you attempt to install a third-party application from the Internet, Gatekeeper will not be able to confirm that the application does not include any forms of malicious software.
For example, a commonly used tool for debugging iOS, Android and React Native apps will throw such an error when you first try to run it.
“Flipper” cannot be opened because the developer cannot be verified.
macOS cannot verify that this app is free from malware.
How Do You Fix macOS Cannot Verify That This App Is Free from Malware?
It’s no surprise that there are dangers involved with running apps from unverified publishers. But if you trust the publisher or have the expertise to mitigate those risks, then you are free to open and install any program you wish.
Time needed: 1 minute.
To bypass Gatekeeper’s checks and install or run the app…
Microsoft reveals details about how it discovered a security flaw in macOS Gatekeeper
/in Mobile Security
Microsoft has revealed how it discovered a security flaw in macOS Gatekeeper. The vulnerability has been termed as Achilles.
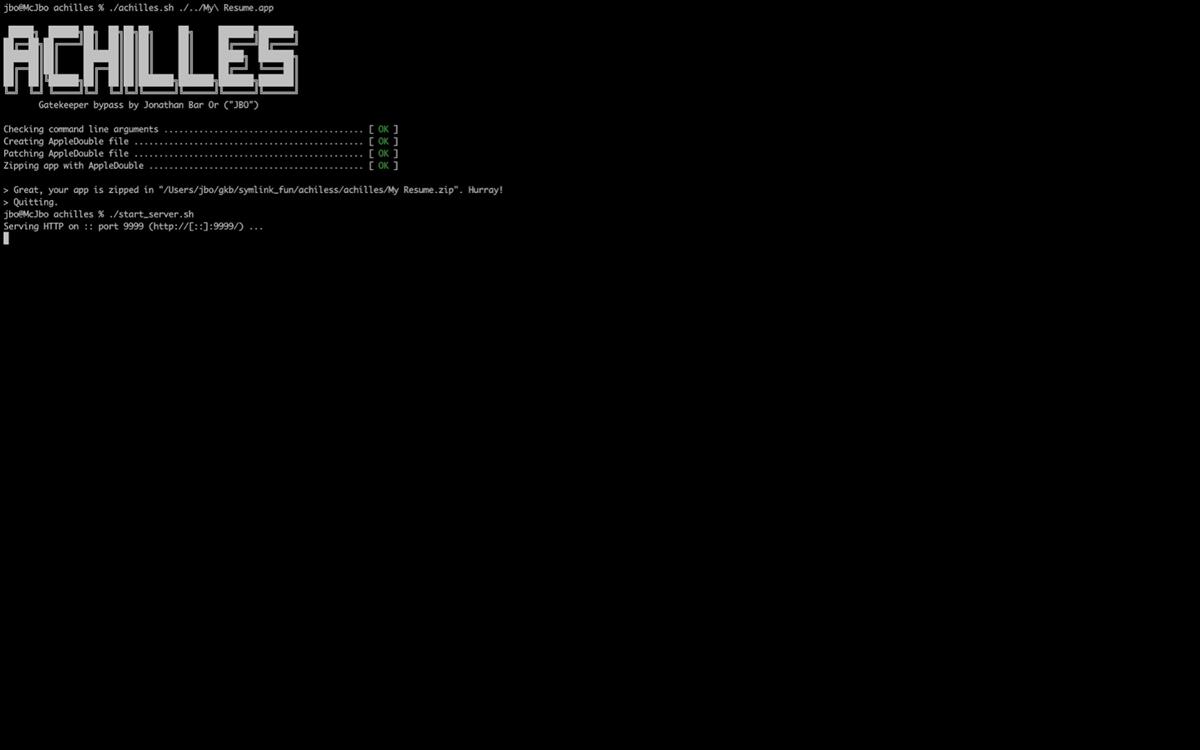
For those unaware, Gatekeeper is a security feature that protects your Mac, it does so by only allowing trusted software to run on it, it’s sort of like an antivirus. The security issue has been referenced as CVE-2022-42821. It has a severity rating of 5.5, which means it is a medium level threat.
Microsoft says that it analyzed the threat, and shared its findings with Apple in July through Microsoft Security Vulnerability Research, in order to help protect macOS users from potential attacks.
Apple patched the Achilles heel security flaw in macOS Ventura that was released on October 24th, and later in macOS Monterey 12.6.2 and macOS Big Sur 11.7.2, which were rolled out on December 13th. In its security notes, the Cupertino company had mentioned that the vulnerability could allow an app to bypass Gatekeeper checks, and that it a logic issue had been addressed with improved checks.
How Microsoft discovered the Achilles vulnerability in macOS
That doesn’t explain much, but an article on Microsoft’s security blog goes into the details. It is a bit on the technical side, so I’ll try to simplify it here. Microsoft says that macOS devices usually get infected as a result of users running fake apps that they may have downloaded from third-party sources, i.e. outside the App Store.
When a user downloads a file through their web browser, macOS assigns an extended attribute to it called com.apple.quarantine. The browser saves the metadata of a downloaded file in the above-mentioned attribute, and it contains some information such as flag;date;agent_name;UUID.
This is used by Gatekeeper to enforce some security policies. macOS usually warns you when you are trying to install something downloaded from the internet, that’s because Gatekeeper read its extended attribute, and recognized it as an app from an unknown source. After analyzing past security vulnerabilities that were present in macOS, Microsoft security researchers identified a specific one, referenced as CVE-2021-1810. The loophole, which was patched a year ago, would create a symbolic link to an app…
Apple issues patch for macOS security bypass vulnerability
/in Internet Security
Apple has fixed a vulnerability in macOS that could have allowed attackers to bypass application restrictions on the tech giant’s Gatekeeper mechanism.
The vulnerability, tracked as CVE-2022-42821 and dubbed ‘Achilles’, was first uncovered by researchers at Microsoft and shared with Apple through the Coordinated Vulnerability Disclosure (CVD) system.
Microsoft said the Achilles flaw could have enabled hackers to gain access to operating systems and download or deploy malware on Mac devices.
Apple confirmed it patched the bug on 13 December in its raft of security updates for macOS 13, macOS 12.6.2 and macOS 1.7.2.
Achilles exploited Apple’s Gatekeeper security mechanism used on Macs which is responsible for checking downloaded apps to ensure that they are legitimate, and works by requiring the user to confirm or authorise launching an app that might have been flagged by the mechanism.
Apple’s Gatekeeper system operates in a similar fashion to Microsoft’s own Mark of the Web (MOTW) protocols.
“When downloading apps from a browser, like Safari, the browser assigns a special extended attribute to the downloaded file,” researchers explained.
“That attribute is named com.apple.quarrantine and is later used to enforce policies such as Gatekeeper or certain mitigations that prevent sandbox escapes.”
Microsoft said the Achilles flaw would allow attackers to leverage targeted payloads to abuse Access Control Lists (ACLs) – a mechanism in macOS that offers additional protection to the standard permission model.
If exploited, the flaw meant that a malicious app downloaded by a user would launch on their system instead of being blocked by Gatekeeper.
Apple introduced Lockdown Mode in macOS Ventura to mitigate the risk of zero-click remote code execution (RCE) exploits. However, researchers noted that this optional feature for high-risk users would not defend against Achilles.
“End-users should apply the fix regardless of their Lockdown Mode status,” said Jonathan Bar Or of the Microsoft 365 Defender Researcher Team.
Gatekeeper vulnerabilities
Bar Or said that while Gatekeeper is “essential” in spotting malware on macOS, there have been…



