More malicious attachments found by researchers
Article content
Attachments continue to be an effective way of delivering malware as long as employees miss vital clues. Two examples detailed by researchers at Fortinet demonstrate the latest techniques of threat actors that can be shown to staff as part of security awareness training.
The first is a Word document containing a malicious URL designed to entice victims to download a malware loader. The payloads of this loader include OriginBotnet for keylogging and password recovery, RedLine Clipper for stealing cryptocurrency on a victim’s computer and AgentTesla for harvesting sensitive information.
Article content
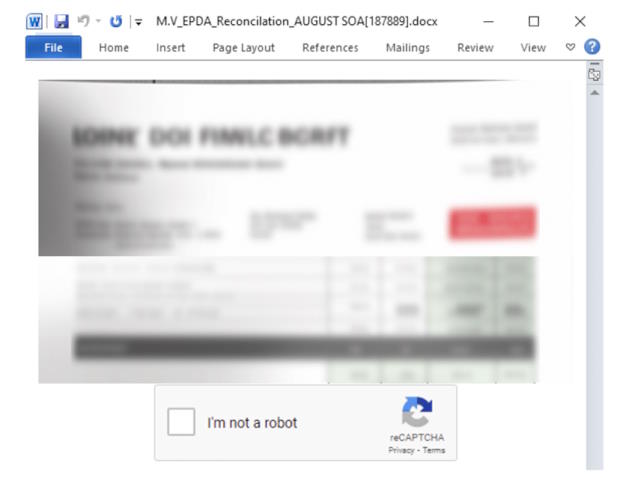
The example found by Fortinet is a financial document, but an attacker could use any tactic: A resume, a request for proposal, etc. Clicking on the Word document results in the display of a deliberately blurred image to convince the recipient there is a document to be seen if they also click on a counterfeit but standard-looking reCAPTCHA challenge that says “I am not a robot.” That starts a process for loading the malware.
RedLine Clipper, also known as ClipBanker, steals cryptocurrencies by manipulating the user’s system clipboard activities to substitute the destination wallet address with one belonging to the attacker. Due to the complexity of digital wallet addresses, users often copy and paste them during transactions.
Agent Tesla can log keystrokes, access the host’s clipboard, and conduct disk scans to uncover credentials and other valuable data. It transmits gathered information to a Command and Control (C2) server through several communication channels, including HTTP(S), SMTP, FTP, or even by dispatching it to a designated Telegram channel.
Article content
OriginBotnet has a range of capabilities including collecting sensitive data, establishing communications with its C2 server, and downloading additional files from the server to execute keylogging or password recovery functions on compromised computers.
The second example is a file the researchers obtained that they assume was an attachment because it purports to be a list of company…