‘TheMoon’ malware shows its dark side, grows to 40,000 bots from 88 countries
A multi-year campaign leveraging an updated version of “TheMoon” malware has been targeting end-of-life (EoL) small business routers and IoT devices via a cybercriminal proxy service known as “Faceless.”
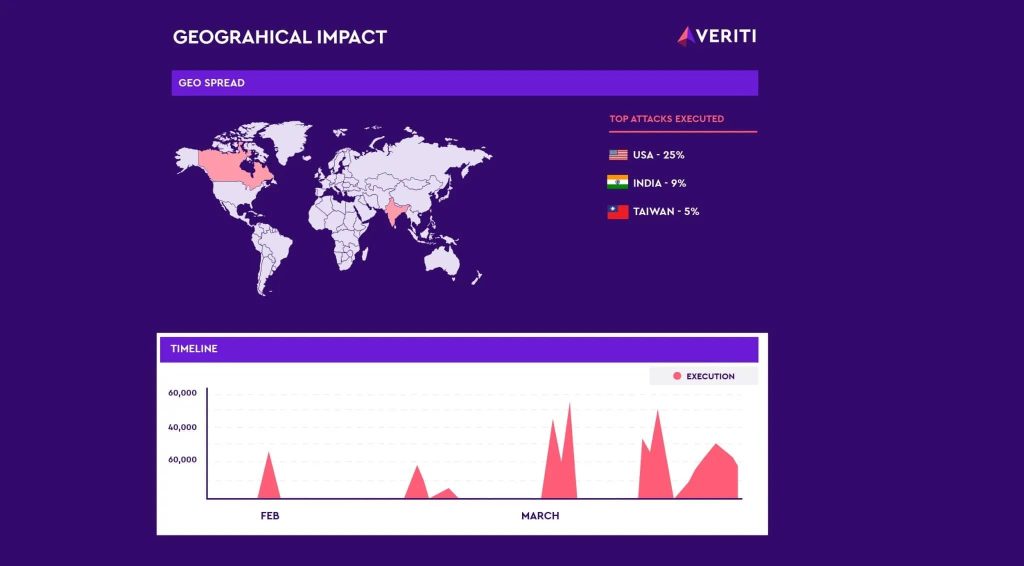
The Black Lotus Lab team at Lumen Technologies described in a March 26 blog post that they found that “TheMoon” malware, which first emerged in 2014, was operating quietly while growing to more than 40,000 bots from 88 countries by January and February of this year.
Black Lotus Labs first described “TheMoon” malware in 2019 and said it has entered a new phase. For their most recent post, the researchers identified at least one campaign by the Faceless criminal proxy service that began in the first week of March which targeted more than 6,000 ASUS routers in less than 72 hours.
The researchers said Faceless has been growing at a pace of 7,000 users per week and has become an ideal choice for cybercriminals seeking anonymity. The researchers said their telemetry found that this service has been used by operators of botnets such as SolarMarker and IcedID.
“This is not the first instance of infected devices being enrolled into a proxy service, and it’s a growing trend,” wrote the researchers. “We suspect that with the increased attention paid to the cybercrime ecosystem by both law enforcement and intelligence organizations, criminals are looking for new methods to obfuscate their activity.”
John Gallagher, vice president of Viakoo Labs, said that IoT devices are designed to be “set-it-and-forget-it,” leading to their being favored by threat actors. So even if they are not EoL, they are likely unmanaged and not updated.
“This is a much bigger issue for enterprises than consumers,” explained Gallagher. “The operators of IoT devices are often cost centers, and have an incentive to not replace equipment unless it isn’t functional anymore. So, enterprises offer vast fleets of IoT devices for threat actors to leverage for DDoS and other attack vectors.”
The result: Gallagher said we now have vast botnet armies of infected IoT devices because there has never been a focus (or incentive) around bot eradication. He said organizations are told to focus on bot…