Tag Archive for: MFA
Cyber Security Today, April 15, 2022 – A new botnet discovered, low MFA adoption and a Struts bug finally patched
/in Internet Security
A new botnet discovered, low MFA adoption and a Struts bug finally patched.
Welcome to Cyber Security Today. It’s Friday April 15th, 2022. I’m Howard Solomon, contributing reporter on cybersecurity for ITWorldCanada.com. Thanks for taking the time to tune in if this is a holiday Friday for you.
 
A new denial of service botnet has been discovered by security researchers in China. Called Fodcha, it’s adding 100 new infected devices to the estimated 62,000 enslaved devices already on the network. Most are in China. Devices are being compromised by Fodcha malware either through known vulnerabilities or weak passwords on Android servers, GitLab accounts and certain brands of routers. Some are made by Totolink. Last week I reported that another botnet was also compromised of certain unpatched models of Totolink routers.
I regularly quote cybersecurity experts saying implementing multifactor authentication is one of the best things IT leaders can do to lower the risk of a successful cyberattack through compromised passwords. So, here are some disturbing numbers from a report released this week by Trellix: Less than half of U.S. government agency respondents to a survey said their organization has fully developed MFA. At least that’s better than the critical infrastructure sector — which includes banks, transportation companies and utilities. Only 37 per cent of American firms in that sector had implemented MFA. Guest commentator Terry Cutler and I will talk about MFA and other identity management technologies in the Week in Review podcast later today.
Apache has admitted a fix for the Struts Java web application development platform issued two years ago didn’t do the job. It has now put out what it says is a patch that solves the problem. It’s serious enough that the U.S. Cybersecurity and Infrastructure Security Agency is urging users to upgrade to version 2.5.30.
Attention hospital IT administrators: If your facility uses the Aethon TUG wireless smart robot cart for delivering medicine or maintenance supplies, the Homebase server needs to be patched. Researchers at Cynerio have discovered five vulnerabilities that could allow an attacker to take remote…
Aware teams with MFA provider to fight ransomware, makes $2.5M strategic investment
/in Internet Security

Aware has formed a partnership with Miracl, which provides multi-factor authentication through a single step, and made a $2.5 million investment in its new partner’s parent company Omlis Limited, as it seeks to apply its biometrics to minimizing risk from data breaches and ransomware.
The partnership is expected to enable Aware to extend its cloud-based biometric authentication to customers in financial services and other industries to protect against data breaches and ransomware, through a mutual reseller agreement, according to the announcement. Miracle contributes risk management functionality to Aware’s solutions portfolio, and makes its “adaptive authentication” services more varied to fit specific customer needs.
“Data breaches and ransomware are continuing to wreak havoc on enterprises, and recent high-profile attacks like the Colonial Pipeline are reminders of the escalating threats we continue to face,” says Bob Eckel, chief executive officer and president of Aware. “In many cases, government agencies are calling on organizations to pursue multifactor authentication (MFA) to enhance their security. To date, many defenses against cybercrimes have relied on zero knowledge trust, which has several disadvantages; or traditional passwords, which are prone to login errors and irritating reset requirements. With MFA that incorporates biometrics, organizations can now have unprecedented protection and user privacy without the risks or frustrations of other approaches. This technology we now have available is an important and effective tool against these sorts of attacks.”
The partners can sell each other’s technologies and integrate them into their own product lines under the agreement, which will allow them to bring passwordless login products to market quickly.
Miracl gains access to Aware’s affordable, high-performance biometrics to provide a more extensive range of authentication capabilities along with its flagship authentication and transaction-signing solution, Miracl Trust.
“Ransomware attacks have increased more than 150 percent between the first six months of 2021 compared to the same period the previous year. MFA is…
Android malware Escobar steals your Google Authenticator MFA codes
/in Mobile Security

The Aberebot Android banking trojan has returned under the name ‘Escobar’ with new features, including stealing Google Authenticator multi-factor authentication codes.
The new features in the latest Aberebot version also include taking control of the infected Android devices using VNC, recording audio, and taking photos, while also expanding the set of targeted apps for credential theft.
The main goal of the trojan is to steal enough information to allow the threat actors to take over victims’ bank accounts, siphon available balances, and perform unauthorized transactions.
Rebranded as Escobar
Using KELA‘s cyber-intelligence DARKBEAST platform, BleepingComputer found a forum post on a Russian-speaking hacking forum from February 2022 where the Aberebot developer promotes their new version under the name ‘Escobar Bot Android Banking Trojan.’
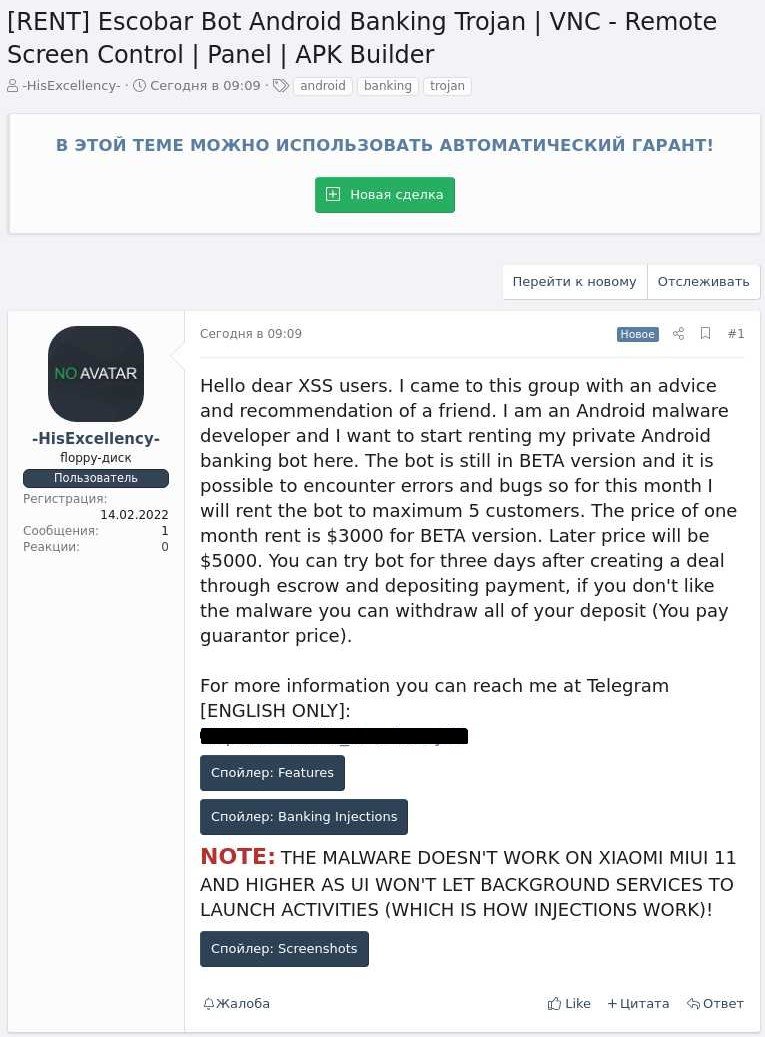
The malware author is renting the beta version of the malware for $3,000 per month to a maximum of five customers, with threat actors having the ability to test the bot for free for three days.
The threat actor plans on raising the malware’s price to $5,000 after development is finished.
MalwareHunterTeam first spotted the suspicious APK on March 3, 2022, masqueraded as a McAfee app, and warned about its stealthiness against the vast majority of anti-virus engines.
Possible interesting, very low detected “McAfee9412.apk”: a9d1561ed0d23a5473d68069337e2f8e7862f7b72b74251eb63ccc883ba9459f
From: https://cdn.discordapp[.]com/attachments/900818589068689461/948690034867986462/McAfee9412.apk
“com.escobar.pablo”
pic.twitter.com/QR89LV4jat— MalwareHunterTeam (@malwrhunterteam) March 3, 2022
This was picked up by researchers at Cyble, who performed an analysis of the new ‘Escobar’ variant of the Aberebot trojan.
According to the same analysts, Aberebot first appeared in the wild in the summer of 2021, so the appearance of a new version indicates active development.
Old and new capabilities
Like most banking trojans, Escobar displays overlay login forms to hijack user interactions with e-banking apps and websites and steal credentials from victims.
The malware also packs several other features that make it…



