How the Modern Data Landscape Made the Traditional Cybersecurity Approach Obsolete
From the news headlines, we know that data breaches are on the rise – both in frequency and scale. While this reality is unsettling, it’s not surprising. That is because the volume of data being collected and stored by organizations continues to grow exponentially each year. Every day, the global population creates 2.5 quintillion bytes of data, and some estimates state that by the end of 2022, 97 zettabytes (one zettabyte is one trillion gigabytes) of data will be created, captured, copied, and consumed worldwide.
This data is valuable and, therefore, attractive to cybercriminals to steal or manipulate to conduct fraud, sell on, or hold for ransom. Organizations are well aware of the threats to data and invest heavily in cybersecurity measures. However, despite this, data breaches continue to occur. To understand why we need to look at how the data landscape has changed in the last decade and how that has made traditional cybersecurity frameworks and playbooks obsolete.
The data landscape pre-2010
Before 2010 and the mass internet adoption spurred on by the invention of the smartphone, organizations had a relatively well-defined and controlled footprint of people, processes, and technology that were used to capture, process, and store data.
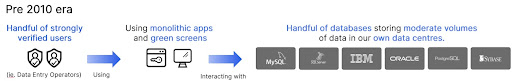
At that time, data was still largely collected using paper. This data was generally provided to a handful of employees (i.e. Data Entry Operators) who had been strongly verified by the organization. They entered this data into monolithic and green screen applications, which stored the data in a handful of enterprise databases that were available at the time. All this was largely run within the organization’s own data centers, under the control of their IT and security teams.
The data landscape post-2010
Mass adoption of the internet and the digitization of the economy since 2010 have seen a significant shift in our data practices and processes.
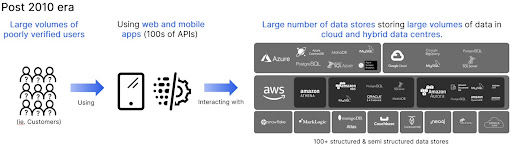
Today we have hundreds or even thousands of people (ie. customers), entering data via web and mobile apps. These users are poorly verified, often requiring as little as an email address to get access. Gone are the centralized monolithic and green screen applications, replaced by web and…




