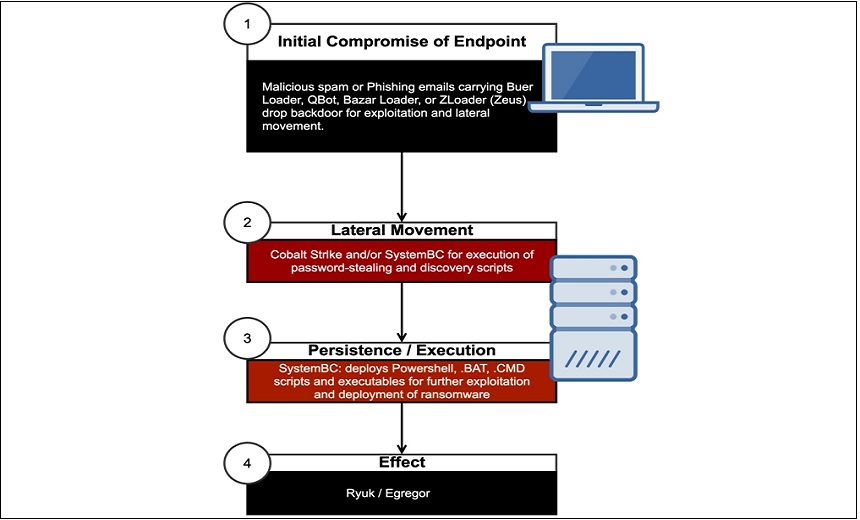
Infobip acquires Anam to offer enhanced product and service offerings for mobile network operators
Infobip announces it has acquired SMS firewall service provider Anam that offers solutions to more than 80 MNOS with more than 606 million customers across the world. The purchase price remains undisclosed and consists of a combination of cash and Infobip shares.
This strategic acquisition strengthens Infobip’s position as the first choice for mobile network operators through enhanced product and service offerings.
Their combined product portfolio for MNOs represents an exceptional proposition to mobile operators that will also vastly benefit subscribers, and includes best in class SMS Firewall, SMS Hubs, SMSC, CPaaS, RCS and Authentication & Verification.
With Anam joining Infobip’s Strategic Operator Partnerships division, customers of both companies will benefit from a better all-up offering including 24/7 Networks Operations Centre (NOC), on ground support, enriched analytics, and reporting.
Additionally, it offers greater scale through Infobip’s truly global presence and direct relationship with over 650 carriers across the world. Together Anam and Infobip’s combined assets secure the best supply chain available today for A2P SMS globally.
The companies will now be able to provide technical solutions to a combined 700+ MNOS globally with 64% global mobiles reached. Infobip processes more than 14 billion monthly customer interactions across the full range of communication channels, in more than 190 countries around the globe.
Both companies are active GSMA associate members and have consistently ranked Tier 1 in ROCCO’s A2P SMS Firewall vendor benchmarking reports. Both are also recipients of Juniper Future Digital Awards in their respective fields making this a highly complementary union.
Anam is also one of the few companies that hold certification of both ISO 27001 and ISO 20000 – best practice standards for information security and IT service management – that guarantee premium levels of Quality of Service to operators.
Culturally, both businesses have closely matched company values and beliefs –abiding by a team-based ethos which emphasizes employee…