Update Zoom right now, major security flaw patched
Zoom has rushed out an important update for its macOS app, which patches a big security hole. The fix is for the auto-update process, which could let an attacker take over your system.
The issue was first found by a security researcher, Patrick Wardle. A combination of issues adds up to anyone being able to get root (superuser privileges) without a password on a Mac computer.
The attack was interesting enough for Wardle to present at Def Con, one of the premier hacking conferences, in Las Vegas last week. Zoom had already fixed some of the issues before his talk, with the remainder fixed shortly afterward.
🆕 Update(s):
🐛 Bug assigned CVE-2022-28756
🩹 Patch now available, in Zoom v5.11.5 (9788)See Zoom’s security bulletin: https://t.co/xUpE4jS6ck
Mahalos to @Zoom for the (incredibly) quick fix! 🙌🏽 🙏🏽 pic.twitter.com/GGtM3EUT7s
— patrick wardle (@patrickwardle) August 14, 2022
Again, if you’re a macOS user who has Zoom installed, go look for an update. The fix is included in version 5.11.5 of the Zoom client.
According to Wardle, who spoke to The Verge last week, he disclosed the bugs to Zoom almost eight months ago. He even told them what needed to be done to fix the issues.
If attackers had wanted, they could have used the privilege escalation in Zoom to do almost anything they wanted on the target Mac. That includes installing more programs, modifying, deleting, or sending data to a remote device.
How to update Zoom
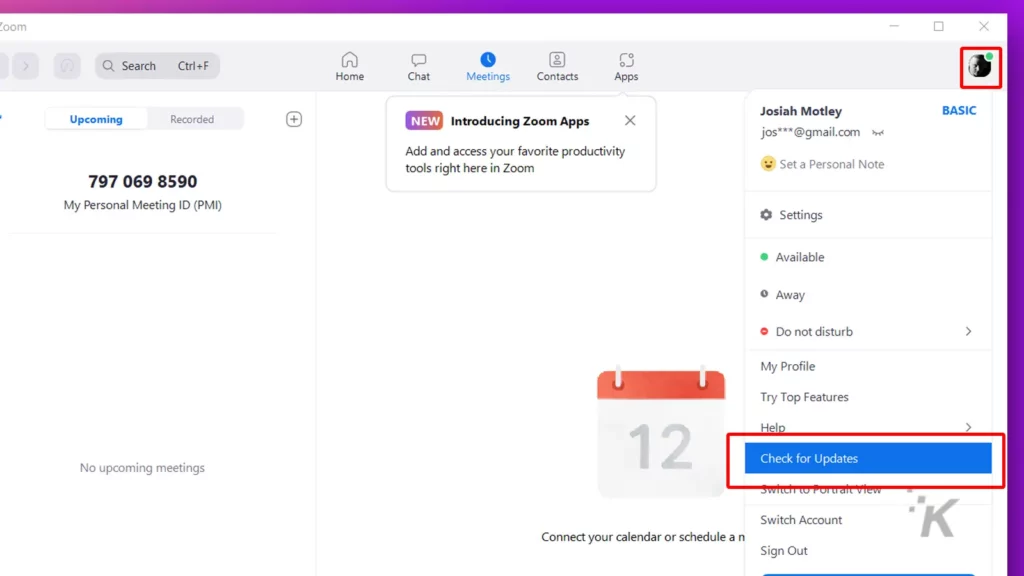
You can check to see if any updates are available for Zoom by clicking your profile icon on the app and finding “Check for Updates” in the dropdown list. For additional help, you can watch Zoom’s own video tutorial here.
If you are on any version lower than 5.11.5, it’s time to update. You’ve already been at risk for the best part of a year, don’t let that continue any longer.
Have any thoughts on this? Let us know down below in the comments or carry the discussion over to our Twitter or Facebook.
Editors’ Recommendations: