Popular Social Media App Discord Clamps Down To Fight Cyber Attacks – Forbes Advisor
Editorial Note: We earn a commission from partner links on Forbes Advisor. Commissions do not affect our editors’ opinions or evaluations.
Multimedia social platform Discord is cracking down on malicious links, known as malware, by activating stronger security measures. From now on, Discord links that are shared outside the platform will expire after 24 hours. The goal is to lessen users’ exposure to malware, making it harder for identity thieves to steal users’ personal and financial information.
Hackers commonly exploit Discord servers to host malicious files and distribute malware. Malware can include spyware, key-loggers and viruses that infect users’ computers and reveal personal data and access codes, enabling identity theft and other crimes. In the past, familiarity with the Discord brand has often led users to click seemingly safe links that turned out to be malware, bringing on a cyberattack.
The new 24-hour expiration feature will only apply to links shared outside of Discord. Within Discord, shared file links will update automatically, so internal users can access files without the threat of expiration.
“There is no impact for Discord users that share content within the Discord client. Any links within the client will be auto-refreshed,” said Discord communications manager Hannah Stabingas.
Stabingas said the new measures, rolling out in December 2023 and early 2024, will enhance privacy and security for the app’s 150 million-plus active monthly users.
“This will help our safety team restrict access to flagged content and generally reduce the amount of malware distributed using our CDN (content delivery network),” Stabingas said.
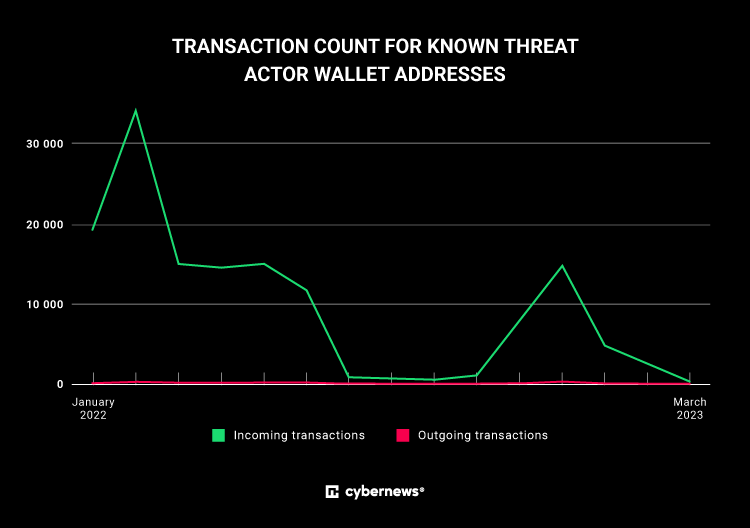
Malware has been an ongoing problem for Discord. According to Discord’s latest transparency report, during the third quarter of 2023, 11,885 accounts and 2,389 servers were removed from the platform for deceptive practices. These practices include malware, fraud and scams, according to the report.
Cybersecurity expert Jake Williams, a faculty member at the Institute for Applied Network Security (IANS), says the new changes will likely be…