Critical Remote Hack Flaws Found in Dataprobe’s Power Distribution Units
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday released an industrial control systems (ICS) advisory warning of seven security flaws in Dataprobe’s iBoot-PDU power distribution unit product, mostly used in industrial environments and data centers.
“Successful exploitation of these vulnerabilities could lead to unauthenticated remote code execution on the Dataprobe iBoot-PDU device,” the agency said in a notice.
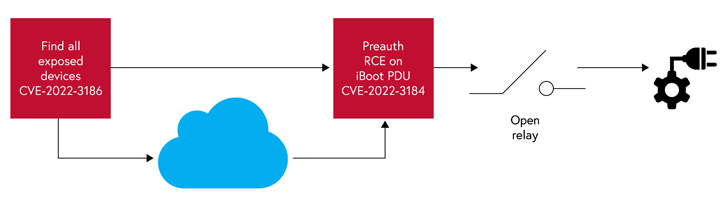
Credited with disclosing the flaws is industrial cybersecurity firm Claroty, which said the weaknesses could be remotely triggered “either through a direct web connection to the device or via the cloud.”
iBoot-PDU is a power distribution unit (PDU) that provides users with real-time monitoring capabilities and sophisticated alerting mechanisms via a web interface so as to control the power supply to devices and other equipment in an OT environment.
The vulnerabilities assume new significance when taking into consideration the fact that no fewer than 2,600 PDUs are accessible on the internet, with Dataprobe devices accounting for nearly a third of those exposed, according to a 2021 report from attack surface management platform Censys.
Claroty’s analysis of the PDU firmware shows that the product is crippled by issues ranging from command injection to path traversal flaws, exposing customers to severe security risks –
- CVE-2022-3183 (CVSS score: 9.8) – A command injection vulnerability stemming from a lack of sanitization of user input
- CVE-2022-3184 (CVSS score: 9.8) – A path traversal vulnerability that enables access to an unauthenticated PHP page, which could be abused to insert malicious code
Successful remote exploitation of the flaws “puts an attacker within arm’s length of disrupting critical services by cutting off electric power to the device and subsequently, anything plugged into it,” Claroty researcher Uri Katz said.
The other five uncovered vulnerabilities (from CVE-2022-3185 through CVE-2022-3189) could be weaponized by a bad actor to access the device’s main management page from the cloud and even trick the server to connect to arbitrary internal or external systems (aka SSRF), potentially leaking sensitive information.
“Even…