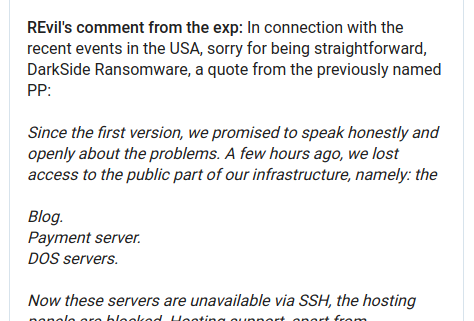
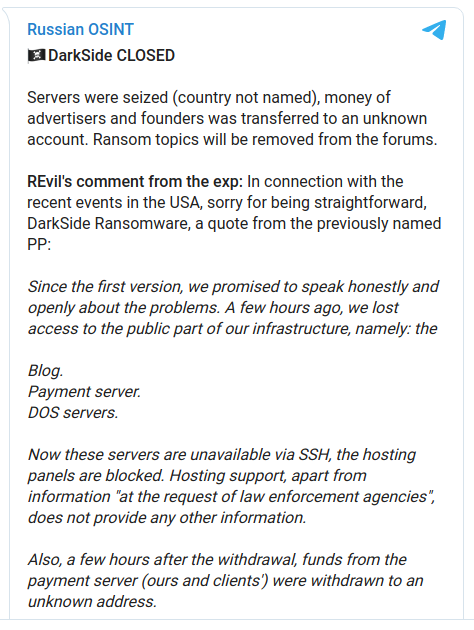
There are a number of exceptions to warrant requirements, and the government is willing to utilize every one of them to salvage evidence obtained from an illegal search. Sometimes the arguments work. Other times — like in this instance where six years elapsed between searches — there’s no credible argument for failing to seek a warrant. (via FourthAmendment.com)
Jason Gandy’s cellphone was seized and searched “at an international border” in 2012. The phone was held for 48 hours for a forensic search. This did not reveal the contents of the phone, but created an electronic record of what was contained on the phone. The court’s description says the search only produced a “technical description” of the phone’s contents, but did not expose the contents themselves.
Like it or not, this search — even a forensic search — fell under the “border exception” to the Fourth Amendment, which allows law enforcement to search devices for border/national security reasons without having to come up with reasonable suspicion, much less probable cause.
That search was lawful. It was the second search that broke the rules, including one handed down by the Supreme Court in 2014. From the decision [PDF]:
In July 2018, six years after the initial border search, the government conducted a warrantless search of Gandy’s cell phone. On July 11 and 13, 2018, the government produced to the defense the evidence discovered during the search and stated the intent to offer the evidence as evidence.
Maybe the government thought it was grandfathered in to the pre-Riley warrantless phone search standard. Maybe the government just didn’t care. Maybe it thought the long list of exceptions would save it, especially the one related to searches at international borders. But it definitely realized it had screwed up when Gandy moved to suppress the evidence, because it did this:
On July 13, after Gandy moved to suppress the newly produced text messages, the government applied for and obtained a warrant to search the phone. The agent who signed the search-warrant affidavit was not the same agent who conducted the 2012 search. The affidavit merely states that the cell phone had been in the Department of Homeland Security’s custody since it was seized at the border in 2012.
The government argued it could perform a warrantless search six years after the phone was seized while nowhere near the border under the border search exception. The court responds with, “Well, why don’t we just get rid of the Fourth Amendment altogether, then?”
The government’s second, warrantless search of Gandy’s phone did not occur at a border or at the time of the crossing. It happened six years after Gandy returned to the United States after being denied entry to the United Kingdom. Gandy and his phone have both been in custody since 2012, within the United States. Searching Gandy’s phone had no connection to the government’s interest in preventing illegal entry or contraband smuggling at an international border. Extending the border-search exception to the government’s warrantless search would “both undervalue the core Fourth Amendment protection afforded” cell phones under Riley and “‘untether’ the [border-search] exception ‘from the justifications underlying it.’”
The court also notes that holding a phone for six years before performing a warrantless search removes any question of “exigency” from the discussion. It also refuses to entertain the government’s “independent source” argument.
The independent source doctrine does not apply. The government has not shown that the search done—again—after the government got the search warrant was untainted by the earlier, warrantless search. […] The government has not shown that “there is a reasonable probability that the contested evidence would have been discovered by lawful means in the absence of police misconduct.”
And there’s no “good faith” here either. The law was completely settled by the time agents warrantlessly searched Gandy’s phone.
The good-faith exception does not apply to the government’s second, warrantless search of Gandy’s phone. That search occurred in July 2018. Under the “law existing at the time of [the July 2018] unconstitutional search,” it is clear that the search was not justified by the border-search exception. The government conducted the search years after the Riley Court clearly held that “what police must do before searching a cell phone seized incident to an arrest is accordingly simple—get a warrant.”
It’s a strong opinion that expresses very clearly the multiple ways the government screwed up. Unfortunately, the “border exception” remains intact. This allows the government to seize devices, hold onto them for months or years, and search them at its leisure. If the border exception were truly about preventing the smuggling of contraband or drug/human trafficking, you’d think searches would be performed as soon as possible, rather than allowing more than a half-decade to elapse between searches. But as long as people’s property remains solely in the control of the government, the more likely it is that searches will be performed whether or not the government truly has an articulable reason to do so.
Permalink | Comments | Email This Story
Techdirt.