New malware seizes on COVID-19 to target Android users
(CBS)
A new form of malware that experts are referring to as “TangleBot” is relying on interest in COVID-19 to trick Android users in the U.S and Canada into clicking on a link that will infect their cell phones, according to analysts at the mobile and email security company Cloudmark.
Cloudmark says the “clever and complicated” malware sends Android users a text message claiming to have the latest COVID-19 guidance in their area or informs them that their third COVID-19 vaccine appointment has been scheduled. When users click on the link provided, they’re prompted to update their phone’s Adobe Flash player, which instead installs the virus on their phone, according to Cloudmark.
Here’s what such a text message might look like, according to Cloudmark:
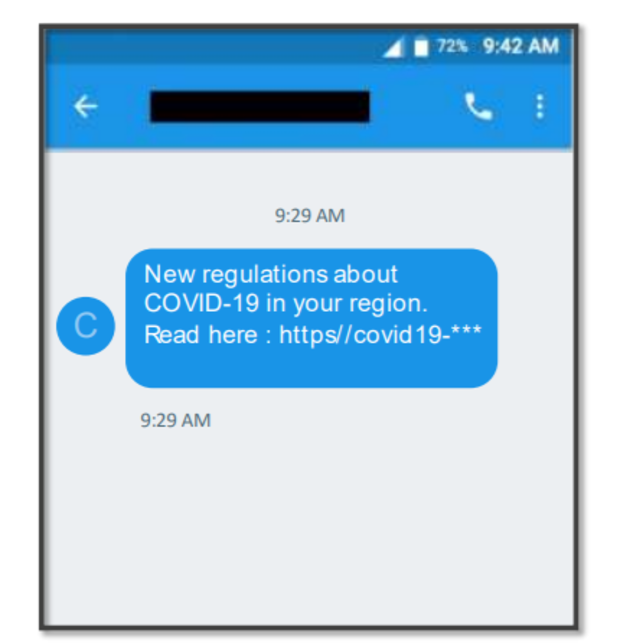
“Once that happens, the TangleBot malware can do a ton of different things,” Ryan Kalember, executive vice president of cybersecurity at Cloudmark’s parent company ProofPoint, told CBS News. “It can access your microphone, it can access your camera, it can access SMS, it can access your call logs, your internet, your GPS so it knows where you are,” Kalember added.
Kalember said the hackers have been using TangleBot for “weeks” and that the impact could potentially be “very widespread.” However, Android does have some protections in place against the virus. Prior to downloading the malware, users are warned by Android about the dangers of software from “unknown sources” and a series of permission boxes are displayed before the phone is infected.
“What is making TangleBot fairly interesting right now is that they are using incredibly fresh lures that all map to the sorts of things that we’re hearing about in the news with COVID, whether we are talking about the booster or other things that you are likely to see on the front page of whatever news site you go to,” Kalember said.
According to Kalember, the TangleBot malware has the capability to show hacked users an “overlay” screen that appears authentic but is instead a fake…


