Microsoft Teams users warned that hackers are using it to spread malware
Microsoft Teams users have been warned of hackers spreading malicious programs into conversations on the app.
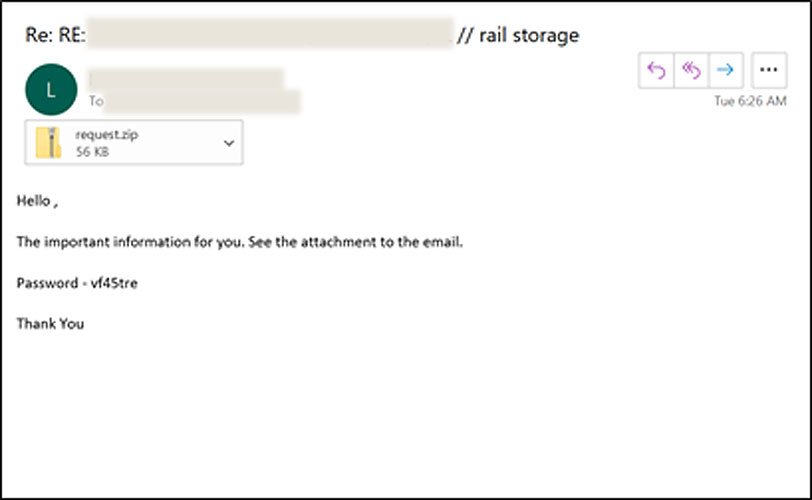
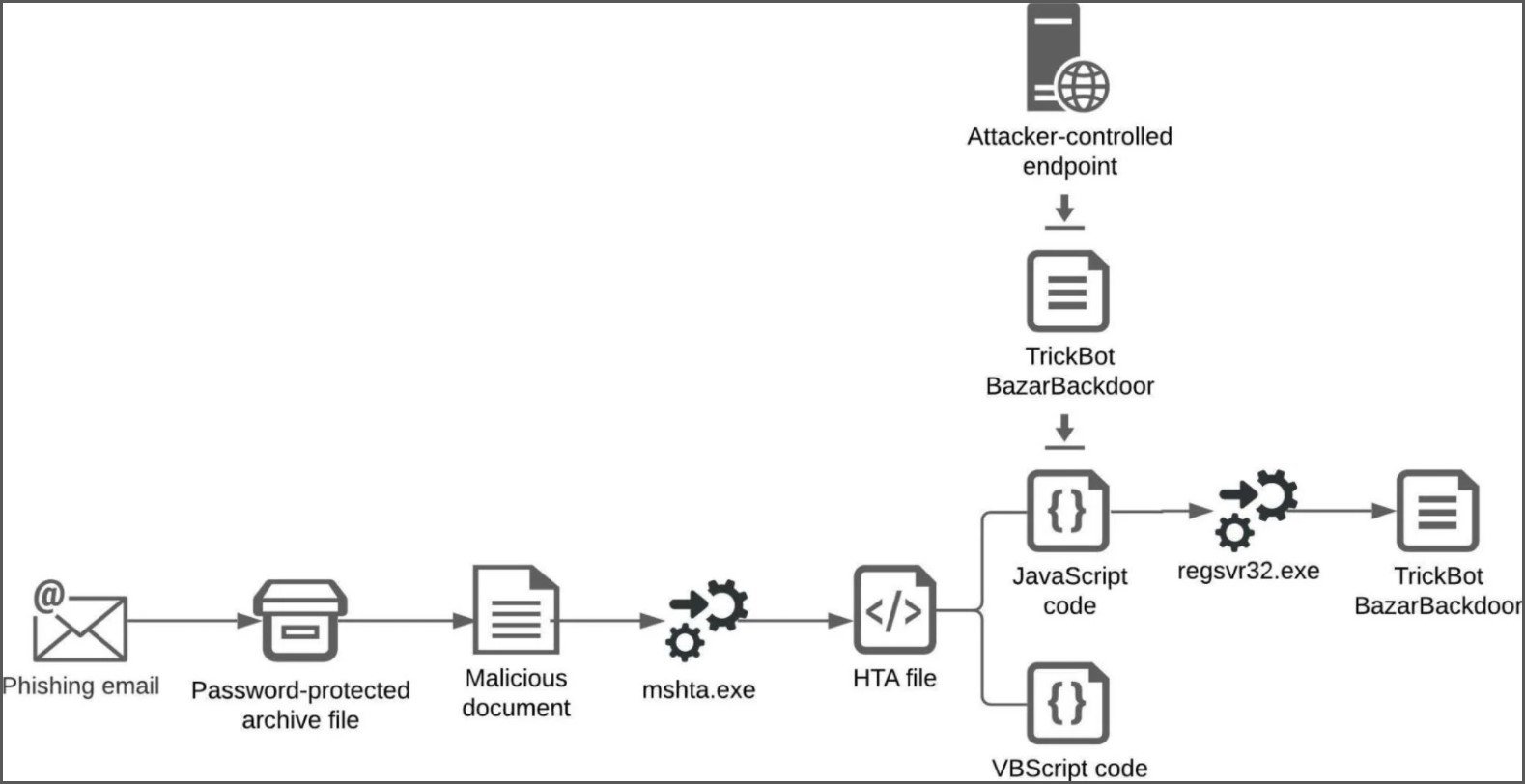
The files, which have the .exe format, write data to the Windows registry, installs DLL files and creates shortcut links that allow the program to self-administer, cloud security firm Avanan warns.
The company has apparently seen thousands of these attacks in the past month, inflicted on a minority of the 270 million monthly active Teams users.
The hackers are using the programs to Teams chats to install a Trojan on the end-users computer. This program can then be used to install malware when clicked on.
Once this has been achieved, the hackers can compromise an email address and use that to access Teams.
If used with another phishing campaign, they could get access to Microsoft 365 credentials.
“Compounding this problem is the fact that default Teams protections are lacking, as scanning for malicious links and files is limited. Further, many email security solutions do not offer robust protection for Teams,” cyber security researcher and analyst Jeremy Fuchs said.
“Hackers, who can access Teams accounts via East-West attacks, or by leveraging the credentials they harvest in other phishing attacks, have carte blanche to launch attacks against millions of unsuspecting users.”
Since many people may still be unfamiliar with the Teams platform, many people will just trust and approve hackers’ requests for access – especially if they pretend to be the chief executive or IT support.
People have been trained to second-guess identities in email, but it is easy to edit the name and appearance of a Teams profile making it easier to gain the trust of the unsuspecting.
Avanan recommends that security professionals implement protection that downloads all files in a sandbox and inspects them for malicious content and encourage users to seek support if they come across an unfamiliar file.