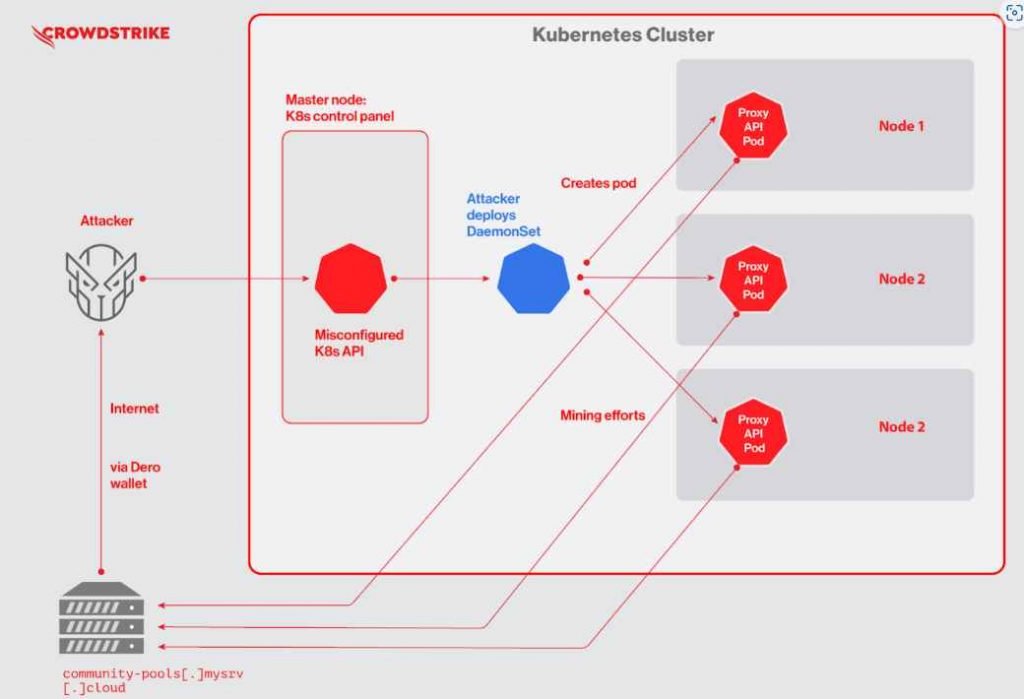
Hackers Use “chatgpt5[.]zip” to Trick Users into Download Malware
Hackers Use “chatgpt5 [.]zip” to Trick Users into Downloading Malware. Phishing remains a severe cybersecurity threat, deceiving employees with cleverly disguised malicious links and malware attachments, potentially causing company-wide troubles for over a decade.
The 2022 FortiGuard Labs report and the 2023 Global Ransomware Research both highlight phishing as the leading initial access method in network breaches, setting the stage for subsequent attack stages.
Threat actors employ creative names to disguise phishing attacks, with a new TLD ‘ .ZIP’ introducing a potential threat by chatgpt5 leading to malicious sites.
Reach Expansion
TLDs are vital components of domain names, like ‘.COM,’. ‘NET,. ‘ ‘.ORG,’ represents the highest level in the DNS hierarchy, shaping the structure of the web.
With internet evolution, countless gTLDs emerged for personalized web addresses, offering branding chances but also phishing opportunities that demand alertness.
The availability of public ‘.ZIP’ domains has created an unfortunate opportunity for the threat actors seeking new exploits and techniques.
The inclusion of ‘.ZIP’ as a gTLD adds complexity to phishing detection, particularly due to its association with compressed files, increasing confusion and providing phishers with a potent new tool for their attacks.
Exploiting ChatGPT
The cybersecurity researchers acknowledge the security risks of the ‘.ZIP’ TLD, but responsible individuals are actively working to mitigate the abuse of such domain names.
The hype around ChatGPT lead to the creation and registration of “chatgpt5 [.]zip ” on May 20th, supposedly for the next GPT iteration, but surprisingly, it holds a neutral text message instead of malware.
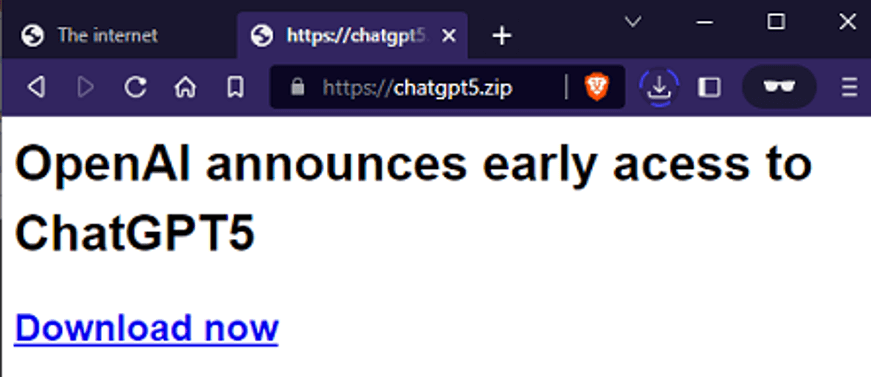
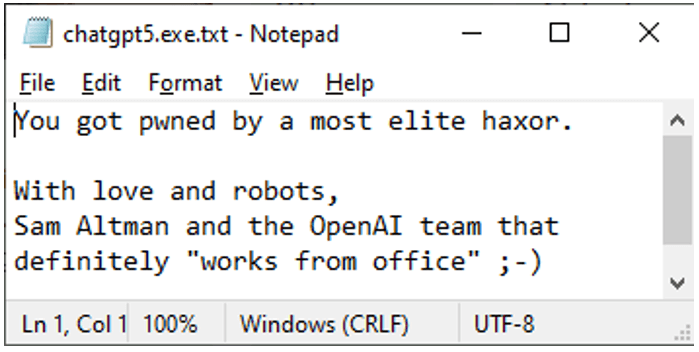
To trick the users by claiming to safeguard students from malware, “assignment[.]zip” was registered by the threat actors on May 15th, redirecting visitors to a download of a ZIP archive containing files that are completely safe.
Exploiting the widespread use of the .ZIP extension, malicious actors create campaigns and websites reminiscent…