10 Helpful Tools You Can Unlock Using Google Search, Google Assistant, or the Google App on Your Phone « Smartphones :: Gadget Hacks
Google has a few hidden tools you might not have discovered yet, and they work in Google Search, in the Google app, and with Google Assistant — on both iPhone and Android phones.
We all know smartphones do much more than make phone calls. They serve as cameras, GPS navigators, music players, portable televisions, web browsers, and even flashlights, making other gadgets that serve those singular purposes nearly obsolete.
But your phone can replace other tools, such as dice, guitar tuners, and bubble levels, with assistance from Google. And you don’t need to install an app to access them unless you want to use the Google or Google Assistant app and don’t already have one of them (many Android phones come with at least one preinstalled).
Google Search Tools
These tools below are accessible on your iPhone or Android phone by performing a Google search in your browser at google.com or by searching in the free Google app for iOS or Android. Some of them can even be called up with Google Assistant.
When searching for these tools, you can tap the button with the downward-pointing chevron to find the other available tools. You’ll see a tab for games and toys, but we’re currently focusing on the tools. All but one of these tools are also accessible via desktop browsers.
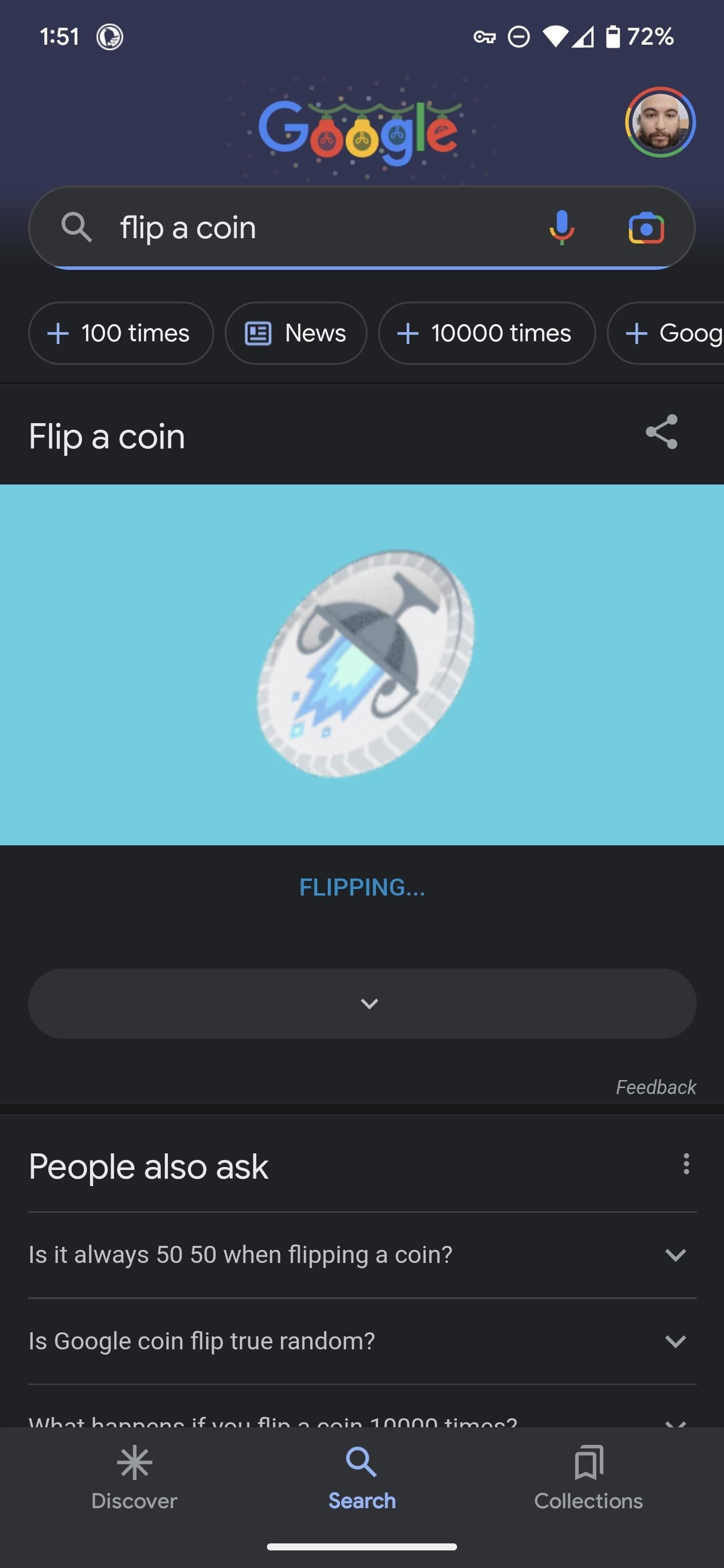
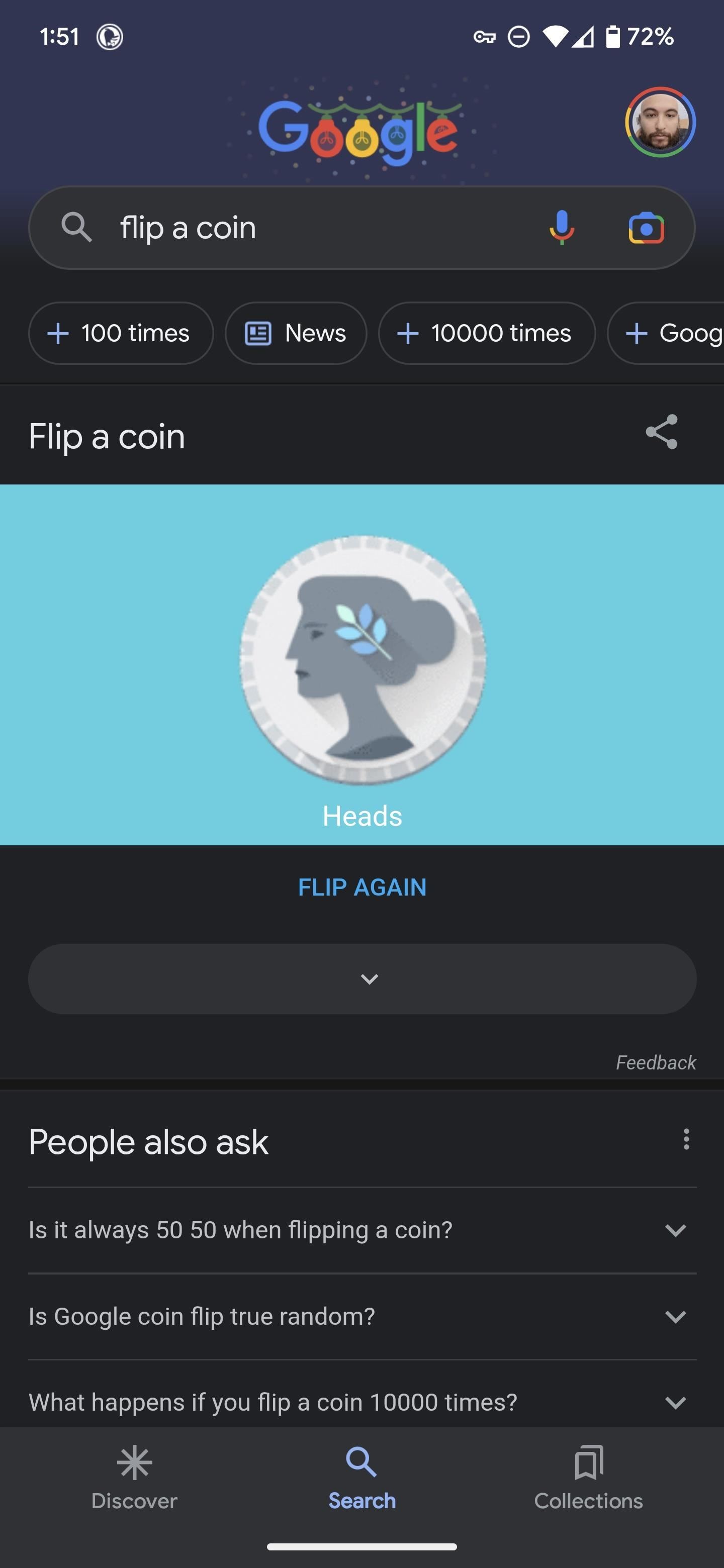
1. Flip a Coin
Search “flip a coin” to access Google’s coin. The virtual coin will spin and flip before landing on a side. Tap the “FLIP AGAIN” button to repeat.
2. Roll a Die or Set of Dice
Search Google for “roll a die” or “roll dice” to roll one six-sided die. You can also specify multiple dice and other types of dice.
There are dice with 4, 6, 8, 10, 12, and 20 sides. For example, “roll 3 d12” gives you a trio of 12-sided dice, while “roll 5 d20” gives you five 20-sided dice. Google will display the rolled dice and the resulting total number.
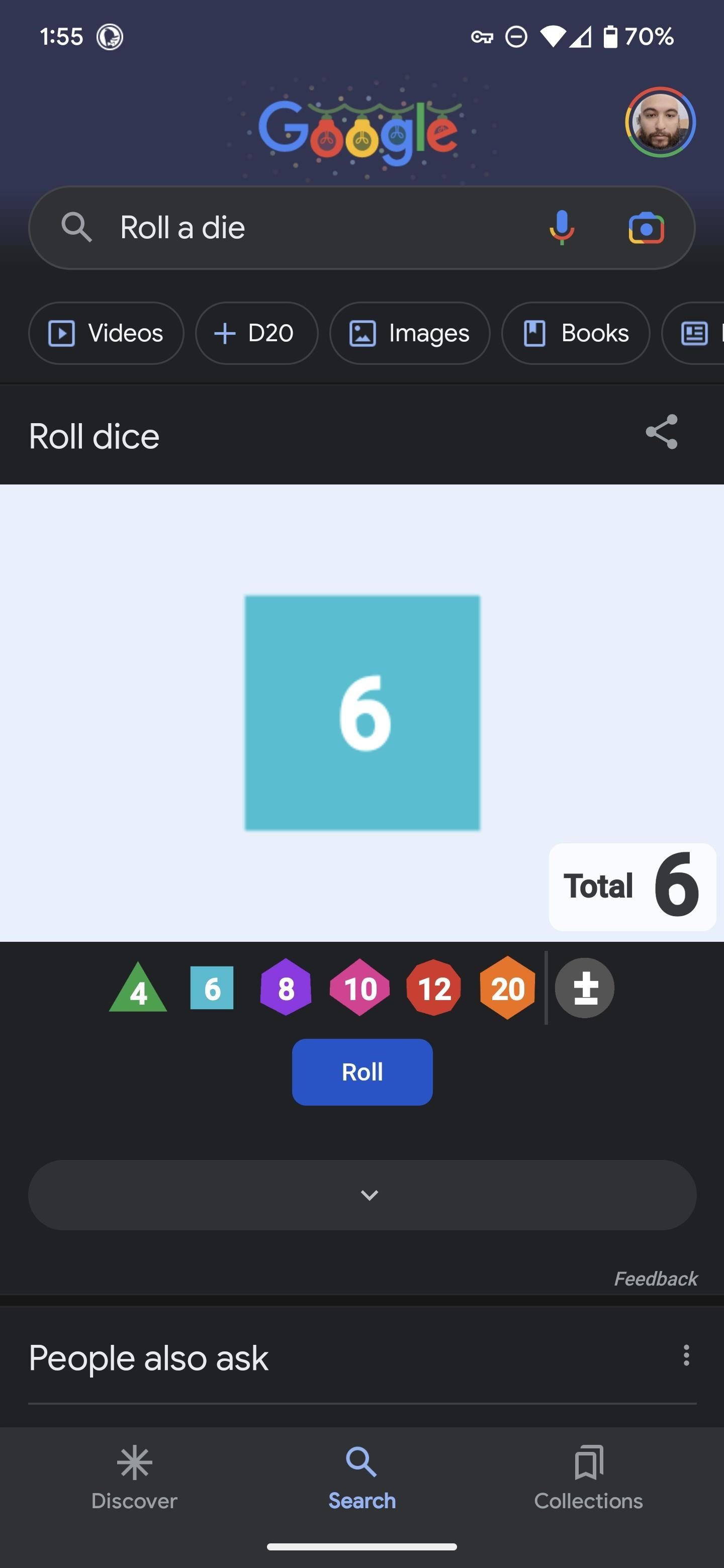
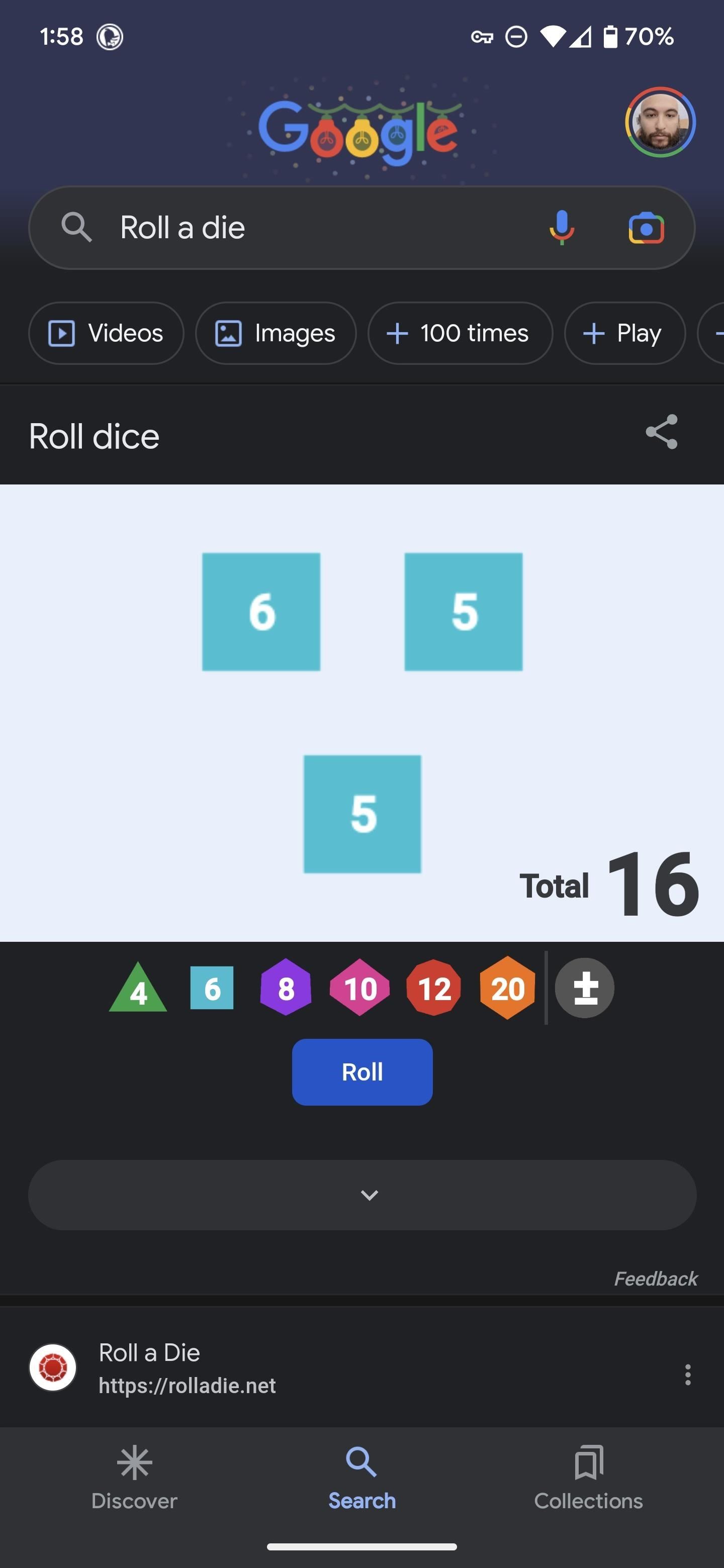
With the on-screen interface, you can tap the “Roll” button to roll the dice again. Tap the dice in the white space to clear them. In the toolbar below the white space, tap the die options to roll an additional die onto the white area. You can also tap the +/- button to add a modifier to the roll total.
3. Spinner
If you’d prefer to spin a wheel for your random number generator, Google has…