New AdLoad malware variant slips through Apple’s XProtect defenses

A new AdLoad malware variant is slipping through Apple’s YARA signature-based XProtect built-in antivirus tech to infect Macs as part of multiple campaigns tracked by American cybersecurity firm SentinelOne.
AdLoad is a widespread trojan targeting the macOS platform since at least since late 2017 and used to deploy various malicious payloads, including adware and Potentially Unwanted Applications (PUAs),
This malware can also harvest system information that later gets sent to remote servers controlled by its operators.
Increasingly active since July
These massive scale and ongoing attacks have started as early as November 2020, according to SentinelOne threat researcher Phil Stokes, with an increase in activity beginning with July and the beginning of August.
Once it infects a Mac, AdLoad will install a Man-in-The-Middle (MiTM) web proxy to hijack search engine results and inject advertisements into web pages for monetary gain.
It will also gain persistence on infected Macs by installing LaunchAgents and LaunchDaemons and, in some cases, user cronjobs that run every two and a half hours.
While monitoring this campaign, the researcher observed more than 220 samples, 150 of them unique and undetected by Apple’s built-in antivirus even though XProtect now comes with roughly a dozen AdLoad signatures.
Many of the samples detected by SentinelOne are also signed with valid Apple-issued Developer ID certificates, while others are also notarized to run under default Gatekeeper settings.
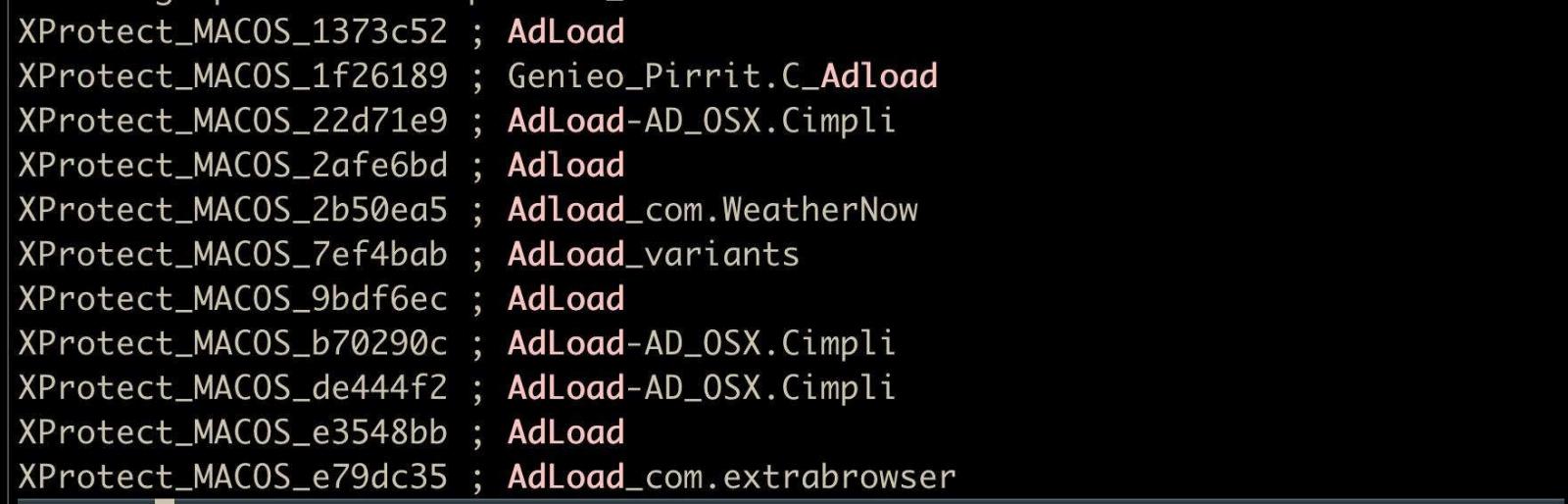
“At the time of writing, XProtect was last updated around June 15th. None of the samples we found are known to XProtect since they do not match any of the scanner’s current set of Adload rules,” Stokes concluded.
“The fact that hundreds of unique samples of a well-known adware variant have been circulating for at least 10 months and yet still remain undetected by Apple’s built-in malware scanner demonstrates the necessity of adding further endpoint security controls to Mac devices.”
Hard to ignore threat
To put things into perspective, Shlayer, another common macOS malware strain that has also been able to bypass XProtect…



