Visitors to TV station websites targeted in malvertising attack
The Angler exploit kit is once again leveraged by online criminals in an attempt to infect innocent computer users.
David Bisson reports.
The Angler exploit kit is once again leveraged by online criminals in an attempt to infect innocent computer users.
David Bisson reports.
Enlarge (credit: Malwarebytes)
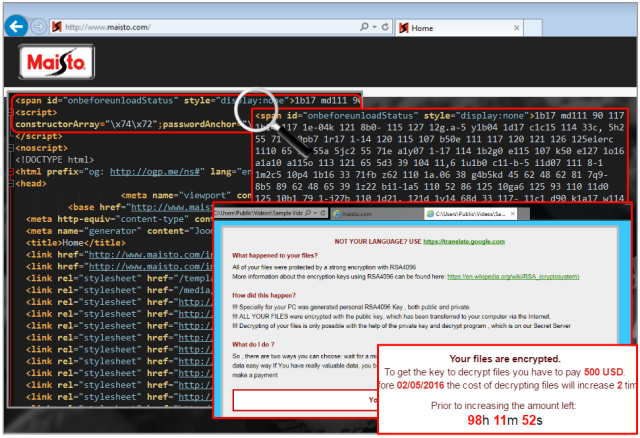
The website belonging to Maisto International, a popular maker of remote-controlled toy vehicles, has been caught pushing ransomware that holds visitors’ files hostage until they pay a hefty fee.
Malicious files provided by the Angler exploit kit were hosted directly on the homepage of Maisto[.]com, according to antivirus provider Malwarebytes. The attack code exploits vulnerabilities in older versions of applications such as Adobe Flash, Oracle Java, Silverlight, and Internet Explorer. People who visit Maisto[.]com with machines that haven’t received the latest updates are surreptitiously infected with the CryptXXX ransomware. Fortunately for victims in this case, researchers from Kaspersky Lab recently uncovered a weakness in the app that allows users to recover their files without paying the extortion demand. People infected with ransomware in other drive-by attacks haven’t been so lucky.
After discovering the infection of the Maisto homepage, Malwarebytes Senior Security Researcher Jerome Segura used this tool from website security firm Sucuri. It detected that Maisto was running an out-of-date version of the Joomla content management system, which is presumed to be the way attackers were able to load the malicious payloads on the homepage.
Attackers have hijacked thousands of websites running the WordPress content management system and are using them to infect unsuspecting visitors with potent malware exploits, researchers said Thursday.
The campaign began 15 days ago, but over the past 48 hours the number of compromised sites has spiked, from about 1,000 per day on Tuesday to close to 6,000 on Thursday, Daniel Cid, CTO of security firm Sucuri, said in a blog post. The hijacked sites are being used to redirect visitors to a server hosting attack code made available through the Nuclear exploit kit, which is sold on the black market. The server tries a variety of different exploits depending on the operating system and available apps used by the visitor.
“If you think about it, the compromised websites are just means for the criminals to get access to as many endpoint desktops as they can,” Cid wrote. “What’s the easiest way to reach out to endpoints? Websites, of course.”
In the latest attack involving malicious advertisements, hackers managed to launch Flash Player exploits against the visitors of several popular porn websites.
It’s not clear how many users were impacted, but the affected websites have over 250 million monthly visits combined, according to researchers from Malwarebytes who spotted and analyzed the attack.
The malicious ads were posted through an advertising network called AdXpansion that was abused in similar incidents in the past.
The attackers managed to distribute through the network a Flash-based ad that attempted to exploit a vulnerability in Flash Player.
The flaw affects Flash Player through version 17.0.0.134, which was released within the last two months, the Malwarebytes researchers said in a blog post Thursday. Affected sites listed in the blog post include Drtuber.com, Nuvid.com, Hardsextube.com and Justporno.tv.
To read this article in full or to leave a comment, please click here