FACTBOX-What is Volt Typhoon, the alleged China-backed hacking group?
Networks controlled by a pervasive Chinese hacking group dubbed “Volt Typhoon” have been disrupted by a U.S. government operation, Reuters exclusively reported on Monday. The group has alarmed intelligence officials who say it is part of a larger effort to compromise Western critical infrastructure, including naval ports, internet service providers and utilities, raising concerns that the hackers were working to hurt U.S. readiness in case of a Chinese invasion of Taiwan.
Here is what is known about Volt Typhoon and its potential threat: ‘FUTURE CRISES’
Nearly every country in the world uses hackers to gather intelligence. Major powers like the United States and Russia have large stables of such groups – many of which have been given colourful nicknames by cybersecurity experts, such as “Equation Group” or “Fancy Bear.” Experts begin to worry when such groups turn their attention from intelligence gathering to digital sabotage. So when Microsoft Corp said in a blog post in May last year that Volt Typhoon was “pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises,” it immediately brought to mind escalating tensions between China and the United States over Taiwan. Any conflict between those two countries would almost certainly involve cyberattacks across the Pacific.
TAIWAN BOTNET Does this mean a group of destructive hackers is preparing to sabotage U.S. infrastructure in the event of a conflict over Taiwan?
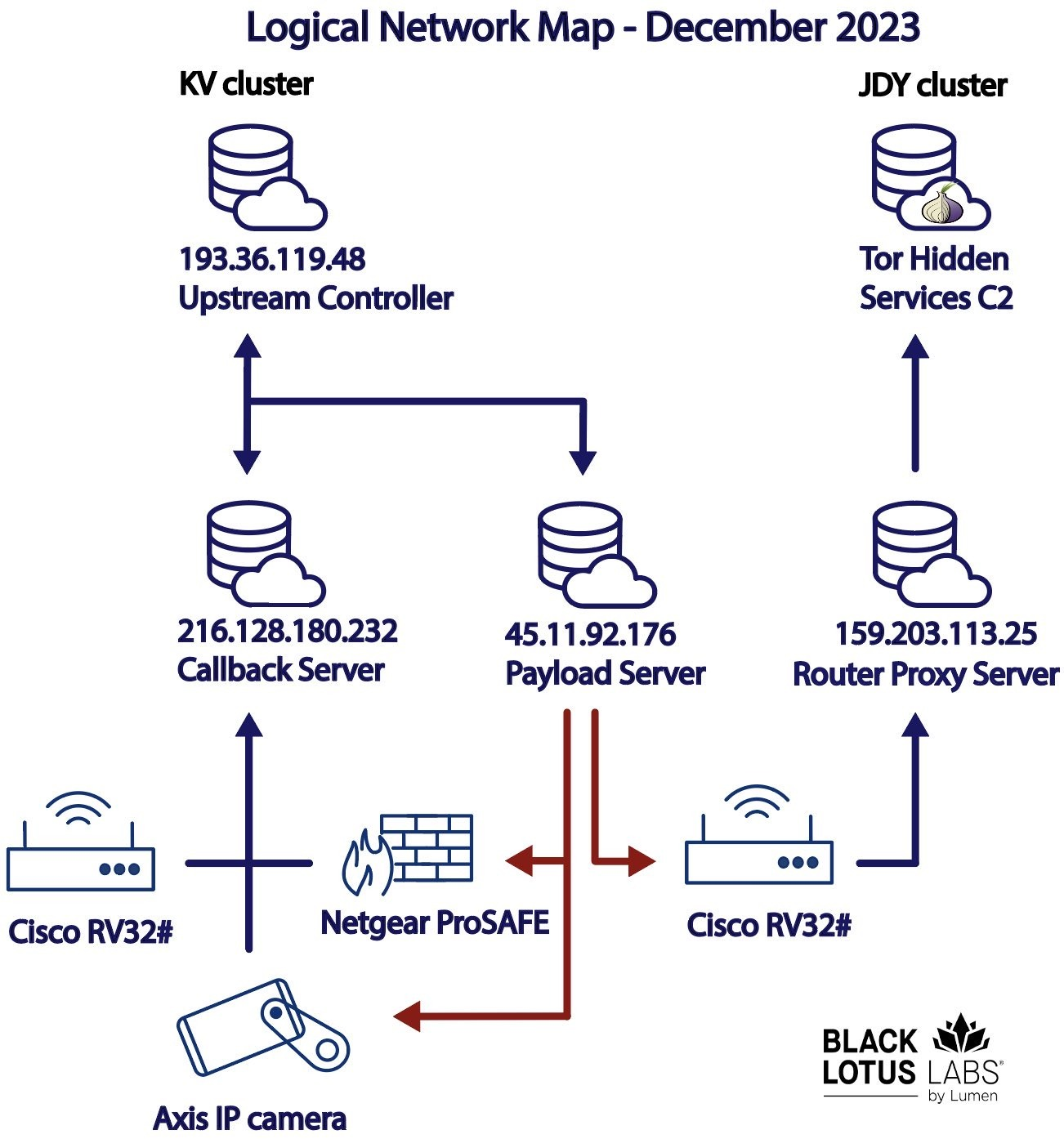
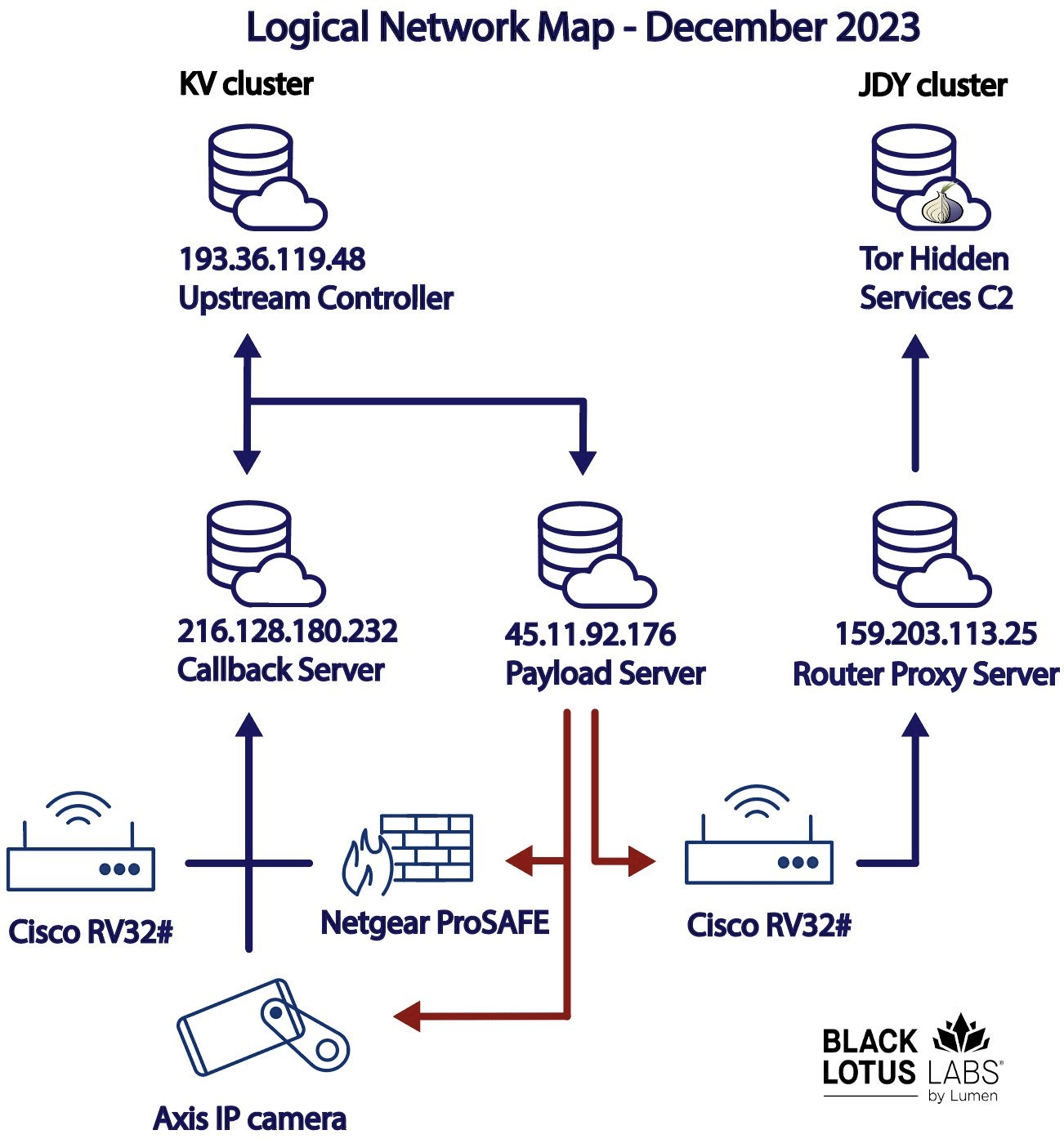
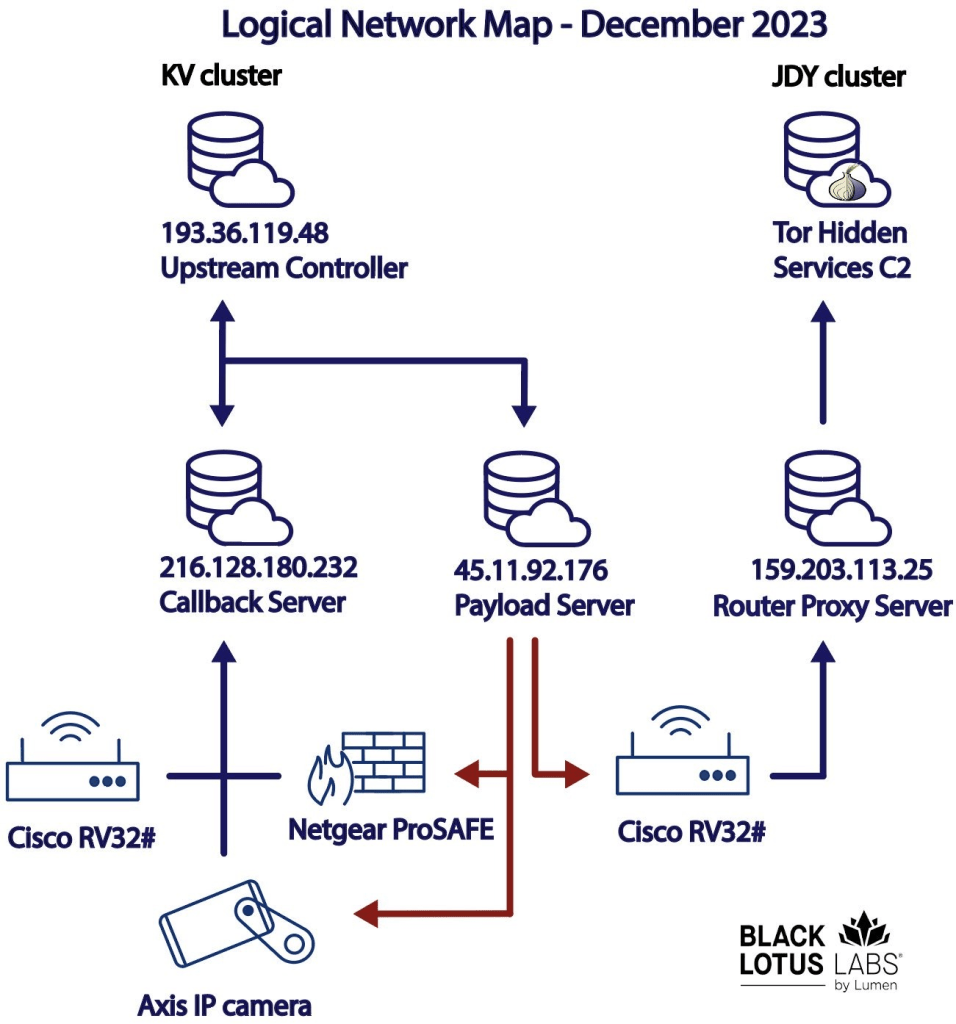
Microsoft qualified its assessment last year as “moderate confidence,” intelligence jargon that typically means a theory is plausible and credibly sourced but has yet to be fully corroborated. Different researchers have identified various aspects of the group. It is now clear that Volt Typhoon has functioned by taking control of swathes of vulnerable digital devices around the world – such as routers, modems, and even internet-connected security cameras – to hide later, downstream attacks into more sensitive targets. This constellation of remotely controlled systems, known as a botnet, is of primary concern to security officials because they limit the visibility of cyber…