Android 14 QPR1 Beta 1 seems to break Google Wallet
Google released the first beta to Android 14 QPR1 last night for Pixel phones, but eager testers should be aware that Google Wallet isn’t currently functional.
NFC payments via Google Wallet are a useful part of almost any Android phone, and with more and more merchants accepting that as a form of payment, many have come to rely on the functionality in their day to day. However, running early or rooted software can often result in the device failing to meet security requirements, and, as such, blocking Wallet from actually working.
While Android 14’s beta program largely worked with Google Wallet, that’s not the case for the first QPR1 beta.
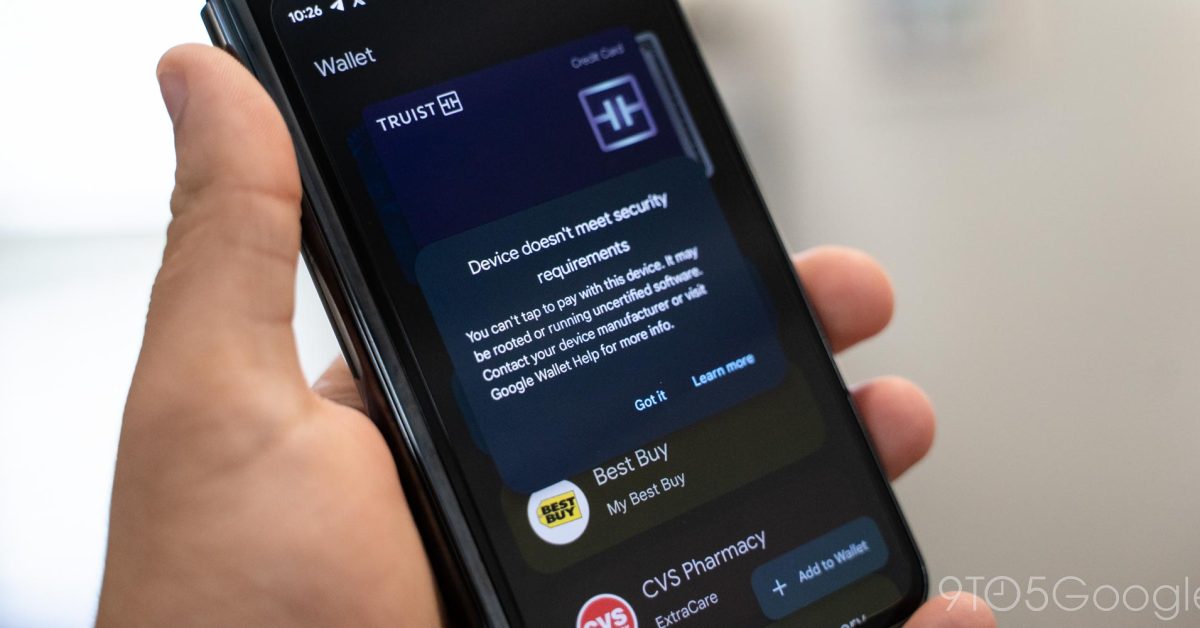
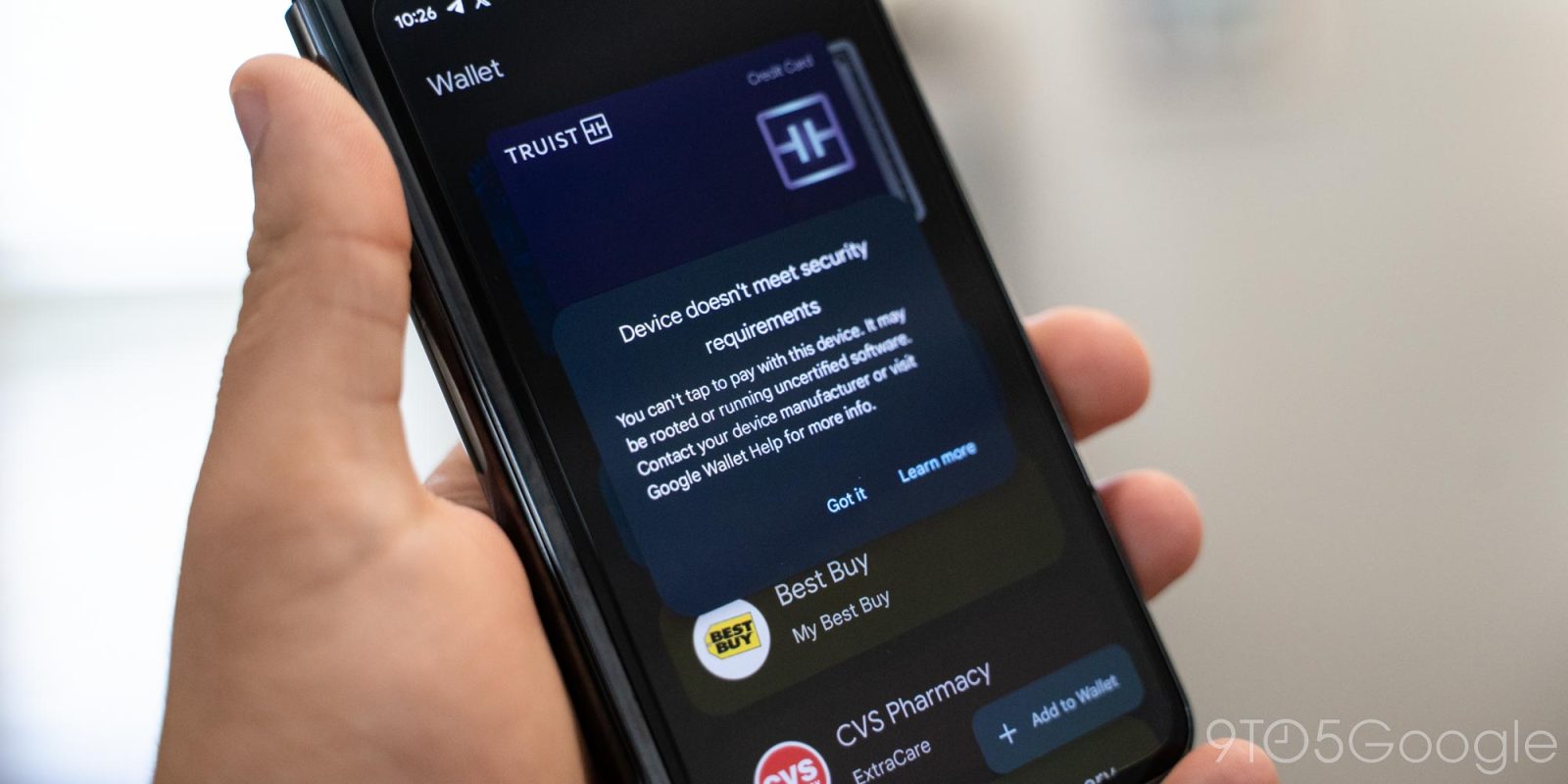
On my Pixel Fold, opening the Wallet app results in a pop-up saying that the “device doesn’t meet security requirements” and that “you can’t tap to pay with this device.” Attempting to add a new card results in a similar error.
Notably, Wallet didn’t purge any of the cards I already had set up for NFC payments on my Pixel Fold, nor does it seem to indicate that they won’t work. It only tells me that I can’t add a new card. That said, I’d guess that tap to pay would be blocked if I actually tried to use it.
Update: Shortly after this story went live, some readers chimed in that Google Wallet is still working, so your results may vary.
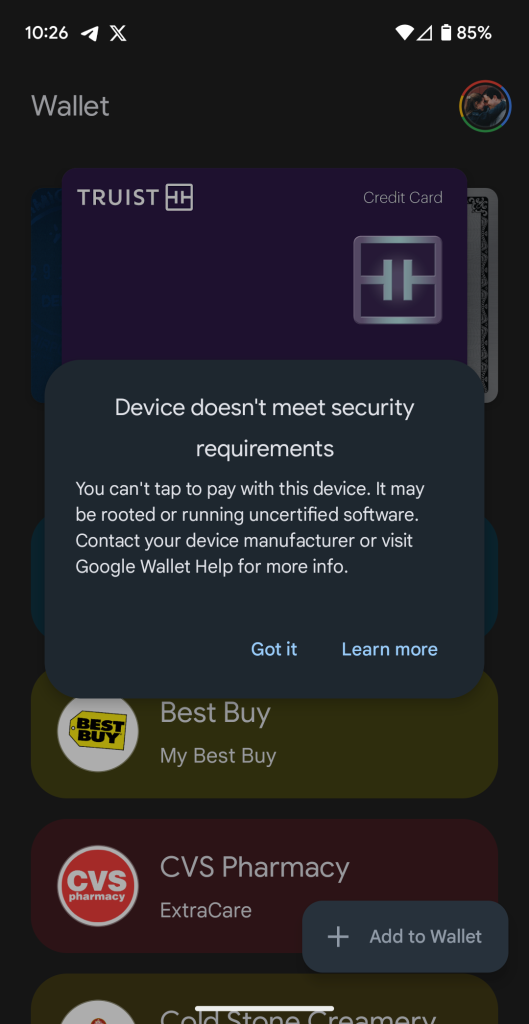
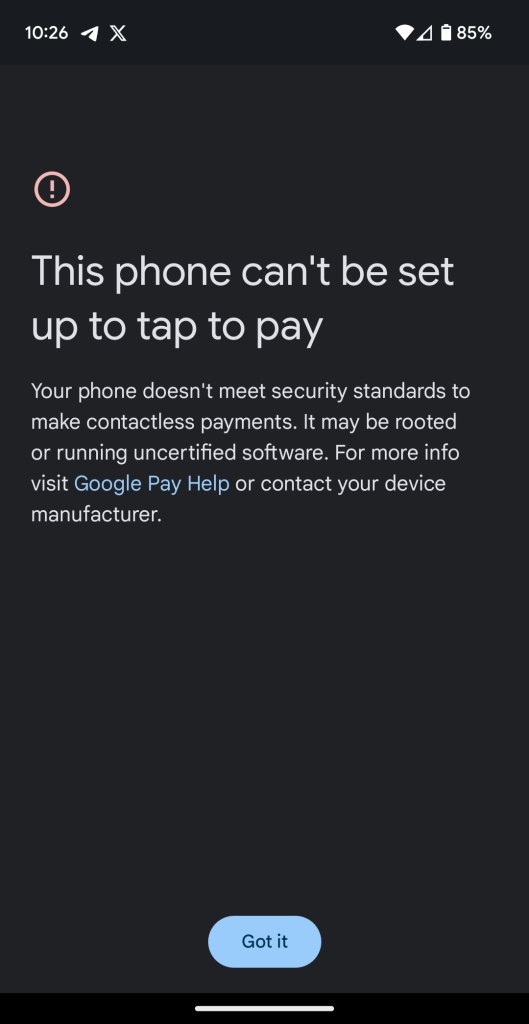
If Google Wallet payments in-store are a crucial part of your day-to-day, it’s certainly for the best that you avoid installing Android 14 QPR1, at least until this gets fixed in forthcoming updates as it usually does.
More on Android:
FTC: We use income earning auto affiliate links. More.