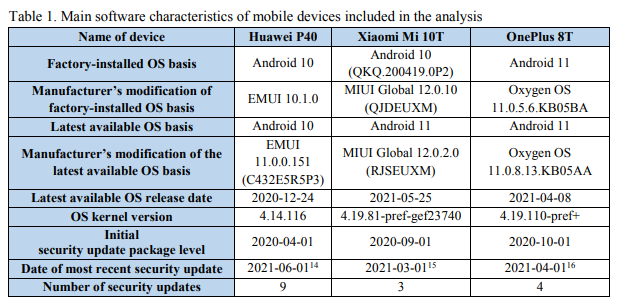
Google Chrome warnings in browser explained
Google Chrome is among the most popular web browsers. If you are a Chrome user, you might have come across some warning messages. Google Chrome displays these warning messages to alert the user that the website he is going to visit may be harmful or a security threat. In this article, we will explain some Google Chrome warnings in the browser. In some cases, these warning messages are false alarms that occur due to the expiration of the SSL certificate. But most of the time, these alert messages are genuine and you should not avoid such warnings unless you are sure that the message is a false positive flag.

What does a Google warning mean?
On the internet, there are a lot of phishing websites. By viewing the URL, one cannot identify whether the particular website is safe or malicious. That’s why Google displays different warning messages when you click on a suspicious URL accidentally in order to protect you from phishing scams and other security threats.
The different Google warning messages have different meanings. We have explained Google Chrome warnings below.
Google Chrome warnings in browser explained
When we surf on the internet, we come across a number of websites indexed on Google and other search engines. While most of these websites are trustworthy, some of them are malicious too. Malicious websites on the internet can harm users and their devices in many different ways. When a user lands on such malicious websites or downloads any content from these websites, there is a high possibility of virus or malware infection.
Some websites also trick users by displaying a message that their system is infected with a virus and offer them a free antivirus scan by installing a program on their computers. These are harmful programs that contain viruses or malware. If you install these programs, there is a high possibility that your computer will be hacked. Therefore, it is advised not to install such programs on your computer.
By default, phishing and malware detection is turned on in Google Chrome. Due to this, you may see the following messages while browsing on the internet in Chrome web browser:
- The site ahead contains malware.
- Deceptive site ahead.
- Suspicious site.
- The site ahead…