Tag Archive for: WhatsApp
How to Move WhatsApp Chats to Android, iPhone, Signal, and Telegram
/in Mobile Security
Since early 2016, WhatsApp has protected messages and conversations sent in its app with end-to-end encryption. This means that nobody other than the sender and receiver of messages can read their content—not even Meta can read or snoop on the contents of your conversations.
Despite WhatsApp being omnipresent—more than 2 billion people use it each month—securely moving your encrypted chats and photos to different platforms or apps has been a challenge. Transferring your WhatsApp chats from Android to iPhone and from iPhone to Android has historically only been possible using third-party apps. These apps are often fiddly and don’t necessarily protect your data at the level offered by WhatsApp’s ecosystem.
But in recent months WhatsApp has made it possible to officially switch between iPhones and Android (and vice versa), rolling out processes to securely move data between operating systems and working with phone manufacturers to enable the move.
If you’re fed up with Meta’s ecosystem, it’s also possible to move your groups and some chat data to other messaging apps. Here’s how to move all of your WhatsApp chats and backups.
Android to iPhone
Moving your WhatsApp account from Android to an iPhone involves a few steps. But it should be possible to bring most of your information with you: Your profile photo, individual and group chats, history, photos, videos, and settings can all make the jump from one device to another. Your call history and display name can’t be moved across, however, WhatsApp says.
Most of the work in moving your WhatsApp data comes before you make the shift. To move between devices, you need to ensure you have the same phone number on each. Before you start the process, make sure you have a recently updated version of WhatsApp on your Android phone. You also need to be running at least Android 5 on the device you’re moving from and iOS 15.5 on the iPhone you’re moving to. (The iPhone needs to be a new device or have been recently reset to its factory settings.)
Next, download and install the “Move to iOS” app from Google’s Play Store—this Apple-owned app will do all the heavy lifting. When you’re ready to migrate your data, plug both…
WhatsApp to introduce a second OTP to log into account on new device: Report
/in Mobile Security
WhatsApp is planning on introducing a feature that will add an extra layer of security before a user is allowed to log in to a WhatsApp account, according to WABetaInfo. The feature is expected to be rolled out to beta versions of the instant messaging app for iOS and Android in the future.
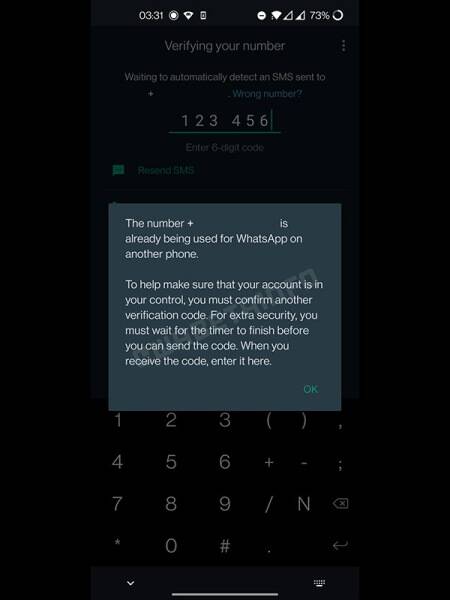
After reportedly testing a feature that would allow users to undo message deletion, WhatsApp could soon begin asking for a double verification code. This would mean that if you tried to log in to WhatsApp on a new phone, you will need an additional verification code apart from the first one sent by SMS.
“The number +********** is already being used for WhatsApp on another phone. To help make sure that your account is in your control, you must confirm another verification code. For extra security, you must wait for the timer to finish before you can send the code. When you receive the code, enter it here.” says a screenshot obtained by WABetaInfo.
 (Image credit: WABetaInfo)
(Image credit: WABetaInfo)
This feature is reportedly being announced to prevent users’ WhatsApp accounts being stolen or hacked, as has happened in the past. Such scams typically happen when users share the OTP that WhatsApp sent them with a bad actor, who can use it to take over the WhatsApp account.
This new security feature could be aimed at protecting people who unwittingly share their 6-digit OTP unwittingly. Once the feature is released, a second 6-digit code will be sent to the user’s phone number after a time delay. The message with the OTP will tell the user that someone is attempting to log into their account, and ideally, this should mean that users won’t share the second 6-digit code.
ESET Research: Lazarus attacks aerospace and defense contractors worldwide while misusing LinkedIn and WhatsApp
/in Mobile Security
DUBAI, UNITED ARAB EMIRATES, June 1, 2022 /EINPresswire.com/ — During the annual ESET World conference, ESET researchers have been presenting about a new investigation into the infamous Lazarus APT group. Director of ESET Threat Research Jean-Ian Boutin went over various new campaigns perpetrated by the Lazarus group against defense contractors around the world between late 2021 and March 2022.
In the relevant 2021-2022 attacks and according to ESET telemetry, Lazarus has been targeting companies in Europe (France, Italy, Germany, the Netherlands, Poland, and Ukraine) and Latin America (Brazil).
Despite the primary aim of this Lazarus operation being cyber-espionage, the group has also worked to exfiltrate money (unsuccessfully). “The Lazarus threat group showed ingenuity by deploying an interesting toolset, including for example a user mode component able to exploit a vulnerable Dell driver in order to write to kernel memory. This advanced trick was used in an attempt to bypass security solutions monitoring.,” says Jean-Ian Boutin.
As early as 2020, ESET researchers had already documented a campaign pursued by a sub-group of Lazarus against European aerospace and defense contractors ESET called operation In(ter)ception. This campaign was noteworthy as it used social media, especially LinkedIn, to build trust between the attacker and an unsuspecting employee before sending them malicious components masquerading as job descriptions or applications. At that time, companies in Brazil, Czech Republic, Qatar, Turkey and Ukraine had already been targeted.
ESET researchers believed that the action was mostly geared towards attacking European companies, but through tracking a number of Lazarus sub-groups performing similar campaigns against defense contractors, they soon realized that the campaign extended much wider. While the malware used in the various campaigns were different, the initial modus operandi (M.O.) always remained the same: a fake recruiter contacted an employee through LinkedIn and eventually sent malicious components.
In this regard, they’ve continued with the same M.O. as in the past. However, ESET researchers have also…