“You’re under arrest for possession of an insecure phone” – 60 Sec Security [VIDEO]
Here’s this week’s 60 Second Security video. News you can use in a format you can enjoy…all in 60 seconds!
Naked Security – Sophos
Here’s this week’s 60 Second Security video. News you can use in a format you can enjoy…all in 60 seconds!
Naked Security – Sophos
What businesses know about any given individual is a lot. But what are companies doing with that data? Not as much as you might think — at least not yet. Companies are getting more sophisticated, however.
The trove of data that’s out there includes:
Traditional offline data gathered by credit bureaus and data aggregators, including public data from telephone directories, court and property records
User account data collected and retained by businesses with which consumers have purchased products or registered for services
Data from online activity including searches, social media profiles and tweets, mobile app activity and Web browsing habits
To read this article in full or to leave a comment, please click here
|
Wolverton: If you're running Android, watch out for malware
San Jose Mercury News Google screens the apps in its store for malicious code, and Android users can now have Google remotely screen apps on their phone that were downloaded elsewhere, said Adrian Ludwing, an Android security engineer at Google. Thanks to that service and … |
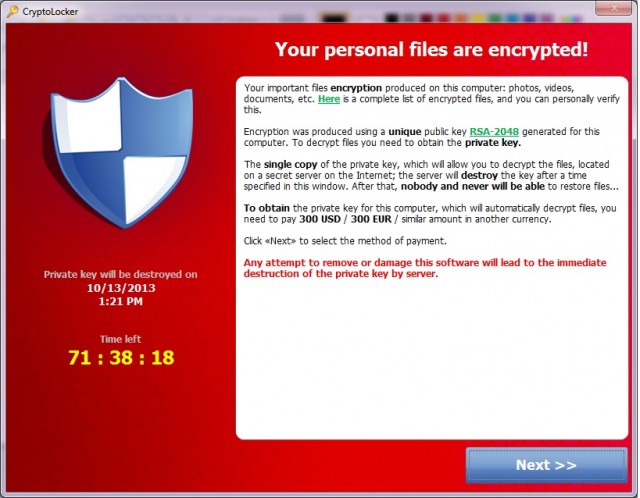
Malware that takes computers hostage until users pay a ransom is getting meaner, and thanks to the growing prevalence of Bitcoin and other digital payment systems, it’s easier than ever for online crooks to capitalize on these “ransomware” schemes. If this wasn’t already abundantly clear, consider the experience of Nic, an Ars reader who fixes PCs for a living and recently helped a client repair the damage inflicted by a particularly nasty title known as CryptoLocker.
It started when an end user in the client’s accounting department received an e-mail purporting to come from Intuit. Yes, the attached archived zip file with an executable inside should have been a dead giveaway that this message was malicious and was in no way affiliated with Intuit. But accounting employees are used to receiving e-mails from financial companies. When the receiver clicked on it, he saw a white box flash briefly on his screen but didn’t notice anything else out of the ordinary. He then locked his computer and attended several meetings.
Within a few hours, the company’s IT department received word of a corrupt file stored on a network drive that was available to multiple employees, including the one who received the malicious e-mail. A quick investigation soon uncovered other corrupted files, most or all of which had been accessed by the accounting employee. By the time CryptoLocker had run its course, hundreds of gigabytes worth of company data was no longer available.
Read 10 remaining paragraphs | Comments
![]()
     |